Abstract
Cloud computing is an emergent technology that brings together all aspects of IT infrastructure from software installation and upgrade to platform oriented services to network and to hardware and storage. However, there are various security concerns that prevent customers from taking benefits of the cloud. Many studies have offered a wide range of possible solutions to deal with cloud security issues. Some of these solutions are very expensive therefore not suitable for Cloud. For example, data encryption is considered as a vital tool and mechanism for securing business data. However, it is not feasible to deploy data encryption on every piece of data. Anthes argues that encryption is sometimes seen as the ultimate security measure, but in fact, encryption is a complex and costly process since encrypted data needs to be downloaded and decrypted for local use and then possibly uploading the results [1]. This study offers a robust, fast and cost effective security measures for protecting Cloud data residing on virtual machines (VMs) without the need for any additional monitoring package or introspection at VM level.
You have full access to this open access chapter, Download conference paper PDF
Similar content being viewed by others
Keywords
1 Introduction
Cloud technology is a radical IT innovation that brings together operational changes to every stage of computing from software installation, upgrade, maintenance and backups, to security [2]. This brings enormous possibilities of continuous innovation [3]. At the same time these changes are precarious [4], and need previsioning of complementary resources [5].
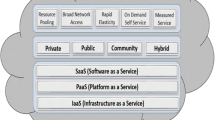
The Cloud technology completely redefines computing infrastructure, in which the infrastructure ownership is migrating to the subscription fees. There are many benefits of Cloud over the existing in-house IT infrastructure, including but not limited to: (1) On demand self-service, (2) Broad Network Access, (3) Resource Pooling, (4) Rapid elasticity, and (5) Measured services and (6) Platform Independency. Cloud computing offers also three main services: Software as a Service (SaaS), Platform as a Service (PaaS) and Infrastructure as a Service (IaaS). On the other hand there are many security and privacy issues discussed in literature associated with each of the above services.
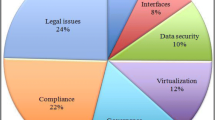
Many customers desire to have the security, ethical and confidentiality principles provided by their LANs while connecting to a cloud. This is in particular important for mission critical applications such as financial data, R&D and clients private information among others. As such data management and data security is one of the core components concerning many organizations. As such understanding what is public cloud data and what is secure private data are among the most challenging and important tasks that face the adoption of cloud computing by businesses. In addition, cloud data is one of the main sources of today’s “big data”. Hemerly argues that the term big data not only describes size, it also describes the speed, volume and computational and analytical capacity required to manage data and derive insight [6]. It is important to secure as much as possible the processes and procedures about generating, computing, collecting, disseminating and securing data. Cloud security has always been the main concern for providers and for service consumers. Every provider implements its own best practices and security frameworks to serve customers’ needs better and, at the same time, to comply with regulations and government requirements. According to a 2010 IBM Global IT Risk Study 77 % of respondents think that Cloud technology makes data privacy protection more difficult; the main concern of 50 % of respondents is data loss or breach, and only 23 % worry about corporate network security as the main concern [7]. In 2010, IBM started a new initiative to make the Cloud more secure. IBM understands that one security policy would not fit the variety of customer requirements, so IBM provides teams of security consultants that work with customers on their specific security needs.
The scope of Cloud security is massive by any measures. It is clear that all aspects of security including authorization, authentication, accountability, and endpoint-to-endpoint security are important, but broader considerations such as data protection, business continuity, and disaster recovery are very important to businesses as well. Customers’ data storage and usage is an ongoing struggle for data privacy management, data misuse and violation.
2 Cloud Security Issues
Using Cloud computing brings significant benefits, including increased operations and economic efficiency, enhancing scalability and collaboration, and low start-up and maintenance costs. However, without proper security and privacy solutions the whole concept could be a big failure.
Identification and authentication define who can log into a system, while authorization provides permission for users to have access to specific resources based on individual or group memberships or assigned roles. Common authentication procedures provide at least one of the following factors: something you know, something you have, something you are, and where you are. Accountability’s role is to keep track of the users’ and system log to help identify security violations and analyze security incident [8].
With the SaaS model, providers implement built-in security features. In the public Cloud end-users utilize features available for this application to protect data, while in the private Cloud organization is flexible to allow for the implementation of an acceptable level of security measures. In the PaaP model developers are responsible for securing their own applications, while providers hold the responsibility to secure the operating system and separate applications for tenants. In the IaaS model developers are in charge of the whole system and have to provide low-level system security and application level security.
