Abstract
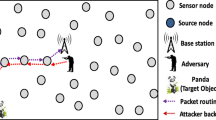
Abundant experiments have shown that phantom source nodes cannot leave far away from the real source node. In this paper, we propose a novel position tracking based source location privacy (PTSLP) protection scheme for wireless sensor networks (WSNs). First, we construct a phantom area in order to make phantom source nodes being far from the real source node. Secondly, we combine shortest path routing and random routing to forward packets to sink node rather than deviating from sink node. Then, we make every packet pass through a special area called trace cost area which consists of many sensor nodes with different weights in different areas and finally reach the ring around sink node. Compared with SLP-E, which fails to take overlapping path into consideration, our proposed scheme can reduce overlapping path. Simulation results show that PTSLP can increase safety time and enhance source location privacy in WSNs.
Access this chapter
Tax calculation will be finalised at checkout
Purchases are for personal use only
Similar content being viewed by others
References
Zhu, C., Leung, V.C.M., Shu, L., Ngai, E.C.-H.: Green Internet of Things for smart world. IEEE Access. 3, 2151–2162 (2015)
Han, G., Jiang, J., Shu, L., Niu, J., Chao, H.C.: Managements and applications of trust in wireless sensor networks: a survey. J. Comput. Syst. Sci. 80, 602–617 (2014)
Han, G., Jiang, J., Zhang, C., Duong, T.Q., Guizani, M., Karagiannidis, G.K.: A survey on mobile anchor node assisted localization in wireless sensor networks. IEEE Commun. Surv. Tutor. 18, 2220–2243 (2016)
Wan, L., Han, G., Shu, L., Feng, N., Zhu, C., Lloret, J.: Distributed parameter estimation for mobile wireless sensor network based on cloud computing in battlefield surveillance system. IEEE Access. 3, 1729–1739 (2015)
Zhu, C., Yang, L.T., Shu, L., Leung, V.C.M., Hara, T., Nishio, S.: Insights of top-k query in duty-cycled wireless sensor networks. IEEE Trans. Ind. Electron. 62, 1317–1328 (2015)
Han, G., Liu, L., Jiang, J., Shu, L., Hancke, G.: Analysis of energy-efficient connected target coverage algorithms for industrial wireless sensor networks. IEEE Trans. Ind. Inform. 13, 135–143 (2015)
Han, G., Dong, Y., Guo, H., Shu, L., Wu, D.: Cross-layer optimized routing in wireless sensor networks with duty-cycle and energy harvesting. Wirel. Commun. Mob. Comput. 15, 1957–1981 (2015)
Peng, H., Chen, H., Hang, X., Fan, Y., Li, C.P., Li, D.: Location privacy preservation in wireless sensor networks. J. Softw. 26, 617–639 (2015)
Chen, H., Wei, L.: On protecting end-to-end location privacy against local eavesdropper in wireless sensor networks. Pervasive Mob. Comput. 16, 36–50 (2014). Elsevier B.V
Li, N., Zhang, N., Das, S., Thuraisingham, B.: A state-of-the-art survey. Ad Hoc Netw. 7, 1501–1514 (2009)
Zhu, C., Yang, L.T., Shu, L., Leung, V.C.M., Rodrigues, J., Wang, L.: Sleep scheduling for geographic routing in duty-cycled mobile sensor networks. IEEE Trans. Ind. Electron. 61, 6346–6355 (2014)
Jia, D., Chi, Y.: REAL: a reciprocal protocol for location privacy in wireless sensor networks. IEEE Trans. Dependable Secur. Comput. 12, 458–471 (2015)
Conti, M., Willemsen, J., Crispo, B.: Providing source location privacy in wireless sensor networks: a survey. IEEE Commun. Surv. Tutor. 15, 1238–1280 (2013)
Jhumka, A., Bradbury, M., Leeke, M.: Fake source-based source location privacy in wireless sensor networks. Concurr. Comput. Pract. Exp. 27, 189–203 (2014)
Chen, J., Lin, Z., Hu, Y., Wang, B.: Hiding the source based on limited flooding for sensor networks. Sensors 15, 29129–29148 (2015)
He, W., Liu, X., Nguyen, H., Nahrstedt, K.: A cluster-based protocol to enforce integrity and preserve privacy in data aggregation. In: 29th IEEE International Conference on Distributed Computing Systems Workshops (ICDCS Workshops 2009), pp. 14–19. IEEE, Los Alamitos. IEEE Computer Society (2009)
Lu, M., Zhao, Z., Tang, X., Zhou, J.: Research on phantom routing to provide source-location privacy in wireless sensor network. Inf. Technol. 10, 72–79 (2012)
Yao, J., Hao, X., Wen, G.: Location privacy protecting in wireless sensor networks. Chin. J. Sens. Actuators 21, 1437–1441 (2008)
Chen, J., Fang, B., Yin, L., Su, S.: A source-location privacy preservation protocol in wireless sensor networks using source-based restricted flooding. Chin. J. Comput. 33, 1736–1749 (2010)
Zhao, Z., Liu, Y., Zhang, F., Zhou, J., Zhang, P.: Research on source location privacy routing based on angle and probability in wireless sensor networks. J. Shandong Univ. (Nat. Sci.) 48, 1–9 (2013)
Zhang, Y., Xu, Y., Wu, X.: Enhanced source-location privacy preservation protocol using random angle. Comput. Eng. Appl. 52, 1–8 (2015)
Liu, X., Li, J., Li, B.: Source-location privacy protocol based on the minimum cost routing. Chin. J. Sens. Actuators 27, 394–400 (2014)
Wang, W., Chen, L., Wang, J.: A source-location privacy protocol in WSN based on locational angle. In: Proceedings of the IEEE International Conference Communications, pp. 1630–1634. IEEE Press, Beijing (2008)
Li, Y., Ren, J., Wu, J.: Quantitative measurement and design of source-location privacy schemes for wireless sensor networks. IEEE Trans. Parallel Distrib. Syst. 23, 1302–1311 (2012)
Acknowledgement
The work is supported by “Qing Lan Project” and “the National Natural Science Foundation of China under Grant No. 61572172 and No. 61602152” and supported by “the Fundamental Research Funds for the Central Universities, No. 2016B10714 and No. 2016B03114 and supported by “Changzhou Sciences and Technology Program, No. CE20165023 and No. CE20160014”.
Author information
Authors and Affiliations
Corresponding author
Editor information
Editors and Affiliations
Rights and permissions
Copyright information
© 2017 Springer International Publishing AG
About this paper
Cite this paper
Wang, H., Han, G., Zhu, C., Chan, S. (2017). PTSLP: Position Tracking Based Source Location Privacy for Wireless Sensor Networks. In: Hancke, G., Markantonakis, K. (eds) Radio Frequency Identification and IoT Security. RFIDSec 2016. Lecture Notes in Computer Science(), vol 10155. Springer, Cham. https://doi.org/10.1007/978-3-319-62024-4_2
Download citation
DOI: https://doi.org/10.1007/978-3-319-62024-4_2
Published:
Publisher Name: Springer, Cham
Print ISBN: 978-3-319-62023-7
Online ISBN: 978-3-319-62024-4
eBook Packages: Computer ScienceComputer Science (R0)