Abstract
In this paper, we formulate a three-player three-stage Colonel Blotto game, in which two players fight against a common adversary. We assume that the game is one of complete information, that is, the players have complete and consistent information on the underlying model of the game; further, each player observes the actions taken by all players up to the previous stage. The setting under consideration is similar to the one considered in our recent work [1], but with a different information structure during the second stage of the game; this leads to a significantly different solution.
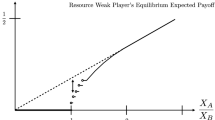
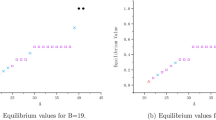
In the first stage, players can add additional battlefields. In the second stage, the players (except the adversary) are allowed to transfer resources among each other if it improves their expected payoffs, and simultaneously, the adversary decides on the amount of resource it allocates to the battle with each player subject to its resource constraint. At the third stage, the players and the adversary fight against each other with updated resource levels and battlefields. We compute the subgame-perfect Nash equilibrium for this game. Further, we show that when playing according to the equilibrium, there are parameter regions in which (i) there is a net positive transfer, (ii) there is absolutely no transfer, (iii) the adversary fights with only one player, and (iv) adding battlefields is beneficial to a player. In doing so, we also exhibit a counter-intuitive property of Nash equilibrium in games: extra information to a player in the game does not necessarily lead to a better performance for that player. The result finds application in resource allocation problems for securing cyber-physical systems.
Access this chapter
Tax calculation will be finalised at checkout
Purchases are for personal use only
Preview
Unable to display preview. Download preview PDF.
Similar content being viewed by others
References
Gupta, A., Schwartz, G., Langbort, C., Sastry, S.S., Başar, T.: A three-stage Colonel Blotto game with applications to cyberphysical security. In: Proc. 2014 American Control Conference (ACC), pp. 3832–3837 (June 2014)
Borel, E., Ville, J.: Applications de la théorie des probabilités aux jeux de hasard. J. Gabay (1938)
Gross, O., Wagner, R.: A continuous Colonel Blotto game. RAND Project No. RM-408, Santa Monica, CA (June 1950)
Roberson, B.: The Colonel Blotto game. Economic Theory 29(1), 1–24 (2006)
Kvasov, D.: Contests with limited resources. Journal of Economic Theory 136(1), 738–748 (2007)
Kovenock, D., Mauboussin, M.J., Roberson, B.: Asymmetric conflicts with endogenous dimensionality. Korean Economic Review 26, 287–305 (2010)
Kovenock, D., Roberson, B.: Coalitional Colonel Blotto games with application to the economics of alliances. Journal of Public Economic Theory 14(4), 653–676 (2012)
Chia, P.H., Chuang, J.: Colonel Blotto in the phishing war. In: Baras, J.S., Katz, J., Altman, E. (eds.) GameSec 2011. LNCS, vol. 7037, pp. 201–218. Springer, Heidelberg (2011)
Chia, P.H.: Colonel Blotto in web security. In: The Eleventh Workshop on Economics and Information Security, WEIS Rump Session (2012)
Arad, A., Rubinstein, A.: Colonel Blotto’s top secret files. Levine’s Working Paper Archive 926159280 (2009)
Arad, A., Rubinstein, A.: Colonel Blotto’s top secret files: Multi-dimensional iterative reasoning in action. Tech. rep., Working paper (2010)
Kohli, P., Kearns, M., Bachrach, Y., Herbrich, R., Stillwell, D., Graepel, T.: Colonel Blotto on Facebook: The effect of social relations on strategic interaction. In: Proceedings of the 3rd Annual ACM Web Science Conference, WebSci 2012, pp. 141–150. ACM, New York (2012)
Fudenberg, D., Tirole, J.: Game Theory. MIT Press (1991)
Gupta, A., Schwartz, G., Langbort, C., Sastry, S.S., Başar, T.: A three-stage Colonel Blotto game with applications to cyberphysical security. Tech. Rep. UCB/EECS-2014-19. EECS Department, University of California, Berkeley (March 2014), http://www.eecs.berkeley.edu/Pubs/TechRpts/2014/EECS-2014-19.html
Başar, T., Ho, Y.-C.: Informational properties of the Nash solutions of two stochastic nonzero-sum games. Journal of Economic Theory 7(4), 370–387 (1974)
Author information
Authors and Affiliations
Editor information
Editors and Affiliations
Rights and permissions
Copyright information
© 2014 Springer International Publishing Switzerland
About this paper
Cite this paper
Gupta, A., Başar, T., Schwartz, G.A. (2014). A Three-Stage Colonel Blotto Game: When to Provide More Information to an Adversary. In: Poovendran, R., Saad, W. (eds) Decision and Game Theory for Security. GameSec 2014. Lecture Notes in Computer Science, vol 8840. Springer, Cham. https://doi.org/10.1007/978-3-319-12601-2_12
Download citation
DOI: https://doi.org/10.1007/978-3-319-12601-2_12
Publisher Name: Springer, Cham
Print ISBN: 978-3-319-12600-5
Online ISBN: 978-3-319-12601-2
eBook Packages: Computer ScienceComputer Science (R0)