Multi-tenancy is the Cloud concept of sharing resources among many end-users. This concept raises additional security concerns. Different Cloud providers resolve this problem in their own ways. For example, Salesforce.com separates users on a database level, securing data with carefully written databases queries, whereas Amazon implements virtualization on a hardware level to separate tenants [9].
A Service level agreement (SLA) defines the quality of service that a Cloud provider will deliver. While up time and bandwidth can be easily measured, security and privacy are not quantifiable. However, with proper monitoring and auditing, security incidents can be detected and brought to the SLA bargain process [9].
Compliance and regulations can potentially cause many jurisdictional problems in terms of which laws or regulations should apply depending on the data type or the user’s residence. Also, depending on the business, companies have to comply with such regulations as the Health Insurance Portability and Accountability Act (HIPAA), Payment Card Industry Data Security Standards (PCI DSS), the Sarbanes Oxley Act on IT Security (SOX), Canada’s Anti-Spam Legislation (Bill C-28) and others [ 10].
Security issues in Cloud are multiplied by issues at every individual service and application. Cloud computing virtual environments are independent domains with different privacy, security and trust relation approaches. Cloud service providers sometimes combine a few services to create new, better-quality application services. Such environmental domains use individually configured applications, services, and other settings. Hence, particular procedures have to be in place to guarantee that this dynamic structure is designed and maintained securely and security incidents and breaches are efficiently monitored and examined during the exploitation process. Even though each separate domain’s policies are under control, security breaches can simply happen during integration [11].
3 Security Threats and Challenges
Cloud solutions integrate different parts of the computing infrastructure. As a whole, infrastructural security solutions are a product of all involved levels. Attacks can be accordingly divided by targeting levels as well: Data, Application, Host, and Network levels (Fig. 1) [9].
3.1 Network Level Attacks
At the Network level, security assumptions are different for Private and Public Clouds. In the Private Cloud, since the infrastructure lies within a company’s premises, the firm has full control over this Cloud infrastructure. That means that all Cloud vulnerabilities and threats are the same as for corporate’s services, and all firm’s implemented threat mitigation measures can be applied to the Cloud infrastructure as well. For the public infrastructure security of access control, ensuring confidentiality, integrity, and availability (CIA) of data accessible through the Internet are the major risks on the Network level security [12].
Access control can be affected by reusable IP addresses. The IP v4 address pool is limited, and Cloud providers re-assign the same address to a new client when the address is released. At the same time there is some delay in updating DNS cash servers so a new customer may be exposed to some risk when accessing his/her Cloud resources through old DNS records to his/her new (re-assigned) IP address. Similar problems can occur with a reverse address resolution when the changed physical address is not updated at the ARP table. The Amazon Cloud provider offers elastic IP addresses where customers can fully control IP release. This helps avoid the aforementioned problem if the customer carefully manages their address space. However, this problem still cannot be resolved if customers use internal (non-routable) IP addresses within one Cloud provider [13]. An access control audit for network level logs in the Public Cloud is also cumbersome and may affect all types of Cloud services [13].
The confidentiality and integrity risks of customers’ data that are exposed to the Internet are significant. When Amazon implemented Amazon Web Services (AWS) Signature Version 1, a vulnerability report showed that the solution is insecure and many customers were unsatisfied with the provided level of security. Soon after that Amazon released AWS Signature Version 2, or suggested switching to HTTPS to mitigate integrity and confidentiality risk [14]. Secure Socket Layer/Transport Layer Security (SSL/TLS) is using to establish a protected, encrypted connection between a website and a client’s web browser. Such connections are used to securely manage all features of provided Cloud services. The Internet researchers Juliano Rizzo and Thai Duong found a way to hack into the secured channel. They suggested using java script code built into a browser that acts as a Trojan horse, along with a network sniffer. This allows attackers to interfere with a secured tunnel, and to break SSL encryption. This attack was named BEASK (Browser Exploit against SSL/TLS) and has the potential to affect millions of websites [15].
The availability of data stored on the Cloud provider’s premises is getting more important as more and more customer data is being saved on the Public Cloud. There are different types of attacks that can affect data availability. Some major attacks including but not limited to: DDoS attack on servers, DNS cash poising attack, IP spoofing attacks and ARP cache poisoning attacks [16, 17, 21].
