Abstract
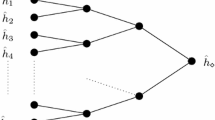
We consider a situation where the adversary performs a second preimage attack and is able to influence slightly the preconditions under which the iterated hash function is used. In the first variant of the attack, the adversary is able to choose the initial value of the hash function after receiving the original message. In the second variant, the adversary is allowed to determine a prefix of the original message and has to create a second preimage with the same prefix. Both of these attacks use diamond structures and the expected number of compression function calls required to complete each of them successfully is in \(\mathrm O(\sqrt{n} \cdot 2^{\frac{2n}{3}})\) while on random oracle hash function it is in \(\mathrm O(2^n)\). We also show that it is possible to decrease the before mentioned expected value to \(\mathrm O(2^{\frac{2n-l}{3}})\) if the length of the original message is 2l and l is sufficiently large. Furthermore, we generalize these attacks to work against concatenated hash functions as well.
Access this chapter
Tax calculation will be finalised at checkout
Purchases are for personal use only
Preview
Unable to display preview. Download preview PDF.
Similar content being viewed by others
References
Andreeva, E., Bouillaguet, C., Dunkelman, O., Kelsey, J.: Herding, second preimage and Trojan message attacks beyond Merkle-Damgård. In: Jacobson Jr., M.J., Rijmen, V., Safavi-Naini, R. (eds.) SAC 2009. LNCS, vol. 5867, pp. 393–414. Springer, Heidelberg (2009)
Andreeva, E., Bouillaguet, C., Fouque, P.-A., Hoch, J.J., Kelsey, J., Shamir, A., Zimmer, S.: Second preimage attacks on dithered hash functions. In: Smart, N.P. (ed.) EUROCRYPT 2008. LNCS, vol. 4965, pp. 270–288. Springer, Heidelberg (2008)
Blackburn, S., Stinson, D., Upadhyay, J.: On the complexity of the herding attack and some related attacks on hash functions. Designs, Codes and Cryptography 64(1-2), 171–193 (2012)
Coron, J.-S., Dodis, Y., Malinaud, C., Puniya, P.: Merkle-Damgård revisited: How to construct a hash function. In: Shoup, V. (ed.) CRYPTO 2005. LNCS, vol. 3621, pp. 430–448. Springer, Heidelberg (2005)
Damgård, I.B.: A design principle for hash functions. In: Brassard, G. (ed.) CRYPTO 1989. LNCS, vol. 435, pp. 416–427. Springer, Heidelberg (1990)
Dean, R.: Formal aspects of mobile code security. PhD thesis, Princeton University (1999)
Dobbertin, H.: Cryptanalysis of MD4. Journal of Cryptology 11(4), 253–271 (1998)
Hoch, J.J., Shamir, A.: Breaking the ICE - finding multicollisions in iterated concatenated and expanded (ICE) hash functions. In: Robshaw, M. (ed.) FSE 2006. LNCS, vol. 4047, pp. 179–194. Springer, Heidelberg (2006)
Joux, A.: Multicollisions in iterated hash functions. Application to cascaded constructions. In: Franklin, M. (ed.) CRYPTO 2004. LNCS, vol. 3152, pp. 306–316. Springer, Heidelberg (2004)
Kelsey, J., Kohno, T.: Herding hash functions and Nostradamus attack. In: Vaudenay, S. (ed.) EUROCRYPT 2006. LNCS, vol. 4004, pp. 183–200. Springer, Heidelberg (2006)
Kelsey, J., Schneier, B.: Second preimage on n-bit hash functions for much less than 2n work. In: Cramer, R. (ed.) EUROCRYPT 2005. LNCS, vol. 3494, pp. 474–490. Springer, Heidelberg (2005)
