Abstract
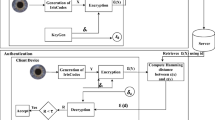
With the widespread development of biometric systems, concerns about security and privacy are increasing. An active area of research is template protection technology, which aims to protect registered biometric data. We focus on a homomorphic encryption approach, which enables building a “cryptographically-secure” system. In DPM 2013, Yasuda et al. proposed an efficient template protection system, using the homomorphic encryption scheme proposed by Brakerski and Vaikuntanathan. In this work, we improve and fortify their system to withstand impersonation attacks such as replay and spoofing attacks. We introduce a challenge-response authentication mechanism in their system and design a practical distributed architecture where computation and authentication are segregated. Our comprehensive system would be useful to build a large-scale and secure biometric system such as secure remote authentication over public networks.
Access this chapter
Tax calculation will be finalised at checkout
Purchases are for personal use only
Similar content being viewed by others
References
Jain, A.K., Nandakumar, K., Nagar, A., et al.: Biometric template security. EURASIP J. Adv. Signal Process. 113 (2008)
Blanton, M., Gasti, P.: Secure and efficient protocols for iris and fingerprint identification. In: Atluri, V., Diaz, C. (eds.) ESORICS 2011. LNCS, vol. 6879, pp. 190–209. Springer, Heidelberg (2011)
Bolle, R.M., Connell, J.H., Ratha, N.K.: Biometric perils and patches. Pattern Recognit. 35(12), 2727–2738 (2002)
Boneh, D., Goh, E.-J., Nissim, K.: Evaluating 2-DNF formulas on ciphertexts. In: Kilian, J. (ed.) TCC 2005. LNCS, vol. 3378, pp. 325–341. Springer, Heidelberg (2005)
Brakerski, Z., Vaikuntanathan, V.: Fully homomorphic encryption from ring-LWE and security for key dependent messages. In: Rogaway, P. (ed.) CRYPTO 2011. LNCS, vol. 6841, pp. 505–524. Springer, Heidelberg (2011)
Bringer, J., Chabanne, H.: An authentication protocol with encrypted biometric data. In: Vaudenay, S. (ed.) AFRICACRYPT 2008. LNCS, vol. 5023, pp. 109–124. Springer, Heidelberg (2008)
Bringer, J., Chabanne, H., Izabachène, M., Pointcheval, D., Tang, Q., Zimmer, S.: An application of the Goldwasser-Micali cryptosystem to biometric authentication. In: Pieprzyk, J., Ghodosi, H., Dawson, E. (eds.) ACISP 2007. LNCS, vol. 4586, pp. 96–106. Springer, Heidelberg (2007)
Campisi, P.: Security and Privacy in Biometrics. Springer, New York (2013)
Damgård, I., Geisler, M., Krøigård, M.: Homomorphic encryption and secure comparison. Int. J. Appl. Cryptogr. 1(1), 22–31 (2008)
Daugman, J.: The importance of being random: statistical principles of iris recognition. Pattern Recognit. 36(2), 279–291 (2003)
Dodis, Y., Reyzin, L., Smith, A.: Fuzzy extractors: how to generate strong keys from biometrics and other noisy data. In: Cachin, C., Camenisch, J.L. (eds.) EUROCRYPT 2004. LNCS, vol. 3027, pp. 523–540. Springer, Heidelberg (2004)
Evans, D., Huang, Y., Katz, J., Malka, L.: Efficient privacy-preserving biometric identification. In: 17th Proceedings of the Network and Distributed System Security Symposium-NDSS, 2011 (2011)
Fujitsu Laboratories Ltd. Press release: Fujitsu develops world’s first authentication technology to extract and match 2,048-bit feature codes from palm vein images (2013)