3.2 Host Level Attacks
Security issues at the host level differ for Cloud models such as SaaS, PaaS, or IaaS and public or private deployment types. Threats at the host level are associated with its Virtual Machine (VM) vulnerabilities. For PaaS and SaaS services the Cloud provider does not share its platform with customers, therefore the provider is responsible for implementing the appropriate level of protection for VMs. A secure model of VM implementation which will be discussed in this paper is the main focus of this paper.
The following security threats are associated with IaaS services:
Hypervision Security Threats:
When an attacker controls software that provides virtualization. The biggest threat is from “zero-day” vulnerabilities and can be anticipated by implementing the best security practices and frameworks that include, but are not limited to, host hardening, and patching and updating hosting software.
Perimeter Security:
In some cases, virtual servers can reside outside of a firewall, which makes their securing more complex. Even when the servers are behind a Public Cloud provider’s firewalls, they can be cracked by attackers inside the premises. A partial solution is to isolate virtual resources within their perimeters.
VM Security:
Guest VMs are isolated from each other with hypervision software. Once a VM is allocated to customers, they are recommended to use a secured connection to manage their allocated resources. These are, for example, SSH and SSL/TLS. Other vulnerable services and protocols, such as FTP and NETBIOS, should be eliminated or substituted with their more secure analogs. Public Cloud providers should implement some operating procedures for properly deploying firewalls and enforce the use of strong passwords for user accounts [18].
3.3 Application Level Attacks
At this level customers have a lack of access control to audit logs, updates and patch management. In the public deployment model customers have to rely on providers’ protection measures, while in the private model they can implement an appropriate amount of security at the host level. Security for hosting applications should be built into the software development life-cycle and provide quality assurance security testing at each stage of this cycle. The Open Web Application Security Project identifies ten security risks in web applications [19]. These security risks are: (1) Injection, (2) Cross-Site Scripting, (3) Broken Authentication and session management, (4) Insecure Direct Object References, (5) Cross-Site Request Forgery, (6) Security Misconfiguration, (7) Insecure Cryptographic storage, (8) Failure to Restrict URL Access, (9) Insufficient Transport Layer Protection, and (10) Invalidated Redirects and Forwards.
3.4 Data Level Attacks
Data level security is important for all Cloud models. Several aspects of data security have been discussed by [12]. These aspects including but not limited to: Data-in-transit is all data transferred across the network. Data-at-rest is data on file-servers and other storage areas. Data lineage is the process of tracking a data’s origin and restricting that data’s distribution to within defined premises for only audit and compliance purposes. Data provenance is the process of ensuring data integrity, which means precise and accurate data computation. Data remanence is the residual information present even after the data has been erased or moved to another location.
4 Virtualization Issues
Virtualization is a mechanism that connects physical hardware and virtual machines. It is also in charge of resource allocation and management for underlying services. The hypervisor or VM monitor compartmentalizes tenants on the physical computer and lets users run independent instances of VMs simultaneously and independently. This is fundamental for Cloud infrastructure, as providing a high level of security for virtualization is essential. The following types of VM vulnerabilities are most common [22].
4.1 VM Hopping
An attacker in such attacks resides on one of VMs and obtains access to a different instance of VM that is hosted on the same server, and the invader has to know target’s IP address. There are different vectors of attacks and they are based on the type of host’s hypervisor and other system vulnerabilities. After the attacker obtains access to the target’s VM, he/she can modify the victim’s configuration, and delete or tamper data. This type of attack targets IaaS and PaaS infrastructures, although it can indirectly strike SaaS since it uses the other types of infrastructure for its foundation. This type of attack is very common because it thrives on the basic Cloud principle of multi-tenancy [23].
4.2 VM Mobility
Almost all Cloud providers offer VM image replication features. Users can choose to use one of the pre-setup configurations from a repository. This feature facilitates quick configuration deployment but also distributes the same vulnerabilities that pertain to that particular setup. The attacker can know and use the configuration weaknesses. The results of this type of attack can lead to completely compromising a large number of new guest VMs. The attack mostly targets the IaaS model, as Cloud providers offer hardware resources and pre-installed VM images that users can customize. At the same time confidentiality, integrity and availability of the SaaS and PaaS models can be compromised, as they are exposed by the underlying IaaS vulnerabilities [24].
