Abstract
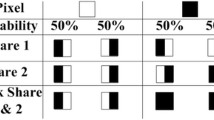
A visual cryptography scheme (VCS) encodes a secret image into several share images, such that stacking sufficient number of shares will reveal the secret while insufficient number of shares provide no information about the secret. The beauty of VCS is that the secret can be decoded by human eyes without needing any cryptography knowledge nor any computation. Variance is first introduced by Hou et al. in 2005 to evaluate the visual quality of size invariant VCS. Liu et al. in 2012 thoroughly verified this idea and significantly improved the visual quality of previous size invariant VCSs. In this paper, we first point out the security defect of Hou et al.’s multi-pixel encoding method (MPEM) that if the secret image has simple contours, each single share will reveal the content of that secret image. Then we use variance to explain the above security defect.
This paper is previously posted on Cryptology ePrint Archive: Report 2012/315.
Access this chapter
Tax calculation will be finalised at checkout
Purchases are for personal use only
Similar content being viewed by others
References
Ateniese, G., Blundo, C., De Santis, A., Stinson, D.R.: Visual cryptography for general access structures. Inf. Comput. 129, 86–106 (1996)
Bose, M., Mukerjee, R.: Optimal (k, n) visual cryptographic schemes for general k. Des. Codes Crypt. 55, 19–35 (2010)
Chen, T.H., Tsao, K.H.: Visual secret sharing by random grids revisited. Pattern Recogn. 42, 2203–2217 (2009)
Chen, T.H., Tsao, K.H.: Threshold visual secret sharing by random grids. J. Syst. Softw. 84, 1197–1208 (2011)
Cimato, S., De Prisco, R., De Santis, A.: Optimal colored threshold visual cryptography schemes. Des. Codes Crypt. 35, 311–335 (2005)
Cimato, S., De Prisco, R., De Santis, A.: Colored visual cryptography without color darkening. Theor. Comput. Sci. 374, 261–276 (2007)
Guo, T., Liu, F., Wu, C.K.: Threshold visual secret sharing by random grids with improved contrast. J. Syst. Softw. 86, 2094–2109 (2013)
Guo, T., Liu, F., Wu, C.K.: k out of k extended visual cryptography scheme by random grids. Sig. Process. 94, 90–101 (2014)
Hou, Y.C., Tu, S.F.: A visual cryptographic technique for chromatic images using multi-pixel encoding method. J. Res. Pract. Inf. Technol. 37, 179–191 (2005)
Kang, I.K., Arce, G.R., Lee, H.K.: Color extended visual cryptography using error diffusion. IEEE Trans. Image Process. 20(1), 132–145 (2011)
Liu, F., Guo, T., Wu, C.K., Qian, L.: Improving the visual quality of size invariant visual cryptography scheme. J. Vis. Commun. Image R. 23, 331–342 (2012)
Naor, M., Shamir, A.: Visual cryptography. In: De Santis, A. (ed.) EUROCRYPT 1994. LNCS, vol. 950, pp. 1–12. Springer, Heidelberg (1995)
Ito, R., Kuwakado, H., Tanaka, H.: Image size invariant visual cryptography. IEICE Trans. Fundam. Electron. Commun. Comput. Sci. E82–A(10), 2172–2177 (1999)
Shyu, S.J.: Image encryption by random grids. Pattern Recogn. 40, 1014–1031 (2007)
Shyu, S.J., Chen, M.C.: Optimum pixel expansions for threshold visual secret sharing schemes. IEEE Trans. Inf. Forensics Secur. 6(3), 960–969 (2011)
Yang, C.N.: New visual secret sharing schemes using probabilistic method. Pattern Recogn. Lett. 25, 481–494 (2004)
Acknowledgments
This work was supported by 863 Program grant No. Y370071102, the “Strategic Priority Research Program” of the Chinese Academy of Sciences grant No. XDA06010701 and the “Fundamental Research Funds for the Central Universities” grant No. 3262015T20 (Topic: A new exploration of information research technology of Big Data environment, Project Leader: Yang LiangBin). Many thanks to the anonymous reviewers for their valuable comments.
Author information
Authors and Affiliations
Corresponding author
Editor information
Editors and Affiliations
Rights and permissions
Copyright information
© 2015 Springer International Publishing Switzerland
About this paper
Cite this paper
Guo, T., Liu, F., Wu, C., Hou, Y., Ren, Y., Wang, W. (2015). The Security Defect of a Multi-pixel Encoding Method. In: Desmedt, Y. (eds) Information Security. Lecture Notes in Computer Science(), vol 7807. Springer, Cham. https://doi.org/10.1007/978-3-319-27659-5_3
Download citation
DOI: https://doi.org/10.1007/978-3-319-27659-5_3
Published:
Publisher Name: Springer, Cham
Print ISBN: 978-3-319-27658-8
Online ISBN: 978-3-319-27659-5
eBook Packages: Computer ScienceComputer Science (R0)