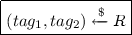Abstract
We propose a new message authentication code (MAC) based on a tweakable block cipher (TBC). We prove that the new MAC is a pseudo-random function (PRF) up to \(O(2^n)\) queries, that is, full PRF-security, where the output length of the TBC is n bits. We note that although Yasuda proposed a full PRF-secure MAC based on a compression function (CF), that does not offer a full PRF-secure TBC-based MAC due to the PRF/PRF switch. Hence our MAC is the first full PRF-secure one based on a TBC.
Access this chapter
Tax calculation will be finalised at checkout
Purchases are for personal use only
Notes
- 1.
- 2.
These MACs achieve \(O(2^{n}/\ell ^{1/2})\) PRF-security when using a block cipher with 2n-bit blocks.
References
Bellare, M., Guérin, R., Rogaway, P.: XOR MACs: new methods for message authentication using finite pseudorandom functions. In: Coppersmith, D. (ed.) CRYPTO 1995. LNCS, vol. 963, pp. 15–28. Springer, Heidelberg (1995)
Bernstein, D.J.: CAESAR: Competition for Authenticated Encryption: Security, Applicability, and Robustness
Bernstein, D.J.: How to stretch random functions: the security of protected counter sums. J. Cryptology 12(3), 185–192 (1999)
Black, J.A., Rogaway, P.: A block-cipher mode of operation for parallelizable message authentication. In: Knudsen, L.R. (ed.) EUROCRYPT 2002. LNCS, vol. 2332, pp. 384–397. Springer, Heidelberg (2002)
Coron, J.-S., Dodis, Y., Mandal, A., Seurin, Y.: A domain extender for the ideal cipher. In: Micciancio, D. (ed.) TCC 2010. LNCS, vol. 5978, pp. 273–289. Springer, Heidelberg (2010)
Dodis, Y., Pietrzak, K.: Improving the security of MACs via randomized message preprocessing. In: Biryukov, A. (ed.) FSE 2007. LNCS, vol. 4593, pp. 414–433. Springer, Heidelberg (2007)
Grosso, V., Leurent, G., Standaert, F.-X., Varici, K., Durvaux, F., Gaspar, L., Kerckhof, S.: SCREAM & iSCREAM side-channel resistant authenticated encryption with masking. Submission to CAESAR (2014)
Iwata, T., Kurosawa, K.: OMAC: one-key CBC MAC. In: Johansson, T. (ed.) FSE 2003. LNCS, vol. 2887, pp. 129–153. Springer, Heidelberg (2003)
Jean, J., Nikolic, I., Peyrin, T.: Tweaks and keys for block ciphers: the TWEAKEY framework. In: Sarkar, P., Iwata, T. (eds.) Advances in Cryptology - ASIACRYPT 2014. Lecture Notes in Computer Science, vol. 8874, pp. 274–288. Springer, Heidelberg (2014)
Jean, J., Nikolić, I., Peyrin, T.: Deoxys v1. Submission to CAESAR (2014)
Jean, J., Nikolić, I., Peyrin, T.: Joltik v1. Submission to CAESAR (2014)
Jean, J., Nikolić, I., Peyrin, T.: KIASU v1. Submission to CAESAR (2014)
Liskov, M., Rivest, R.L., Wagner, D.: Tweakable block ciphers. In: Yung, M. (ed.) CRYPTO 2002. LNCS, vol. 2442, pp. 31–46. Springer, Heidelberg (2002)
Lucks, S.: The sum of PRPs is a secure PRF. In: Preneel, B. (ed.) EUROCRYPT 2000. LNCS, vol. 1807, pp. 470–484. Springer, Heidelberg (2000)
Minematsu, K.: Beyond-birthday-bound security based on tweakable block cipher. In: Dunkelman, O. (ed.) FSE 2009. LNCS, vol. 5665, pp. 308–326. Springer, Heidelberg (2009)
Minematsu, K.: How to thwart birthday attacks against MACs via small randomness. In: Hong, S., Iwata, T. (eds.) FSE 2010. LNCS, vol. 6147, pp. 230–249. Springer, Heidelberg (2010)
Rogaway, P.: Efficient instantiations of Tweakable blockciphers and refinements to modes OCB and PMAC. In: Lee, P.J. (ed.) ASIACRYPT 2004. LNCS, vol. 3329, pp. 16–31. Springer, Heidelberg (2004)
Yasuda, K.: The sum of CBC MACs is a secure PRF. In: Pieprzyk, J. (ed.) CT-RSA 2010. LNCS, vol. 5985, pp. 366–381. Springer, Heidelberg (2010)
Yasuda, K.: A new variant of PMAC: beyond the birthday bound. In: Rogaway, P. (ed.) CRYPTO 2011. LNCS, vol. 6841, pp. 596–609. Springer, Heidelberg (2011)
Yasuda, K.: PMAC with parity: minimizing the query-length influence. In: Dunkelman, O. (ed.) CT-RSA 2012. LNCS, vol. 7178, pp. 203–214. Springer, Heidelberg (2012)
Yasuda, K.: A parallelizable PRF-based MAC algorithm: well beyond the birthday bound. IEICE Trans. 96–A(1), 237–241 (2013)
Zhang, Y.: Using an error-correction code for fast, beyond-birthday-bound authentication. In: Nyberg, K. (ed.) CT-RSA 2015. LNCS, vol. 9048, pp. 291–307. Springer, Heidelberg (2015)
Acknowledgments
The author would like to thank reviewers for helpful comments.
