Abstract
Keeping correct and informative log files is crucial for system maintenance, security and forensics. Cryptographic logging schemes offer integrity checks that protect a log file even in the case where an attacker has broken into the system.
A relatively recent feature of these schemes is resistance against truncations, i.e. the deletion and/or replacement of the end of the log file. This is especially relevant as system intruders are typically interested in manipulating the later log entries that point towards their attack. However, there are not many schemes that are resistant against truncating the log file. Those that are have at least one of the following disadvantages: They are memory intensive (they store at least one signature per log entry), or fragile (i.e. a single error in the log renders the signature invalid and useless in determining where the error occurred).
We obtain a publicly-verifiable secure logging scheme that is simultaneously robust, space-efficient and truncation secure with provable security under simple assumptions. Our generic construction uses forward-secure signatures, in a plain and a sequential aggregate variant, where the latter is additionally fault-tolerant, as recently formalized by Hartung et al. [9]. Fault-tolerant schemes can cope with a number of manipulated log entries (bounded a priori) and offer strong robustness guarantees while still retaining space efficiency. Our implementation and the accompanying performance measurements confirm the practicality of our scheme.
G. Hartung—The project underlying this report was supported by the German Federal Ministry of Education and Research under Grant No. 01|S15035A. The responsibility for the contents of this publication lies with the author.
A. Koch, J. Koch and D. Hartmann—This work was supported by the German Federal Ministry of Education and Research within the framework of the project KASTEL_IoE in the Competence Center for Applied Security Technology (KASTEL).
Access this chapter
Tax calculation will be finalised at checkout
Purchases are for personal use only
Notes
- 1.
The terms “claim” and “claim sequence” are borrowed from [9]. However, we have added an epoch index i to each claim, because we are considering forward security in this work.
- 2.
This security notion is slightly weaker with respect to the non-triviality of forgeries than the one for sequential aggregate signatures by Lysyanskaya et al. [19]. There, they allow for all messages in \(C^*\) to be already queried before, but in different order. However, our notion additionally considers forward security.
- 3.
forward-secure existentially unforgeable under chosen log message attacks.
- 4.
Remember that we assume that m and i can be uniquely derived from \(m \mathop {\Vert }i\), which implies that the claims
 and
and 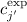 also differ after concatenating \(j'\) to their messages. Since \(j'\) is also only used once, the claim
also differ after concatenating \(j'\) to their messages. Since \(j'\) is also only used once, the claim  cannot become equal to any other claim of
cannot become equal to any other claim of 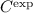 after this concatenation, either.
after this concatenation, either.
References
Anderson, R.: Invited lecture. In: 4th ACM Computer and Communications Security (1997)
Bellare, M., Miner, S.K.: A forward-secure digital signature scheme. In: Wiener, M. (ed.) CRYPTO 1999. LNCS, vol. 1666, pp. 431–448. Springer, Heidelberg (1999). doi:10.1007/3-540-48405-1_28
Bellare, M., Yee, B.: Forward integrity for secure audit logs. Technical report, Computer Science and Engineering Department, University of California at San Diego (1997)