4.3 VM Diversity
Virtualization allows users to effortlessly deploy new virtual configurations in seconds. Users can choose different types of operating systems and pre-setup software configurations. That configuration diversity makes security management more challenging. The Service Level Agreement between a Cloud provider and a user can help to anticipate this issue. For the IaaS model, the Cloud provider obliges to supporting the hypervisor and servicing security, while the user has to strengthen his/her VM instances by applying patches, updates, and implementing best security practices. Similarly, for PaaS and SaaS models SLA can define and regulate a provider’s and user’s responsibilities for security management processes [25, 26].
4.4 VM Denial of Service
A Denial-of-service (DoS) attack happens after a guest’s VMs occupies the CPU, network bandwidth, or hard drive throughput, and the hypervisor cannot allocate the resources to other guest machines. The base way to withstand this attack is to have a SLA that defines resource allocation to user’s VMs. The SaaS Cloud model is less exposed to such attacks compare to the PaaS or IaaS models [25].
A Distributed Denial of Service (DDoS) attack happens when attackers take control over a number of computers with some vulnerability, and initiate a flood of traffic to the target machine.
4.5 The Insider Threat
All security counter-measures make sense only when attacks are external. However, data from VM can be compromised by anyone with administrative access, by whom all security precautions and efforts to monitor malicious activity can be circumvented. According to a VMworld magazine survey, 93 % of companies have mission-critical data at some virtual environment, and more than 70 % of respondents think that their colleagues could attack that data if they wanted to [27]. The only way to contend with the insider threat is to implement the same standards, audit practices, processes, and tools that a company uses in-house.
5 Virtualization and Multi-tenancy
Most articles so far already identified multi-tenancy and virtualization as main threats to cloud security. A paper called “A Distributed Access Control Architecture for Cloud Computing” discusses a possible solution to these problems using distributed architecture. The authors [28] discuss the system where both security management and software engineering techniques are used together. The authorization requirements are built using the following three components:
-
1)
VRM (virtual resource manager) is located at each layer of the cloud and is responsible for providing and deploying virtual resources
-
2)
DACM (distributed access control module) is also located at each layer and enforces access control policy
-
3)
SLA (service level agreement) performs role mapping, prevents side-channel attacks by describing isolation constraints and presents a virtualized view of resources.
The only way to deliver secure multi-tenancy is to have some kind of isolation between tenant’s data while at rest and in transition as well as physical location transparency where tenants can’t determine where their data and resources are located to prevent side-channel attacks [30]. For example, Amazon Virtual Private Cloud allows the customer to specify set of virtual machines that can communicate only through an encrypted channel. There are some products on the market aimed at enhancing cloud security – IBM’s Websphere Cast Iron and Cisco IronPort both provide among others secure messaging [30].
5.1 V2LAN
As indicated most of Cloud security discussed above are related to VMs (see Table 1). This study offers a Virtualized Virtual LAN (V2LAN) for protecting VMs locating on one or more physical servers. As we know each physical server is capable of providing many virtual machines providing computing resources to multiple organizations. Securing VMs against any data leak or unauthorized access is one of the main responsibilities of cloud providers. On the other hand customers should be aware of the importance of SLA in providing legal support in case unauthorized access to data and data leak occurs. We should not forget the fact that Cloud products and services are available to evry organization and to every individuals with the swipe of a credit card including hackers. This study offers a robust solution to secure VMs against any type of data leak.
A Virtual LAN defines a broadcast domain in which only those nodes that are grouped within a cluster are able exchange messages if desired. This feature provides a high level of abstraction and security at layer 2 level (as defined by OSI). For example, a common backbone connection shared across VLAN trunks or infrastructure can provide a very high level of security with great flexibilities. As such many Cloud features such as security, scalability and virtual machines are supported by VLAN. In fact a Cloud-aware switches have support for device virtualization at both layer 2 (datalink layer) and layer 3 (network layer). These types of switches are often referred to as a layer 2.5 protocol. For example Cisco Nexus 7000 Series switches can be configured to support Virtualized VLAN or V2LAN for short. They support the so called Virtual Device Contexts (VDCs). Each VDC runs as a separate logical entity comprising switching, security, and services that is designed for physical, virtual, and cloud environments. It uniquely integrates with servers, storage, and orchestration platforms for more efficient operations and greater scalability [31]. As shown in Fig. 2 each VDC is a complete unit capable of layer 3 routing via its virtual route forwarding (VRF) as well as layer 2 VLAN.
