Abstract
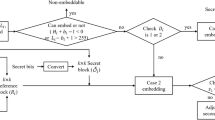
This paper proposes an efficient reversible information hiding method based on AMBTC compressed images. At present, most digital images are stored and transmitted in compressed form, so research and development of such a scheme is necessary. Hong et al. proposed a reversible information hiding based approach based on AMBTC compression of images to provide considerable embedding capacity and effectively reduce the bit-rate. However, it did not carry out a detailed categorization of the error value or adopt the most suitable method for category information encoding, where error value is the difference of the original quantization value and the prediction quantization value. So there’s possibility to reduce the bit-rate. In this paper, we propose an Improved Centralized Error Division (ICED) technique to conduct a more detailed categorization of the error value. In addition, we also adopt an optimal Huffman code to encode category information, so as to further reduce the bit-rate. Our experimental results show that our proposed approach has an equal embedding capacity as Hong et al.’s method and is higher than other relevant work. In addition, the proposed scheme has a lower bit-rate than Hong et al.’s method.
Access this chapter
Tax calculation will be finalised at checkout
Purchases are for personal use only
Similar content being viewed by others
References
Yuan, C., Xia, Z., Sun, X.: Coverless image steganography based on SIFT and BOF. J. Internet Technol. 18(2), 435–442 (2017)
Chen, X., Chen, S., Wu, Y.: Coverless information hiding method based on the Chinese character encoding. J. Internet Technol. 18(2), 313–320 (2017)
Li, J., Li, X., et al.: Segmentation-based image copy-move forgery detection scheme. IEEE Trans. Inf. Forensics Secur. 10(3), 507–518 (2015)
Zhou, Z., Wang, Y., et al.: Effective and efficient global context verification for image copy detection. IEEE Trans. Inf. Forensics Secur. 12(1), 48–63 (2017)
Guo, P., et al.: A variable threshold-value authentication architecture for wireless mesh networks. J. Internet Technol. 15(6), 929–935 (2014)
Xie, S., Wang, Y.: Construction of tree network with limited delivery latency in homogeneous wireless sensor networks. Wireless Pers. Commun. 78(1), 231–246 (2014)
Chen, B., Shu, H., et al.: Color image analysis by quaternion zernike moments. J. Math. Imaging Vis. 51(1), 124–144 (2015)
Wang, B., Gu, X., Ma, L., Yan, S.: Temperature error correction based on BP neural network in meteorological WSN. Int. J. Sensor Netw. 23(4), 265–278 (2017)
Tsai, C.L., Chiang, H.F., et al.: Reversible data hiding and lossless reconstruction of binary images using pair-wise logical computation mechanism. Pattern Recogn. 38(11), 1993–2006 (2005)
Shiu, C.W., Chen, Y.C., Hong, W.: Encrypted image-based reversible data hiding with public key cryptography from difference expansion. Signal Process. Image Commun. 39, 226–233 (2015)
Barton, J.M.: Method and apparatus for embedding authentication information within digital data. US, US6523114 (2003)
Hong, W., et al.: An efficient reversible data hiding method for AMBTC compressed images. Multimedia Tools Appl. 76(4), 5441–5460 (2016)
Chen, J., et al.: Steganography for BTC compressed images using no distortion technique. Imaging Sci. J. 58(4), 177–185 (2010)
Sun, W., et al.: High performance reversible data hiding for block truncation coding; compressed images. Signal Image Video Process. 7(2), 297–306 (2013)
Acknowledgements
This research work is partly supported by National Natural Science Foundation of China (61502009, U1536109), China Postdoctoral Science Foundation (2016M591650), Anhui Provincial Natural Science Foundation (1508085SQF216) and Key Program for Excellent Young Talents in Colleges and Universities of Anhui Province (gxyqZD2016011).
Author information
Authors and Affiliations
Corresponding author
Editor information
Editors and Affiliations
Rights and permissions
Copyright information
© 2017 Springer International Publishing AG
About this paper
Cite this paper
Puyang, Y., Yin, Z., Feng, G., Abel, A.K. (2017). An Improved Reversible Information Hiding Scheme Based on AMBTC Compressed Images. In: Sun, X., Chao, HC., You, X., Bertino, E. (eds) Cloud Computing and Security. ICCCS 2017. Lecture Notes in Computer Science(), vol 10602. Springer, Cham. https://doi.org/10.1007/978-3-319-68505-2_5
Download citation
DOI: https://doi.org/10.1007/978-3-319-68505-2_5
Published:
Publisher Name: Springer, Cham
Print ISBN: 978-3-319-68504-5
Online ISBN: 978-3-319-68505-2
eBook Packages: Computer ScienceComputer Science (R0)