Abstract
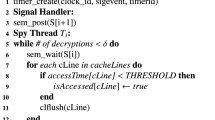
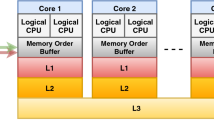
While the AES algorithm is regarded as secure, many implementations of AES are prone to cache side-channel attacks. The lookup tables traditionally used in AES implementations for storing precomputed results provide speedup for encryption and decryption. How such lookup tables are used is known to affect the vulnerability to side channels, but the concrete effects in actual AES implementations are not yet sufficiently well understood. In this article, we analyze and compare multiple off-the-shelf AES implementations wrt. their vulnerability to cache side-channel attacks. By applying quantitative program analysis techniques in a systematic fashion, we shed light on the influence of implementation techniques for AES on cache-side-channel leakage bounds.
Access this chapter
Tax calculation will be finalised at checkout
Purchases are for personal use only
Similar content being viewed by others
Notes
- 1.
We round all leakage bounds up to one decimal place and truncate them to the maximum leakage of 256 bit (128 bit message and 128 bit key) throughout the article.
- 2.
To support the reader in reading such diagrams, we connect the leakage bounds computed for adjacent cache sizes and the same attacker model by dashed lines.
- 3.
For \(\mathrm {LibTomCrypt}\) AES and 2 KB cache size, the analysis ran out of memory.
- 4.
- 5.
This can be realized using static cache locking if the cache size exceeds the total size of tables. One could consider dynamic cache locking [27] if the cache is too small.
- 6.
The sequential composition of the functions crypto_stream_beforenm (beforenm.c) and crypto_stream_xor_afternm (xor_afternm.c) from NaCl in version 20110221.
References
Acıiçmez, O., Koç, Ç.K.: Trace-driven cache attacks on AES (short paper). In: Ning, P., Qing, S., Li, N. (eds.) ICICS 2006. LNCS, vol. 4307, pp. 112–121. Springer, Heidelberg (2006). doi:10.1007/11935308_9
A.R.M Ltd.: ARM buys Leading IoT Security Company Offspark as it Expands its mbed Platform (2015). https://www.arm.com/about/newsroom/arm-buys-leading-iot-security-company-offspark-as-it-expands-its-mbed-platform.php. Accessed 11 Feb 2017
A.R.M Ltd.: mbed TLS (Version 2.2.1-gpl) (2016). https://tls.mbed.org/download/mbedtls-2.2.1-gpl.tgz. Accessed 28 Jul 2016
Backes, M., Köpf, B., Rybalchenko, A.: Automatic discovery and quantification of information leaks. In: S&P, pp. 141–153 (2009)
Bernstein, D.J.: Cache-timing attacks on AES. Technical report, University of Illinois at Chicago (2005)
Bernstein, D.J., Lange, T., Schwabe, P.: The security impact of a new cryptographic library. In: Hevia, A., Neven, G. (eds.) LATINCRYPT 2012. LNCS, vol. 7533, pp. 159–176. Springer, Heidelberg (2012). doi:10.1007/978-3-642-33481-8_9
Brickell, E., Graunke, G., Neve, M., Seifert, J.: Software mitigations to hedge AES against cache-based software side channel vulnerabilities. IACR Cryptology ePrint Archive, pp. 1–17 (2006)
Committee on National Security Systems: CNSS Policy No. 15: National Information Assurance Policy on the Use of Public Standards for the Secure Sharing of Information Among National Security Systems (2016). https://www.cnss.gov/CNSS/openDoc.cfm?1858/J1y8IPFvRRvn+ZZBw==. Accessed 29 Dec 2016
Crane, S., Homescu, A., Brunthaler, S., Larsen, P., Franz, M.: Thwarting cache side-channel attacks through dynamic software diversity. In: NDSS (2015)
Daemen, J., Rijmen, V.: AES submission document on Rijndael, Version 2 (1999). http://csrc.nist.gov/archive/aes/rijndael/Rijndael.pdf
Doychev, G., Feld, D., Köpf, B., Mauborgne, L., Reineke, J.: CacheAudit: a tool for the static analysis of cache side channels. In: USENIX Security, pp. 431–446 (2013)
Doychev, G., Köpf, B., Mauborgne, L., Reineke, J.: Cacheaudit: a tool for the static analysis of cache side channels. ACM Trans. Inf. Syst. Secur. 18, 4:1–4:32 (2015)
Barker, E.: Nist special publication 800–57 part 1, revision 4: Recommendation for key management - part 1: General (2016). http://nvlpubs.nist.gov/nistpubs/SpecialPublications/NIST.SP.800-57pt1r4.pdf
Ge, Q., Yarom, Y., Cock, D., Heiser, G.: A survey of microarchitectural timing attacks and countermeasures on contemporary hardware. J. Cryptogr. Eng., 1–27 (2016)
Gullasch, D., Bangerter, E., Krenn, S.: Cache games - bringing access-based cache attacks on AES to practice. In: S&P, pp. 490–505 (2011)
Heusser, J., Malacaria, P.: Quantifying information leaks in software. In: ACSAC, pp. 261–269 (2010)
Corporation, I.: Intel®64 and IA-32 Architectures Optimization Reference Manual. Order Number: 248966–032 (2016)
Irazoqui, G., Eisenbarth, T., Sunar, B.: S$A: a shared cache attack that works across cores and defies VM sandboxing - and its application to AES. In: S & P, pp. 591–604 (2015)
