Abstract
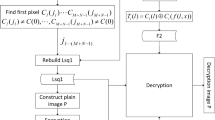
In this work, we analyze the security of the image encryption scheme proposed by Norouzi et al. (Multimedia Syst 20:45–64, 2014) [1]. The encryption scheme is based on a hash function and a two-round diffusion process applied to each 8 × 8 patches that compose the entire image. The analysis reveals the existence of a huge number of weak keys, allowing us to compute the effective key length, thus reducing the key space from 2512 to 2195 keys.
Access this chapter
Tax calculation will be finalised at checkout
Purchases are for personal use only
Similar content being viewed by others
References
Norouzi, B., Seyedzadeh, S.M., Mirzakuchaki, S., Mosavi, M.R.: A novel image encryption based on hash function with only two-round diffusion process. Multimed. Syst. 20, 45–64 (2014)
Bernstein, D.J.: “The Salsa20 Stream Cipher.” SKEW2005, Symmetric Key Encryption Workshop, 2005, Workshop Record. http://www.ecrypt.eu.org/stream/salsa20p2.html
Acknowledgments
This work has been supported by the MICINN under project “TUERI: Technologies for secure and efficient wireless networks within the Internet of Things with applications to transport and logistics”, TIN2011-25452.
Author information
Authors and Affiliations
Corresponding author
Editor information
Editors and Affiliations
Rights and permissions
Copyright information
© 2015 Springer International Publishing Switzerland
About this paper
Cite this paper
Peinado, A., García, A.O. (2015). Reducing the Key Space of an Image Encryption Scheme Based on Two-Round Diffusion Process. In: Herrero, Á., Baruque, B., Sedano, J., Quintián, H., Corchado, E. (eds) International Joint Conference. CISIS 2015. Advances in Intelligent Systems and Computing, vol 369. Springer, Cham. https://doi.org/10.1007/978-3-319-19713-5_38
Download citation
DOI: https://doi.org/10.1007/978-3-319-19713-5_38
Published:
Publisher Name: Springer, Cham
Print ISBN: 978-3-319-19712-8
Online ISBN: 978-3-319-19713-5
eBook Packages: EngineeringEngineering (R0)