Boneh, D., Gentry, C., Lynn, B., Shacham, H.: Aggregate and verifiably encrypted signatures from bilinear maps. In: Biham, E. (ed.) EUROCRYPT 2003. LNCS, vol. 2656, pp. 416–432. Springer, Heidelberg (2003). doi:10.1007/3-540-39200-9_26
Bowers, K.D., Hart, C., Juels, A., Triandopoulos, N.: PillarBox: combating next-generation malware with fast forward-secure logging. In: Stavrou, A., Bos, H., Portokalidis, G. (eds.) RAID 2014. LNCS, vol. 8688, pp. 46–67. Springer, Cham (2014). doi:10.1007/978-3-319-11379-1_3
Boyen, X., Shacham, H., Shen, E., Waters, B.: Forward-secure signatures with untrusted update. In: Juels, A., Wright, R.N., di Vimercati, S.D.C. (eds.) CCS 2006, pp. 191–200. ACM (2006). doi:10.1145/1180405.1180430
Crosby, S.A., Wallach, D.S.: Efficient data structures for tamper- evident logging. In: Monrose, F. (ed.) USENIX 2009, pp. 317–334. USENIX Association (2009). http://www.usenix.org/events/sec09/tech/full_papers/crosby.pdf
Hartung, G.: Secure audit logs with verifiable excerpts. In: Sako, K. (ed.) CT-RSA 2016. LNCS, vol. 9610, pp. 183–199. Springer, Cham (2016). doi:10.1007/978-3-319-29485-8_11
Hartung, G., Kaidel, B., Koch, A., Koch, J., Rupp, A.: Fault-tolerant aggregate signatures. In: Cheng, C.-M., Chung, K.-M., Persiano, G., Yang, B.-Y. (eds.) PKC 2016. LNCS, vol. 9614, pp. 331–356. Springer, Heidelberg (2016). doi:10.1007/978-3-662-49384-7_13
Holt, J.E.: Logcrypt: forward security and public verification for secure audit logs In: Buyya, R., Ma, T., Safavi-Naini, R., Steketee, C., Susilo, W. (eds.) AusGrid 2006 and AISW 2006. CRPIT, vol. 54, pp. 203–211. Australian Computer Society (2006). doi:10.1145/1151828.1151852
Intel Corporation: 2nd Generation Intel Core Mobile Processor Datasheet, vol. 1, September 2012. https://www-ssl.intel.com/content/www/us/en/processors/core/2nd-gen-core-family-mobile-vol-1-datasheet.html. Accessed 29 May 2017
Intel Corporation: Intel Core i5–2430M Processor Specification. https://ark.intel.com/products/53450/Intel-Core-i5-2430M-Processor-3M-Cache-up-to-3_00-GHz. Accessed 29 May 2017
Itkis, G., Reyzin, L.: Forward-secure signatures with optimal signing and verifying. In: Kilian, J. (ed.) CRYPTO 2001. LNCS, vol. 2139, pp. 332–354. Springer, Heidelberg (2001). doi:10.1007/3-540-44647-8_20
Kautz, W.H., Singleton, R.C.: Nonrandom binary superimposed codes. IEEE Trans. Inf. Theor. 10(4), 363–377 (1964). doi:10.1109/TIT.1964.1053689
Krawczyk, H.: Simple forward-secure signatures from any signature scheme. In: Gritzalis, D., Jajodia, S., Samarati, P. (eds.) CCS 2000, pp. 108–115. ACM (2000). doi:10.1145/352600.352617
Kumar, R., Rajagopalan, S., Sahai, A.: Coding constructions for blacklisting problems without computational assumptions. In: Wiener, M. (ed.) CRYPTO 1999. LNCS, vol. 1666, pp. 609–623. Springer, Heidelberg (1999). doi:10.1007/3-540-48405-1_38
Lu, S., Ostrovsky, R., Sahai, A., Shacham, H., Waters, B.: Sequential aggregate signatures, multisignatures, and verifiably encrypted signatures without random oracles. J. Crypt. 26(2), 340–373 (2013). doi:10.1007/s00145-012-9126-5
Lynn, B.: The pairing-based crypto library. https://crypto.stanford.edu/pbc/. Accessed 29 May 2017
Lysyanskaya, A., Micali, S., Reyzin, L., Shacham, H.: Sequential aggregate signatures from trapdoor permutations. In: Cachin, C., Camenisch, J.L. (eds.) EUROCRYPT 2004. LNCS, vol. 3027, pp. 74–90. Springer, Heidelberg (2004). doi:10.1007/978-3-540-24676-3_5
Ma, D.: Practical forward secure sequential aggregate signatures. In: Abe, M., Gligor, V.D. (eds.) ASIACCS 2008, pp. 341–352. ACM (2008). doi:10.1145/1368310.1368361