Irazoqui, G., Inci, M.S., Eisenbarth, T., Sunar, B.: Wait a minute! a fast, cross-VM attack on AES. In: Stavrou, A., Bos, H., Portokalidis, G. (eds.) RAID 2014. LNCS, vol. 8688, pp. 299–319. Springer, Cham (2014). doi:10.1007/978-3-319-11379-1_15
Kim, T., Peinado, M., Mainar-Ruiz, G.: STEALTHMEM: system-level protection against cache-based side channel attacks in the cloud. In: USENIX Security, pp. 189–204 (2012)
Kong, J., Aciiçmez, O., Seifert, J.P., Zhou, H.: Deconstructing new cache designs for thwarting software cache-based side channel attacks. In: CSAW, pp. 25–34 (2008)
Kong, J., Aciiçmez, O., Seifert, J.P., Zhou, H.: Hardware-software integrated approaches to defend against software cache-based side channel attacks. In: HPCA, pp. 393–404 (2009)
Köpf, B., Rybalchenko, A.: Approximation and randomization for quantitative information-flow analysis. In: CSF, pp. 3–14 (2010)
Käsper, E., Schwabe, P.: Faster and timing-attack resistant AES-GCM. In: Clavier, C., Gaj, K. (eds.) CHES 2009. LNCS, vol. 5747, pp. 1–17. Springer, Heidelberg (2009). doi:10.1007/978-3-642-04138-9_1
Lipp, M., Gruss, D., Spreitzer, R., Maurice, C., Mangard, S.: ARMageddon: cache attacks on mobile devices. In: USENIX Security, pp. 549–564 (2016)
Massey, J.L.: Guessing and entropy. In: ISIT, p. 204 (1994)
Mittal, S.: A survey of techniques for cache locking. ACM Trans. Des. Automat. Electron. Syst., 49:1–49:24 (2016)
Möller, N.: Nettle (Version 3.2) (2016). https://ftp.gnu.org/gnu/nettle/nettle-3.2.tar.gz. Accessed 28 Jul 2016
Newsome, J., McCamant, S., Song, D.: Measuring channel capacity to distinguish undue influence. In: PLAS, pp. 73–85 (2009)
OpenSSL Software Foundation: OpenSSL (Version 1.0.1t) (2016). https://www.openssl.org/source/openssl-1.0.1t.tar.gz. Accessed 28 Jul 2016
OpenVPN Technologies, Inc. HOWTO (2017). https://openvpn.net/index.php/open-source/documentation/howto.html. Accessed 16 Feb 2017
Osvik, D.A., Shamir, A., Tromer, E.: Cache attacks and countermeasures: the case of AES. In: Pointcheval, D. (ed.) CT-RSA 2006. LNCS, vol. 3860, pp. 1–20. Springer, Heidelberg (2006). doi:10.1007/11605805_1
Page, D.: Theoretical Use of Cache Memory as a Cryptanalytic Side-Channel. IACR Cryptology ePrint Archive, pp. 1–23 (2002)
Page, D.: Defending Against Cache-Based Side-Channel Attacks. Information Security Technical Report, pp. 30–44 (2003)
Page, D.: Partitioned cache architecture as a side-channel defence mechanism. IACR Cryptology ePrint Archive, pp. 1–14 (2005)
Pasareanu, C.S., Phan, Q., Malacaria, P.: Multi-run side-channel analysis using symbolic execution and max-SMT. In: CSF, pp. 387–400 (2016)
libtom projects: LibTomCrypt (Version 1.17) (2010). https://github.com/libtom/libtomcrypt/archive/1.17.tar.gz. Accessed 28 Jul 2016
Smith, G.: On the foundations of quantitative information flow. In: FOSSACS, pp. 288–302 (2009)
Tiri, K., Acıiçmez, O., Neve, M., Andersen, F.: An analytical model for time-driven cache attacks. In: Biryukov, A. (ed.) FSE 2007. LNCS, vol. 4593, pp. 399–413. Springer, Heidelberg (2007). doi:10.1007/978-3-540-74619-5_25
Tromer, E., Osvik, D.A., Shamir, A.: Efficient cache attacks on AES, and countermeasures. J. Cryptology 23(1), 37–71 (2010)
Wang, Z., Lee, R.B.: A novel cache architecture with enhanced performance and security. In: MICRO, pp. 83–93 (2008)
Yarom, Y., Falkner, K.: FLUSH+RELOAD: a high resolution, low noise, L3 cache side-channel attack. In: USENIX Security, pp. 719–732 (2014)
Acknowledgements
We thank Clémentine Maurice and the anonymous reviewers for helpful comments. We also thank Artem Starostin for inspiring discussions in the initial phase of this project and Xucheng Yin for his contributions to CacheAudit. This work has been funded by the DFG as part of the project Secure Refinement of Cryptographic Algorithms (E3) within the CRC 1119 CROSSING and was supported by Ramón y Cajal grant RYC-2014-16766, Spanish projects TIN2012-39391-C04-01 StrongSoft and TIN2015-70713-R DEDETIS, and Madrid regional project S2013/ICE-2731 N-GREENS.
Author information
Authors and Affiliations
Corresponding authors
Editor information
Editors and Affiliations
Rights and permissions
Copyright information
© 2017 Springer International Publishing AG
About this paper
Cite this paper
Mantel, H., Weber, A., Köpf, B. (2017). A Systematic Study of Cache Side Channels Across AES Implementations. In: Bodden, E., Payer, M., Athanasopoulos, E. (eds) Engineering Secure Software and Systems. ESSoS 2017. Lecture Notes in Computer Science(), vol 10379. Springer, Cham. https://doi.org/10.1007/978-3-319-62105-0_14
Download citation
DOI: https://doi.org/10.1007/978-3-319-62105-0_14
Published:
Publisher Name: Springer, Cham
Print ISBN: 978-3-319-62104-3
Online ISBN: 978-3-319-62105-0
eBook Packages: Computer ScienceComputer Science (R0)