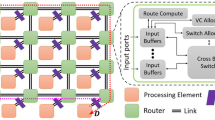
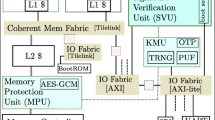
Abstract
A novel approach for mitigation of hardware Trojan in Systems on Chip (SoC) is presented. With the assumption that Trojans can cause harm only when they are activated, the goal is to avoid cumbersome and sometimes destructive pre-fabrication and pre-deployment tests for Trojans in SoCs, by building systems capable of capturing Trojan activation or simply nullifying their effect at run-time to prevent damage to the system. To reach this goal, non-trusted third-party IPs and components off the shelf (COTS) are executed in sandboxes with checkers and virtual resources. While checkers are used to detect run-time activation of Trojans and mitigate potential damage to the system, virtual resources are provided to IPs in the sandbox, thus preventing direct access to physical resources. Our approach was validated with benchmarks from trust-hub.com, a synthetic system on FPGA scenario using the same benchmark. All our results showed a 100% Trojan detection and mitigation, with only a minimal increase in resource overhead and no performance decrease.
Access this chapter
Tax calculation will be finalised at checkout
Purchases are for personal use only
Similar content being viewed by others
References
IEEE standard for property specification language (PSL). IEEE Std 1850–2010 (Revision of IEEE Std 1850–2005) pp. 1–182, April 2010
ARM: Trustzone. http://www.arm.com/products/processors/technologies/trustzone/
Banga, M., Hsiao, M.: A region based approach for the identification of hardware Trojans. In: IEEE International Workshop on Hardware-Oriented Security and Trust, HOST 2008, pp. 40–47, June 2008
Bhunia, S., Abramovici, M., Agrawal, D., Bradley, P., Hsiao, M., Plusquellic, J., Tehranipoor, M.: Protection against hardware trojan attacks: towards a comprehensive solution. IEEE Des. Test 30(3), 6–17 (2013)
Bhunia, S., Hsiao, M., Banga, M., Narasimhan, S.: Hardware trojan attacks: threat analysis and countermeasures. Proc. IEEE 102(8), 1229–1247 (2014)
Çakir, B., Malik, S.: Hardware Trojan detection for gate-level ICS using signal correlation based clustering. In: Proceedings of the 2015 Design, Automation & Test in Europe Conference & Exhibition, DATE 2015, EDA Consortium, San Jose, CA, USA, pp. 471–476 (2015). http://dl.acm.org/citation.cfm?id=2755753.2755860
Chakraborty, R.S., Bhunia, S.: Security against hardware Trojan attacks using key-based design obfuscation. J. Electron. Test. 27(6), 767–785 (2011). http://dx.doi.org/10.1007/s10836-011-5255-2
Forte, D., Bao, C., Srivastava, A.: Temperature tracking: an innovative run-time approach for hardware Trojan detection. In: 2013 IEEE/ACM International Conference on Computer-Aided Design (ICCAD), pp. 532–539, November 2013
Glazberg, Z., Moulin, M., Orni, A., Ruah, S., Zarpas, E.: PSL: beyond hardware verification. In: Ramesh, S., Sampath, P. (eds.) Next Generation Design and Verification Methodologies for Distributed Embedded Control Systems, pp. 245–260. Springer, Netherlands (2007). doi:10.1007/978-1-4020-6254-4_19
Group, O.W: Open verification library (OVL) working group.http://accellera.org/activities/working-groups/ovl
Hategekimana, F., Tbatou, A., Bobda, C., Kamhoua, C.A., Kwiat, K.A.: Hardware isolation technique for IRC-based botnets detection. In: International Conference on ReConFigurable Computing and FPGAs, ReConFig 2015, Riviera Maya, Mexico, 7–9 December 2015, pp. 1–6 (2015). http://dx.doi.org/10.1109/ReConFig.2015.7393319
Lamech, C., Rad, R., Tehranipoor, M., Plusquellic, J.: An experimental analysis of power and delay signal-to-noise requirements for detecting Trojans and methods for achieving the required detection sensitivities. IEEE Trans. Inf. Forensics Secur. 6(3), 1170–1179 (2011)
Mitra, S., Wong, H.S.P., Wong, S.: Stopping hardware Trojans in their tracks. A few adjustments could protect chips against malicious circuitry. http://spectrum.ieee.org/semiconductors/design/stopping-hardware-trojans-in-their-tracks
Pnueli, A.: Special issue semantics of concurrent computation the temporal semantics of concurrent programs. Theoret. Comput. Sci. 13(1), 45–60 (1981). http://www.sciencedirect.com/science/article/pii/0304397581901109
Sengupta, A., Bhadauria, S.: Untrusted third party digital IP cores: power-delay trade-off driven exploration of hardware Trojan secured datapath during high level synthesis. In: Proceedings of the 25th Edition on Great Lakes Symposium on VLSI, GLSVLSI 2015, NY, USA, pp. 167–172 (2015). http://doi.acm.org/10.1145/2742060.2742061
Tehranipoor, M., Koushanfar, F.: A survey of hardware Trojan taxonomy and detection. IEEE Des. Test Comput. 27(1), 10–25 (2010)
Venema, W.: Isolation mechanisms for commodity applications and platforms. Technical report RC24725 (W0901–048), IBM, January 2009
Wei, S., Potkonjak, M.: Scalable hardware Trojan diagnosis. IEEE Trans. Very Large Scale Integr. (VLSI) Syst. 20(6), 1049–1057 (2012)
Xiao, K., Tehranipoor, M.: BISA: built-in self-authentication for preventing hardware trojan insertion. In: 2013 IEEE International Symposium on Hardware-Oriented Security and Trust (HOST), pp. 45–50, June 2013
Zhang, X., Tehranipoor, M.: Case study: detecting hardware Trojans in third-party digital IP cores. In: 2011 IEEE International Symposium on Hardware-Oriented Security and Trust (HOST), pp. 67–70, June 2011
Acknowledgment
This work was in part supported by the Air Force Summer Faculty Fellowship Program (SFFP 2015) at the Air Force Research Lab, Cyber Assurance Branch in Rome, NY. The authors would like to thank the Air Force and Information Institute for all the support they provided during the summer 2015.
Author information
Authors and Affiliations
Corresponding author
Editor information
Editors and Affiliations
Rights and permissions
Copyright information
© 2017 Springer International Publishing AG
About this paper
Cite this paper
Bobda, C., Mead, J., Whitaker, T.J.L., Kamhoua, C., Kwiat, K. (2017). Hardware Sandboxing: A Novel Defense Paradigm Against Hardware Trojans in Systems on Chip. In: Wong, S., Beck, A., Bertels, K., Carro, L. (eds) Applied Reconfigurable Computing. ARC 2017. Lecture Notes in Computer Science(), vol 10216. Springer, Cham. https://doi.org/10.1007/978-3-319-56258-2_5
Download citation
DOI: https://doi.org/10.1007/978-3-319-56258-2_5
Published:
Publisher Name: Springer, Cham
Print ISBN: 978-3-319-56257-5
Online ISBN: 978-3-319-56258-2
eBook Packages: Computer ScienceComputer Science (R0)