Goldwasser, S., Micali, S.: Probabilistic encryption and how to play mental poker keeping secret all partial information. In: Proceedings of the Fourteenth Annual ACM Symposium on Theory of Computing-STOC, pp. 365–377. ACM (1982)
Hattori, M., Matsuda, N., Ito, T., Shibata, Y., Takashima, K., Yoneda, T.: Provably-secure cancelable biometrics using 2-DNF evaluation. J. Inf. Process. 20(2), 496–507 (2012)
Hirano, T., Hattori, M., Ito, T., Matsuda, N.: Cryptographically-secure and efficient remote cancelable biometrics based on public-key homomorphic encryption. In: Sakiyama, K., Terada, M. (eds.) IWSEC 2013. LNCS, vol. 8231, pp. 183–200. Springer, Heidelberg (2013)
Izu, T., Sakemi, Y., Takenaka, M., Torii, N.: A spoofing attack against a cancelable biometric authentication scheme. In: Advanced Information Networking and Applications-AINA. IEEE (2014)
Kulkarni, R., Namboodiri, A.: Secure hamming distance based biometric authentication. In: International Conference on Biometrics (ICB), pp. 1–6. IEEE (2013)
Osadchy, M., Pinkas, B., Jarrous, A., Moskovich, B.: SCiFI-a system for secure face identification. In: IEEE Symposium on Security and Privacy (SP), pp. 239–254. IEEE (2010)
Paillier, P.: Public-key cryptosystems based on composite degree residuosity classes. In: Stern, J. (ed.) EUROCRYPT 1999. LNCS, vol. 1592, pp. 223–238. Springer, Heidelberg (1999)
Rathgeb, C., Uhl, A.: A survey on biometric cryptosystems and cancelable biometrics. EURASIP J. Inf. Secur. 2011(1), 1–25 (2011)
Simoens, K., Bringer, J., Chabanne, H., Seys, S.: A framework for analyzing template security and privacy in biometric authentication systems. IEEE Trans. Inf. Forensics Secur. 7(2), 833–841 (2012)
Upmanyu, M., Namboodiri, A.M., Srinathan, K., Jawahar, C.: Blind authentication: a secure crypto-biometric verification protocol. IEEE Trans. Inf. Forensics Secur. 5(2), 255–268 (2010)
U.S. Department of Homeland Security. Privacy impact assessment for the biometric storage system (2007)
Yasuda, M., Shimoyama, T., Kogure, J., Yokoyama, K., Koshiba, T.: Packed homomorphic encryption based on ideal lattices and its application to biometrics. In: Cuzzocrea, A., Kittl, C., Simos, D.E., Weippl, E., Xu, L. (eds.) cd-ares workshops 2013. LNCS, vol. 8128, pp. 55–74. Springer, Heidelberg (2013)
Yasuda, M., Shimoyama, T., Kogure, J., Yokoyama, K., Koshiba, T.: Practical packing method in somewhat homomorphic encryption. In: Garcia-Alfaro, J., Lioudakis, G., Cuppens-Boulahia, N., Foley, S., Fitzgerald, W.M. (eds.) DPM 2013 and SETOP 2013. LNCS, vol. 8247, pp. 34–50. Springer, Heidelberg (2014)
Author information
Authors and Affiliations
Corresponding author
Editor information
Editors and Affiliations
Rights and permissions
Copyright information
© 2016 Springer International Publishing Switzerland
About this paper
Cite this paper
Mandal, A., Roy, A., Yasuda, M. (2016). Comprehensive and Improved Secure Biometric System Using Homomorphic Encryption. In: Garcia-Alfaro, J., Navarro-Arribas, G., Aldini, A., Martinelli, F., Suri, N. (eds) Data Privacy Management, and Security Assurance. DPM QASA 2015 2015. Lecture Notes in Computer Science(), vol 9481. Springer, Cham. https://doi.org/10.1007/978-3-319-29883-2_12
Download citation
DOI: https://doi.org/10.1007/978-3-319-29883-2_12
Publisher Name: Springer, Cham
Print ISBN: 978-3-319-29882-5
Online ISBN: 978-3-319-29883-2
eBook Packages: Computer ScienceComputer Science (R0)