Abstract
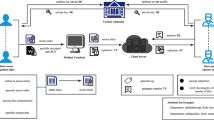
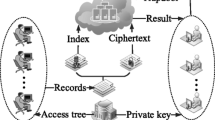
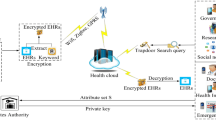
Online personal health record (PHR) enables patients to store their health records at a cloud server and selectively share them with doctors for convenient medical care, and greatly facilitates the storage and sharing of the data. However, there are some challenges, such as risks of privacy exposure, flexible access, rapid ciphertext retrieval and efficient user revocation, impeding the development of PHR. As for solving the above problems, we propose a privacy-preserving personal health record with search and revocation. In our scheme, we obfuscates the attributes exposed in the access policy. Consequently, this avoids the risk that an attacker may guess what kind of disease the patient gets according to the attributes exposed in the access policy. Instead of an exhaustive search with cryptographic calculations, a simple comparison algorithm is adopted to improve the searching efficiency. Furthermore, our scheme supports dynamic user revocation through the cloud reencrypts normal and unnormal ciphertexts according to the revocation list.
Access this chapter
Tax calculation will be finalised at checkout
Purchases are for personal use only
Preview
Unable to display preview. Download preview PDF.
Similar content being viewed by others
References
Sahai, A., &Waters, B. (2005, May). Fuzzy identity-based encryption. In Annual International Conference on the Theory and Applications of Cryptographic Techniques (pp. 457-473). Springer Berlin Heidelberg.
Boneh, D., Di Crescenzo, G., Ostrovsky, R., & Persiano, G. (2004, May). Public key encryption with keyword search. In International Conference on the Theory and Applications of Cryptographic Techniques (pp. 506-522). Springer Berlin Heidelberg.
Dong, Q., Guan, Z., & Chen, Z. (2015, December). Attribute-based Keyword Search Efficiency Enhancement Via an Online/Offline Approach. In Parallel and Distributed Systems (ICPADS), 2015 IEEE 21st International Conference on (pp. 298-305). IEEE.
Koo, D., Hur, J., & Yoon, H. (2013). Secure and efficient data retrieval over encrypted data using attribute-based encryption in cloud storage. Computers & Electrical Engineering, 39(1), 34-46.
Zu, L., Liu, Z., & Li, J. (2014, September). New Ciphertext-Policy Attribute-Based Encryption with Efficient Revocation. In Computer and Information Technology (CIT), 2014 IEEE International Conference on (pp. 281-287). IEEE.
Xie, X., Ma, H., Li, J., & Chen, X. (2013). An Efficient Ciphertext-Policy Attribute-Based Access Control towards Revocation in Cloud Computing. J. UCS, 19(16), 2349-2367.
Xu, Z., & Martin, K. M. (2012, June). Dynamic user revocation and key refreshing for attribute-based encryption in cloud storage. In 2012 IEEE 11th International Conference on Trust, Security and Privacy in Computing and Communications (pp. 844-849). IEEE.
Li, J., & Zhang, L. (2014). Attribute-based keyword search and data access control in cloud. In Computational Intelligence and Security (CIS)(pp. 382-386).
Bethencourt, J., Sahai, A., & Waters, B. (2007, May). Ciphertext-policy attribute-based encryption. In 2007 IEEE symposium on security and privacy (SP’07) (pp. 321-334). IEEE.
Author information
Authors and Affiliations
Corresponding author
Editor information
Editors and Affiliations
Rights and permissions
Copyright information
© 2017 Springer International Publishing AG
About this paper
Cite this paper
Duan, S., Liu, Z., Zhou, P. (2017). A privacy-preserving personal health record with searchability and revocability using attribute-based encryption. In: Barolli, L., Xhafa, F., Yim, K. (eds) Advances on Broad-Band Wireless Computing, Communication and Applications. BWCCA 2016. Lecture Notes on Data Engineering and Communications Technologies, vol 2. Springer, Cham. https://doi.org/10.1007/978-3-319-49106-6_85
Download citation
DOI: https://doi.org/10.1007/978-3-319-49106-6_85
Published:
Publisher Name: Springer, Cham
Print ISBN: 978-3-319-49105-9
Online ISBN: 978-3-319-49106-6
eBook Packages: EngineeringEngineering (R0)