Author information
Authors and Affiliations
Corresponding author
Editor information
Editors and Affiliations
A Analysis of the XOR of Two Random Permutations \(\widetilde{P}^{tw_1}\) and \(\widetilde{P}^{tw_2}\)
A Analysis of the XOR of Two Random Permutations \(\widetilde{P}^{tw_1}\) and \(\widetilde{P}^{tw_2}\)
The following analysis is almost exactly the same as the one for Yasuda’s analysis in [18, 19] that follows the analysis for Lucks’ \(\text{ sum }^2\) construction [14].
In this case, we have only to analyze the case where the indistinguishability of the xor of two random permutations \(\widetilde{P}^{tw_1}\) and \(\widetilde{P}^{tw_2}\) from a random function under the following conditions.
-
The input \(w_1\) (resp., \(w_2\)) to \(\widetilde{P}^{tw_1}\) (resp., \(\widetilde{P}^{tw_2}\)) is a fresh input
-
The number of inputs to \(\widetilde{P}^{tw_1}\) is at most \(\rho -1\) due to \(\mathsf {mcoll}=\mathsf {false}\) and the same is true for \(\widetilde{P}^{tw_2}\).
Then we simulate the xor of two random permutation and a random function by using the technique of fair sets developed by Lucks. In this case, a fair set R is chosen so that the number of pair \((tag_1,tag_2) \in R\) such that
is the same for each \(tag \in \{0,1\}^n\). For \((w_1,w_2) \in \{0,1\}^n \times \{0,1\}^n\), we unroll the outputs of \(\widetilde{P}^{tw_1}\) into \(Y_1=\{tag_{1}^1, \ldots , tag_{1}^\alpha \}\), and the outputs of \(\widetilde{P}^{tw_2}\) into \(Y_2=\{tag_{2}^{1}, \ldots , tag_{2}^{\beta } \}\). Let \(Y_1^*\leftarrow \{0,1\}^n \backslash Y_1\) and \(Y_2^*\leftarrow \{0,1\}^n \backslash Y_2\). Then we choose a fair set \(R \subset Y_1^*\times Y_2^*\) as follows. For each \(1 \le j_1 \le \alpha \) and \(1 \le j_2 \le \beta \), we choose arbitrary representatives \((tag_{1}^{(j_1)},tag_{2}^{(j_2)}) \in Y_1^*\times Y_2^*\) such that \(tag_{1}^{(j_1)} \oplus tag_{2}^{(j_2)} = tag_{1}^{j_1} \oplus tag_{2}^{j_2}\). We then define \(R \leftarrow Y_1^*\times Y_2^*\backslash \bigcup _{j_1,j_2}\{ (tag_{1}^{(j_1)}, tag_{2}^{(j_2)}) \}\). We see that, for each value \(tag \in \{0,1\}^n\),
Hence R is a fair set. We note that \(\alpha \le \rho -1\) and \(\beta \le \rho -1\). Then for an input pair \((w_1,w_2)\), tag is defined by the following procedure.
-
1.
Choose a fair set \(R \subset Y_1^*\times Y_2^*\)
-
2.
\((tag_1,tag_2) \xleftarrow {\$}Y_1^*\times Y_2^*\)
-
3.
If \((tag_1,tag_2) \not \in R\) then
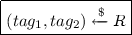
-
4.
\(tag \leftarrow tag_1 \oplus tag_1\)
-
5.
Return tag
Since R is a fair set, the above procedure without the boxed statement simulates the xor of two random permutations where \(tag_1\) is the output of \(\widetilde{P}^{tw_1}\) for input \(w_1\) and \(tag_2\) is the output of \(\widetilde{P}^{tw_2}\) for input \(w_2\), and the above procedure with the boxed statement simulates a random function.
Then at one execution of the above procedure, the probability that the behavior of the xor function is different from that of a random function is bounded by \(\frac{|Y_1^*\times Y_2^*\backslash R|}{|Y_1^*\times Y_2^*|} = \frac{\alpha \beta }{(2^n-\alpha )(2^n-\beta )} \le \frac{\rho ^2}{(2^n-\rho )^2} \).
Hence at the i-th query the probability that Case 4 holds is bounded by \(\frac{\rho ^2}{(2^n-\rho )^2} \).
Rights and permissions
Copyright information
© 2015 Springer International Publishing Switzerland
About this paper
Cite this paper
Naito, Y. (2015). Full PRF-Secure Message Authentication Code Based on Tweakable Block Cipher. In: Au, MH., Miyaji, A. (eds) Provable Security. ProvSec 2015. Lecture Notes in Computer Science(), vol 9451. Springer, Cham. https://doi.org/10.1007/978-3-319-26059-4_9
Download citation
DOI: https://doi.org/10.1007/978-3-319-26059-4_9
Published:
Publisher Name: Springer, Cham
Print ISBN: 978-3-319-26058-7
Online ISBN: 978-3-319-26059-4
eBook Packages: Computer ScienceComputer Science (R0)