Ma, D., Tsudik, G.: A new approach to secure logging. In: Atluri, V. (ed.) DBSec 2008. LNCS, vol. 5094, pp. 48–63. Springer, Heidelberg (2008). doi:10.1007/978-3-540-70567-3_4
Ma, D., Tsudik, G.: A new approach to secure logging. ACM Trans. Storage (TOS) 5(1) (2009). doi:10.1145/1502777.1502779
Ma, D., Tsudik. G.: Extended abstract: forward-secure sequential aggregate authentication. In: S&P 2007, pp. 86–91. IEEE Computer Society (2007). doi:10.1109/SP.2007.18
Schneier, B., Kelsey, J.: Cryptographic support for secure logs on untrusted machines. In: Rubin, A.D. (ed.) Proceedings of USENIX. USENIX Association (1998). https://www.usenix.org/conference/7th-usenix-security-symposium/cryptographic-support-securelogs-untrusted-machines
Shoup, V.: NTL: a library for doing number theory. http://shoup.net/ntl/. Accessed 29 May 2017
Author information
Authors and Affiliations
Corresponding authors
Editor information
Editors and Affiliations
A Implementation Details
A Implementation Details
This section gives details about our implementation of the scheme from Sect. 4.1. Our implementation is written in C++11, and will be made available under a free software license. For the BM-FSS scheme, we chose a modulus size of 1024 bits, roughly equivalent to a security level of 80 bit. The BGLS scheme was instantiated using elliptic curve groups 160 bits, and the base field had 1024 bits. We used an instantiation of the cover-free family based on polynomials, described in [16]. For a CFF supporting \(n = 100\), 1000, and 10000 messages, we chose the field size \(q = 5\), 11, and 23, respectively, and fixed the polynomial degree at \(k = 2\). This led to \(d = 2, 5\) and 11, respectively. (The resulting CFFs were slightly larger than required: They supported 125, 1331, and 12167 messages, respectively.) Whenever a hash function was needed, we used SHA-256. We used a constant string of 200 bytes for all messages.
Our experiments were conducted on a laptop computer with an Intel Core i5-2430M CPU [12] with a clock rate of 2.4 GHz. (Our implementation is not parallelized and therefore did not make use of the additional processor cores.) The processor has private (per-core) caches of 128 KB (Level 1) and 512 KB (Level 2), and a shared Level 3 Cache of 3072 KB [11, Sect. 1.1] The system was equipped with 5.7 GiB of RAM and running a 64-bit version desktop version of the Fedora 23 GNU/Linux operating system, equipped with Linux Kernel version 4.4.9-300. All code was compiled with the GNU C Compiler (version 5.3.1) and optimization level set to -O2. We used Shoups NTL library [25] (version 9.4.0) for the implementation of the BM-FSS scheme and the PBC library [18] (version 0.5.14) for the implementation of the BGLS-FS-SAS scheme.
Rights and permissions
Copyright information
© 2017 Springer International Publishing AG
About this paper
Cite this paper
Hartung, G., Kaidel, B., Koch, A., Koch, J., Hartmann, D. (2017). Practical and Robust Secure Logging from Fault-Tolerant Sequential Aggregate Signatures. In: Okamoto, T., Yu, Y., Au, M., Li, Y. (eds) Provable Security. ProvSec 2017. Lecture Notes in Computer Science(), vol 10592. Springer, Cham. https://doi.org/10.1007/978-3-319-68637-0_6
Download citation
DOI: https://doi.org/10.1007/978-3-319-68637-0_6
Published:
Publisher Name: Springer, Cham
Print ISBN: 978-3-319-68636-3
Online ISBN: 978-3-319-68637-0
eBook Packages: Computer ScienceComputer Science (R0)


 and
and 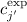 also differ after concatenating
also differ after concatenating  cannot become equal to any other claim of
cannot become equal to any other claim of 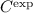 after this concatenation, either.
after this concatenation, either.