Abstract
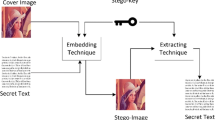
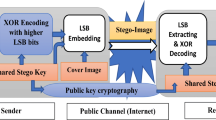
An efficient 2-step steganography technique is proposed to enhance stego image quality and secret message un-detectability. The first step is a pre-processing algorithm that reduces the size of secret images without losing information. This results in improved stego image quality compared to other existing image steganography methods. The proposed secret image size reduction (SISR) algorithm is an efficient spatial domain technique. The second step is an embedding mechanism that relies on Fibonacci representation of pixel intensities to minimize the effect of embedding on the stego image quality. The improvement is attained by using bit-plane(s) mapping instead of bit-plane(s) replacement for embedding. The proposed embedding mechanism outperforms the binary based LSB randomly embedding in two ways: reduced effect on stego quality and increased robustness against statistical steganalysers. Experimental results demonstrate the benefits of the proposed scheme in terms of: 1) SISR ratio (indirectly results in increased capacity); 2) quality of the stego; and 3) robustness against steganalysers such as RS, and WS. Furthermore, experimental results show that the proposed SISR algorithm can be extended to be applicable on DICOM standard medical images. Future security standardization research is proposed that would focus on evaluating the security, performance, and effectiveness of steganography algorithms.
Access this chapter
Tax calculation will be finalised at checkout
Purchases are for personal use only
Preview
Unable to display preview. Download preview PDF.
Similar content being viewed by others
References
Mildenberger, P., Eichelberg, M., Martin, E.: Introduction to the DICOM standard. European Radiology 12, 920–927 (2002)
Gibaud, B.: The Dicom Standard: A Brief Overview. In: Molecular Imaging: Computer Reconstruction and Practice, pp. 229–238. Springer (2008)
Chan, C., Cheng, L.M.: Hiding data in images by simple LSB substitution. Pattern Recognition 37, 469–474 (2004)
Thien, C., Lin, J.: A simple and high-hiding capacity method for hiding digit-by-digit data in images based on modulus function. Pattern Recognition 362, 875 (2003)
Picione, D.D.L., Battisti, F., Carli, M., Astola, J., Egiazarian, K.: A Fibonacci LSB data hiding technique. In: Proc. 14th EUSIPCO (2006)
Fridrich, J., Goljan, M., Du, R.: Reliable detection of LSB steganography in color and grayscale images. In: Proc. ACM Workshop on Multimedia and Security, pp. 27–30 (2001)
Fridrich, J., Goljan, M.: On estimation of secret message length in LSB steganography in spatial domain. Electronic Imaging, International Society for Optics and Photonics, 23–34 (2004)
Najeena, K.S., Imran, B.M.: An efficient steganographic technique based on chaotic maps and adpative PPM embedding. In: Signal Processing Image Processing & Pattern Recognition (ICSIPR), pp. 293–297. IEEE (2013)
Kurtuldu, O., Arica, N.: A new steganography method using image layers. In: ISCIS, pp. 1–4. IEEE (2008)
Kraetzer, C.: Visualisation of Benchmarking Results in Digital Watermarking and Steganography. In: ECRYPT, pp. 30–46. Citeseer (2007), IST-2002-507932
Sharp, T.: An implementation of key-based digital signal steganography. In: Moskowitz, I.S. (ed.) IH 2001. LNCS, vol. 2137, pp. 13–26. Springer, Heidelberg (2001)
Mielikainen, J.: LSB matching revisited. LSP IEEE 13(5), 285–287 (2006)
Provos, N., Honeyman, P.: Hide and seek: An introduction to steganography. IEEE Security & Privacy 1, 32–44 (2003)
Hempstalk, K.: Hiding behind corners: Using edges in images for better steganography. In: Proceedings of the Computing Women’s Congress, Hamilton, New Zealand, pp. 11–19 (2006)
Chen, W.J., Chang, C.C., Le, T.: High payload steganography mechanism using hybrid edge detector 37(4), 3292–3301 (2010)
Weiqi, L., Fangjun, H., Huang, J.: Edge Adaptive Image Steganography Based on LSB Matching Revisited. TIFS 5(2), 201–214 (2010)
Yi, L., Xiaolong, L., Bin, Y.: Locating steganographic payload for LSB matching embedding. In: ICME, pp. 1–6 (2011)
Battisti, F., Carli, M., Neri, A., Egiaziarian, K.: A Generalized Fibonacci LSB Data Hiding Technique. In: CODEC, pp. 671–683 (2006)
Patsakis, C., Fountas, E.: Extending Fibonacci LSB data hiding technique to more integer bases. In: ICACTE, vol. 4, pp. 18–27 (2010)
Mammi, E., Battisti, F., Carli, M., Neri, A., Egiazarian, K.: A novel spatial data hiding scheme based on generalized Fibonacci sequences. Proc. SPIE 6982, 1–7 (2008)
Abdulla, A.A., Jassim, S., Sellahewa, H.: Efficient high-capacity steganography techniques. Proc. SPIE 8755, 875508-1–875508-11 (2013)
http://sipi.usc.edu/database/database.php?volume=misc (last access date was Spetember 15, 2014)
http://www.microdicom.com/downloads.html (last access date was September 15, 2014)
Author information
Authors and Affiliations
Editor information
Editors and Affiliations
Rights and permissions
Copyright information
© 2014 Springer International Publishing Switzerland
About this paper
Cite this paper
Abdulla, A.A., Sellahewa, H., Jassim, S.A. (2014). Stego Quality Enhancement by Message Size Reduction and Fibonacci Bit-Plane Mapping. In: Chen, L., Mitchell, C. (eds) Security Standardisation Research. SSR 2014. Lecture Notes in Computer Science, vol 8893. Springer, Cham. https://doi.org/10.1007/978-3-319-14054-4_10
Download citation
DOI: https://doi.org/10.1007/978-3-319-14054-4_10
Publisher Name: Springer, Cham
Print ISBN: 978-3-319-14053-7
Online ISBN: 978-3-319-14054-4
eBook Packages: Computer ScienceComputer Science (R0)