Abstract
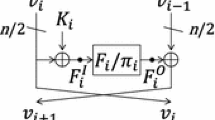
In SAC 2013, Berger et al. defined Extended Generalized Feistel Networks (EGFN) and analyzed their security. They proposed designs with 8 or 16 branches. This class of schemes is well-suited for cryptographic applications. Using the minimal number of active S-boxes, the authors showed that for 64-bits messages divided into 8 branches, at least seven rounds are needed for security against differential and linear cyptanalysis. They proved that 10 rounds are required against integral attacks and 9 rounds against impossible differential attacks. In this paper, we propose a method that allows to attack up to 18 rounds the design with 8 branches. We also mention the results for the 16-branch design.
Access this chapter
Tax calculation will be finalised at checkout
Purchases are for personal use only
Similar content being viewed by others
References
Camellia home page. https://info.isl.ntt.co.jp/crypt/eng/camellia/
Secure Hash Standard. Federal Information Processing Standard Publication 180–4. US Department of Commerce, National Institute of Standard and Technology, Technical report (2012)
Encryption Algorithm for Computer Data Protection. Technical Report Federal Register 40(52) 12134, National Bureau of Standards, March 1975
Notice of a Proposed Federal Information Processing Data Encryption. Technical Report Federal Register 40(149) 12607, National Bureau of Standards, August 1975
Adams, C., Heys, H., Tavares, S., Wiener, M.: The CAST-256 Encryption Algorithm. Technical report, AES Submission (1998)
Beaulieu, R., Shors, D., Smith, J., Treatman-Clarck, S., Weeks, B., Wingers, L.: The Simon and Speck Families of Lightweight Block Ciphers. Cryptology ePrint archive: 2013/404: Listing for 2013
Berger, T.P., Minier, M., Thomas, G.: Extended generalized feistel networks using matrix representation. In: Lange, T., Lauter, K., Lisoněk, P. (eds.) SAC 2013. LNCS, vol. 8282, pp. 289–305. Springer, Heidelberg (2014)
Burwick, C., Coppersmith, D., DÁvignon, E., Gennaro, R., Halevi, S., Jutla, C., Matyas Jr., S.M., OĆonnor, L., Peyravian, M., Safford, D., Zunic, N.: MARS - a candidate cipher for AES. Technical report, AES Submission (1998)
Hoel, P.G., Port, S.C., Stone, C.J.: Introduction to Probability Theory. Houghton Mifflin Company, Boston (1971)
Hirose, S., Kuwakado, H., Yoshida, H.: SHA-3 Proposal: Lesamnta (2009)
Nachef, V., Volte, E., Patarin, J.: Differential attacks on generalized feistel schemes. In: Abdalla, M., Nita-Rotaru, C., Dahab, R. (eds.) CANS 2013. LNCS, vol. 8257, pp. 1–19. Springer, Heidelberg (2013)
Patarin, J.: Generic attacks on feistel schemes. In: Boyd, C. (ed.) ASIACRYPT 2001. LNCS, vol. 2248, pp. 222–238. Springer, Heidelberg (2001)
Patarin, J., Nachef, V., Berbain, C.: Generic Attacks on Unbalanced Feistel Schemes with Expanding Functions - Extended version. Cryptology ePrint archive: 2007/449: Listing for 2007
Patarin, J., Nachef, V., Berbain, C.: Generic attacks on unbalanced feistel schemes with contracting functions. In: Lai, X., Chen, K. (eds.) ASIACRYPT 2006. LNCS, vol. 4284, pp. 396–411. Springer, Heidelberg (2006)
Patarin, J., Nachef, V., Berbain, C.: Generic attacks on unbalanced feistel schemes with expanding functions. In: Kurosawa, K. (ed.) ASIACRYPT 2007. LNCS, vol. 4833, pp. 325–341. Springer, Heidelberg (2007)
Rivest, R.L., Robshaw, M., Sidney, R., Yin, Y.L.: The RC6 Block Cipher. Technical report, AES Submission (1998)
Rivest, R.L.: A Description of the RC2 Encryption Algorithm. File draft-rivest-rc2desc-00.txt. ftp://ftp.ietf.org/internet-drafts/
Shirai, T., Shibutani, K., Akishita, T., Moriai, S., Iwata, T.: The 128-Bit blockcipher CLEFIA (extended abstract). In: Biryukov, A. (ed.) FSE 2007. LNCS, vol. 4593, pp. 181–195. Springer, Heidelberg (2007)
Volte, E., Nachef, V., Marrière, N.: Automatic Expectation and Variance Computing for Attacks on Feistel Schemes. Cryptology ePrint archive: 2016/136: Listing for 2016
Volte, E., Nachef, V., Patarin, J.: Improved generic attacks on unbalanced feistel schemes with expanding functions. In: Abe, M. (ed.) ASIACRYPT 2010. LNCS, vol. 6477, pp. 94–111. Springer, Heidelberg (2010)
Wood. Method of Cryptographically Transforming Electronic Digital Data from One Form to Another (1991)
Author information
Authors and Affiliations
Corresponding author
Editor information
Editors and Affiliations
Rights and permissions
Copyright information
© 2016 Springer International Publishing AG
About this paper
Cite this paper
Nachef, V., Marrière, N., Volte, E. (2016). Improved Attacks on Extended Generalized Feistel Networks. In: Foresti, S., Persiano, G. (eds) Cryptology and Network Security. CANS 2016. Lecture Notes in Computer Science(), vol 10052. Springer, Cham. https://doi.org/10.1007/978-3-319-48965-0_35
Download citation
DOI: https://doi.org/10.1007/978-3-319-48965-0_35
Published:
Publisher Name: Springer, Cham
Print ISBN: 978-3-319-48964-3
Online ISBN: 978-3-319-48965-0
eBook Packages: Computer ScienceComputer Science (R0)