5.2 V2LAN Implementation
The routing structure offered by VLANs in connection with VDC has a close and similar implementation with those of Multiprotocol Label Switching (MPLS) in which packet forwarding mechanism use Forwarding Information Base (FIB). FIB is based on a data structure called Routing Information Base (RIB). RIB is essentially a routing table. To make a decision about the best route, V2LAN FIB is relying on information provided by RIB for its outgoing traffic (traffic outside VM environment).
Figure 2 above shows a physical server containing some VMs (VM1 through VM15). Assume that only VM4 through VM9 are designed for Customer 1, and the rest of VMs belong to other clients. Our Cloud switch via its V2LAN1 component defines a unique broadcast domain that includes only these VMs; no other VMs can access or listen to message exchange within the domain of V2LAN1. V2LAN is acting as a buffer against data leakage within the context of virtual machines. This IaaS-based security feature is deployed in addition to SaaS-based VM security offered by the hypervisor. Anthes has noted that IBM Research deployed a method for securing VM known as “virtual machine introspection”; in which it puts security inside a protected VM running on the same physical machine [1]. Recent VM security employs a number of protective measures such as whitelisting and blacklisting of the guest kernel functions [1]. These activities are aimed to determine the operating system and the version of the VM. While V2LAN provides strong buffer against these types of activities, it eliminates the need of deploying or cloning such functions at VM levels.
V2LAN implementation is a secure and cost effective solution for increased business agility with VMs and their motilities [31]. It reduces capital and operational expenditures through more efficient use of hardware and storage devices and more efficient management, Create an architecture that supports futures growth, server performance, and storage and virtualization goals [31].
6 Conclusion
There are many advantages in using Cloud-based systems. However, there are also many technological problems that have not yet been solved. The Cloud is a technology that is widely used in the whole IT sector. Retaining factors such as data privacy and information security issues, computing power efficiency, and SLA related concerns are still holding back complete adoption of the technology.
Acceptance of the Cloud requires a shift in its perception and also the understanding of all its accompanying problems, especially security related ones. Although some security risks are already present at the traditional computing model, while using Cloud, the security risks might have a higher impact on businesses. Currently Cloud security has a lot of loose ends that deter potential Cloud customers from migration there. Until proper security mechanisms are in place, prospective customers are not going to leverage the advantages of Cloud technology.
As indicated above, VMs are one of the main sources of concern within the context of Cloud security. In this study we offered a cost effective solution to tackle this issue. It offers a layer 2 and 3 solution to harden communication among interrelated VMs and prevent issues such as black listening or data leak.
Finally, it is important to note that this study is limited to VM issues and more specifically the issues related to data leak as such it does not claim that it has addressed all Cloud security issues as discussed in this paper.
References
Anthes, G.: Security in the cloud. Commun. ACM 53(11), 16–18 (2010)
Truong, D.: How cloud computing enhances competitive advantages: a research model for small business. Bus. Rev. 15(1), 59–65 (2010)
Carlo, J.L.: Internet computing as a disruptive information technology innovation: the role of strong order effects. Inf. Syst. J. 21, 91–122 (2011)
Dewar, R., Dutton, E.J.: The adoption of radical and incremental innovations: an empirical analysis. Manag. Sci. 32, 1422–1433 (1986)
Teece, D.P.: Dynamic capabilities and strategic management. Strateg. Manag. J. 18, 509–533 (1997)
Hemerly, J.: Public policy considerations for data-driven innovation. IEEE Comput. Soc. 46(6), 25–31 (2013)
Chisholm, T., Smigala, H.: IBM Advances Cloud Computing in Education; Unveils IBM Cloud Academy (2009). http://www-03.ibm.com/press/us/en/pressrelease/28749.wss
