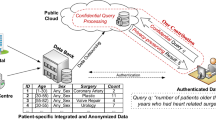
Abstract
Outsourcing data in the cloud has become nowadays very common. Since – generally speaking – cloud data storage and management providers cannot be fully trusted, mechanisms providing the confidentiality of the stored data are necessary. A possible solution is to encrypt all the data, but – of course – this poses serious problems about the effective usefulness of the stored data. In this work, we propose to apply a well-known attribute-based cryptographic scheme to cope with the problem of querying encrypted data. We have implemented the proposed scheme with a real-world, off-the-shelf RDBMS and we provide several experimental results showing the feasibility of our approach.
Access this chapter
Tax calculation will be finalised at checkout
Purchases are for personal use only
Preview
Unable to display preview. Download preview PDF.
Similar content being viewed by others
References
Katz, J., Sahai, A., Waters, B.: Predicate encryption supporting disjunctions, polynomial equations, and inner products. J. Cryptology 26(2), 191–224 (2013)
Okamoto, T., Takashima, K.: Adaptively attribute-hiding (hierarchical) inner product encryption. In: Pointcheval, D., Johansson, T. (eds.) EUROCRYPT 2012. LNCS, vol. 7237, pp. 591–608. Springer, Heidelberg (2012)
Samarati, P., de Capitani di Vimercati, S.: Data protection in outsourcing scenarios: issues and directions. In: Proceedings of the 5th ACM Symposium on Information, Computer and Communications Security (ASIACCS), Beijing, China, pp. 1–14 (2010)
Davida, G.I., Wells, D.L., Kam, J.B.: A database encryption system with subkeys. ACM Trans. Database Syst. 6(2), 312–328 (1981)
Bayer, R., Metzger, J.K.: On the encipherment of search trees and random access files. ACM Trans. Database Syst. 1(1), 37–52 (1976)
Hacigümüs, H., Iyer, B.R., Li, C., Mehrotra, S.: Executing sql over encrypted data in the database-service-provider model. In: Proceedings of the ACM SIGMOD Conference on Management of Data, pp. 216–227 (2002)
Bajaj, S., Sion, R.: Trusteddb: A trusted hardware based outsourced database engine. PVLDB 4(12), 1359–1362 (2011)
Popa, R.A., Redfield, C.M.S., Zeldovich, N., Balakrishnan, H.: Cryptdb: protecting confidentiality with encrypted query processing. In: Proceedings of the 23rd ACM Symposium on Operating Systems Principles (SOSP), pp. 85–100 (2011)
Corp. Oracle: Oracle advences security transparent data encryption best practices. White paper (2012)
Shmueli, E., Vaisenberg, R., Elovici, Y., Glezer, C.: Database encryption: an overview of contemporary challenges and design considerations. SIGMOD Record 38(3), 29–34 (2009)
Bouganim, L., Guo, Y.: Database encryption. In: Encyclopedia of Cryptography and Security, 2nd edn., pp. 307–312 (2011)
Gentry, C.: Fully homomorphic encryption using ideal lattices. In: Proceedings of the 41st Annual ACM Symposium on Theory of Computing, STOC 2009, Bethesda, MD, USA, pp. 169–178 (2009)
Boneh, D., Di Crescenzo, G., Ostrovsky, R., Persiano, G.: Public key encryption with keyword search. In: Cachin, C., Camenisch, J.L. (eds.) EUROCRYPT 2004. LNCS, vol. 3027, pp. 506–522. Springer, Heidelberg (2004)
Boneh, D., Waters, B.: Conjunctive, subset, and range queries on encrypted data. In: Vadhan, S.P. (ed.) TCC 2007. LNCS, vol. 4392, pp. 535–554. Springer, Heidelberg (2007)
Boneh, D., Gentry, C., Halevi, S., Wang, F., Wu, D.J.: Private database queries using somewhat homomorphic encryption. In: Jacobson, M., Locasto, M., Mohassel, P., Safavi-Naini, R. (eds.) ACNS 2013. LNCS, vol. 7954, pp. 102–118. Springer, Heidelberg (2013)
Zheng, Q., Xu, S., Ateniese, G.: Vabks: Verifiable attribute-based keyword search over outsourced encrypted data. IACR Cryptology ePrint Archive 2013 (2013)
Samarati, P., de Capitani di Vimercati, S.: Access control: Policies, models, and mechanisms. In: Focardi, R., Gorrieri, R. (eds.) FOSAD 2000. LNCS, vol. 2171, pp. 137–196. Springer, Heidelberg (2001)
Bangerter, E., Camenisch, J., Lysyanskaya, A.: A cryptographic framework for the controlled release of certified data. In: Christianson, B., Crispo, B., Malcolm, J.A., Roe, M. (eds.) Security Protocols 2004. LNCS, vol. 3957, pp. 20–42. Springer, Heidelberg (2006)
Camenisch, J., Dubovitskaya, M., Lehmann, A., Neven, G., Paquin, C., Preiss, F.-S.: Concepts and languages for privacy-preserving attribute-based authentication. In: Fischer-Hübner, S., de Leeuw, E., Mitchell, C. (eds.) IDMAN 2013. IFIP AICT, vol. 396, pp. 34–52. Springer, Heidelberg (2013)
Gasarch, W.I.: A survey on private information retrieval (column: Computational complexity). Bulletin of the EATCS 82, 72–107 (2004)
Iovino, V., Persiano, G.: Hidden-vector encryption with groups of prime order. In: Galbraith, S.D., Paterson, K.G. (eds.) Pairing 2008. LNCS, vol. 5209, pp. 75–88. Springer, Heidelberg (2008)
Author information
Authors and Affiliations
Corresponding author
Editor information
Editors and Affiliations
Rights and permissions
Copyright information
© 2014 Springer International Publishing Switzerland
About this paper
Cite this paper
Trombetta, A., Persiano, G., Braghin, S. (2014). Processing Private Queries over an Obfuscated Database Using Hidden Vector Encryption. In: Bernsmed, K., Fischer-Hübner, S. (eds) Secure IT Systems. NordSec 2014. Lecture Notes in Computer Science(), vol 8788. Springer, Cham. https://doi.org/10.1007/978-3-319-11599-3_6
Download citation
DOI: https://doi.org/10.1007/978-3-319-11599-3_6
Publisher Name: Springer, Cham
Print ISBN: 978-3-319-11598-6
Online ISBN: 978-3-319-11599-3
eBook Packages: Computer ScienceComputer Science (R0)