Klima, V.: Finding MD5 collisions on a notebook PC using multi-message modifications, Cryptology ePrint Archive, Report 2005/102 (2005), http://eprint.iacr.org/2005/102
Klima, V.: Huge multicollisions and multipreimages of hash functions BLENDER-n, Cryptology ePrint Archive, Report 2009/006 (2009), http://eprint.iacr.org/2009/006
Kortelainen, J., Halunen, K., Kortelainen, T.: Multicollision attacks and generalized iterated hash functions. J. Math. Cryptol. 4, 239–270 (2010)
Kortelainen, J., Kortelainen, T., Vesanen, A.: Unavoidable regularities in long words with bounded number of symbol occurrences. In: Fu, B., Du, D.-Z. (eds.) COCOON 2011. LNCS, vol. 6842, pp. 519–530. Springer, Heidelberg (2011)
Kortelainen, J., Kortelainen, T., Vesanen, A.: Unavoidable regularities in long words with bounded number of symbol occurrences. J. Comp. Optim. 26, 670–686 (2013)
Kortelainen, T., Kortelainen, J., Halunen, K.: Variants of multicollision attacks on iterated hash functions. In: Lai, X., Yung, M., Lin, D. (eds.) Inscrypt 2010. LNCS, vol. 6584, pp. 139–154. Springer, Heidelberg (2011)
Kortelainen, T., Vesanen, A., Kortelainen, J.: Generalized iterated hash functions revisited: New complexity bounds for multicollision attacks. In: Galbraith, S., Nandi, M. (eds.) INDOCRYPT 2012. LNCS, vol. 7668, pp. 172–190. Springer, Heidelberg (2012)
Kortelainen, T., Kortelainen, J.: On diamond structures and Trojan message attacks. In: Sako, K., Sarkar, P. (eds.) ASIACRYPT 2013, Part II. LNCS, vol. 8270, pp. 524–539. Springer, Heidelberg (2013)
Menezes, A., van Oorschot, P., Vanstone, S. (eds.): Handbook of Applied Cryptography, pp. 321–376. CRC Press (1996)
Merkle, R.C.: One way hash functions and DES. In: Brassard, G. (ed.) CRYPTO 1989. LNCS, vol. 435, pp. 428–446. Springer, Heidelberg (1990)
Nandi, M., Stinson, D.: Multicollision attacks on some generalized sequential hash functions. IEEE Trans. Inform. Theory 53, 759–767 (2007)
Stevens, M.: Fast collision attack on MD5, Cryptology ePrint Archive, Report 2006/104 (2006), http://eprint.iacr.org/2006/104
Wang, X., Yu, H.: How to break MD5 and other hash functions. In: Cramer, R. (ed.) EUROCRYPT 2005. LNCS, vol. 3494, pp. 19–35. Springer, Heidelberg (2005)
Wang, X., Yin, Y.L., Yu, H.: Finding collisions in the full SHA-1. In: Shoup, V. (ed.) CRYPTO 2005. LNCS, vol. 3621, pp. 17–36. Springer, Heidelberg (2005)
Yu, H., Wang, X.: Multi-collision attack on the compression functions of MD4 and 3-pass HAVAL. In: Nam, K.-H., Rhee, G. (eds.) ICISC 2007. LNCS, vol. 4817, pp. 206–226. Springer, Heidelberg (2007)
Author information
Authors and Affiliations
Editor information
Editors and Affiliations
Rights and permissions
Copyright information
© 2014 Springer International Publishing Switzerland
About this paper
Cite this paper
Kortelainen, T., Kortelainen, J. (2014). New Second Preimage Attack Variants against the MD-Structure. In: Gritzalis, D., Kiayias, A., Askoxylakis, I. (eds) Cryptology and Network Security. CANS 2014. Lecture Notes in Computer Science, vol 8813. Springer, Cham. https://doi.org/10.1007/978-3-319-12280-9_7
Download citation
DOI: https://doi.org/10.1007/978-3-319-12280-9_7
Publisher Name: Springer, Cham
Print ISBN: 978-3-319-12279-3
Online ISBN: 978-3-319-12280-9
eBook Packages: Computer ScienceComputer Science (R0)