Katzan, H.: On the privacy of cloud computing. Int. J. Manag. Inf. Syst. 14(2), 1–12 (2010)
Kulkarni, G., Gambhir, J., Patil, T., Dongare, A.: A security aspects in cloud computing. In: 2012 IEEE 3rd International Conference on Software Engineering and Service Science (ICSESS), pp. 547–550 (2012)
Takabi, H., Joshi, J.B., Ahn, G.J.: Security and privacy challenges in cloud computing environments. IEEE Secur. Priv. 8(6), 24–31 (2010)
Jordan, J.: Climbing out of the box and into the cloud: building webscale for libraries. J. Libr. Adm. 51(1), 3–17 (2011)
Mather, T., Kumaraswamy, S., Latif, S.: Cloud Security and Privacy: An Enterprise Edition on Risks and Compliance (Theory in Practice), O’Reilly Media, ISBN: 978-0596802769 (2009)
Rekhter: Address allocation for private internets (1996). Retrieved from Network Working Group. http://tools.ietf.org/html/rfc1918
Amazon AWS. AWS Signature Version 1 is Insecure (2008). http://www.daemonology.net/blog/2008-12-18-AWS-signature-version-1-is-insecure.html
The register. Hackers Break SSL Encryption Used by Millions of Sites (2011). http://www.theregister.co.uk/2011/09/19/beast_exploits_paypal_ssl
Atkins, D.: Threat Analysis of the Domain Name System (DNS) (2004). Retrieved from Network Working Group. http://tools.ietf.org/html/rfc3833
Evans, K.: IP Spoofing Attack and Defenses (2010). http://resources.infosecinstitute.com/ipspoofing-attack
Contextis. Assessing Cloud Node Security whitepapers@ (2011). Retrieved from Context Information Security: contextis.com
OWASP. The Ten Most Critical Web Application Security Risks (2010). Retrieved from Open Web Application Security Project. https://www.owasp.org/index.php/Category:OWASP_Top_Ten_Project
Sudha, S., Viswanathan, V.M.: Addressing security and privacy issues in cloud computing. J. Theor. Appl. Inf. Technol. 48(2), 708–719 (2013)
Fewer, S.: ARP Poisoning an Investigation into Spoofing the Address Resolution Protocol (2009). http://www.harmonysecurity.com
Garfinkel,T., Rosenblum, M.: When virtual is harder than real: security challenges in virtual machine based computing environments. In: Proceedings of the 10th Workshop on Hot Topics in Operating Systems (2005). USENIX Association. https://www.usenix.org/legacy/events/hotos05/final_papers/garfinkel.html
Ristenpart, T. Tromer, E., Shacham, H., Savage, S.: Hey, you, get off of my cloud: exploring information leakage in third-party compute clouds. In: Proceedings of the 16th ACM Conference on Computer and Communications Security (CCS 09), pp. 199–212. ACM Press (2009)
Oberheide, C. J.: Empirical exploitation of live virtual machine migration. In: Proceedings of Black Hat DC 2008 Convention (2008). www.net-security.org/dl/articles/migration.pdf
Tsai, H., Siebenhaar, M., Miede, A., Huang, Y., Steinmetz, R.: Threat as a service?: virtualization’s impact on cloud security. IEEE Comput. Soc. 14(1), 32–37 (2012)
Yan, J., Early, S., Anderson, R.: The XenoService – A Distributed Defeat for Distributed Denial of Service. Proceedings of Information Survivability Workshop, Boston, Massachusetts, USA (2000)
Moss, H., Zierick, J.: Cloud providers will be better at security than you can ever be. Netw. World 28(4), 27–28 (2011)
Almutairi, A., Sarfraz, M.I., Basalamah, S., Walid, G., Aref, W.G., Ghafoor, A.: A distributed access control architecture for cloud computing. IEEE Softw. 29(2), 36–44 (2012)
Behl, A., Behl, K.: An analysis of cloud computing security issues. In: 2012 World Congress on Information and Communication Technologies (WICT), pp. 109–114 (2012)
Cachin, C., Schunter, M.: A cloud you can trust - IEEE Spectrum, December issue, pp. 28–33 (2011)
Cisco. Technical Overview of Virtual Device Contexts, Cisco Systems Inc. (2012)
Author information
Authors and Affiliations
Corresponding author
Editor information
Editors and Affiliations
Rights and permissions
Copyright information
© 2016 Springer International Publishing Switzerland
About this paper
Cite this paper
Shirazi, F., Krasnov, A. (2016). Cloud Security: A Virtualized VLAN (V2LAN) Implementation. In: Kurosu, M. (eds) Human-Computer Interaction. Theory, Design, Development and Practice . HCI 2016. Lecture Notes in Computer Science(), vol 9731. Springer, Cham. https://doi.org/10.1007/978-3-319-39510-4_56
Download citation
DOI: https://doi.org/10.1007/978-3-319-39510-4_56
Published:
Publisher Name: Springer, Cham
Print ISBN: 978-3-319-39509-8
Online ISBN: 978-3-319-39510-4
eBook Packages: Computer ScienceComputer Science (R0)