Abstract
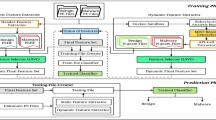
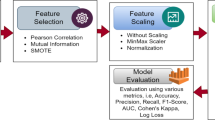
With the development of software security technology, more and more malicious programs constantly uses new confusion and feature hiding techniques, the malware detection technology need to upgrade urgently. This paper presents a malware detection method based on sandbox, binary instrumentation and multidimensional feature extraction. We introduced the design and implementation of sandbox, feature extractor and the classifier. Finally, we merged multiple models and get a pretty well classifier for the malware detection.
Access this chapter
Tax calculation will be finalised at checkout
Purchases are for personal use only
Similar content being viewed by others
References
Gandotra, E., Bansal, D., Sofat, S.: Malware analysis and classification: a survey. J. Inf. Secur. 2014 (2014)
Baldangombo, U., Jambaljav, N., Horng, S.J.: A static malware detection system using data mining methods. arXiv preprint arXiv:1308.2831 (2013)
Divandari, H., Pechaz, B., Jahan, M.V.: Malware detection using Markov Blanket based on opcode sequences. In: International Congress on Technology, Communication and Knowledge (ICTCK) 2015, pp. 564–569. IEEE (2015)
Lee, J., Im, C., Jeong, H.: A study of malware detection and classification by comparing extracted strings. In: Proceedings of the 5th International Conference on Ubiquitous Information Management and Communication, p. 75. ACM (2011)
Xiao, H., Stibor, T.: A supervised topic transition model for detecting malicious system call sequences. In: Proceedings of the 2011 Workshop on Knowledge Discovery, Modeling and Simulation, pp. 23–30. ACM (2011)
Gui, X., Liu, J., Chi, M., et al.: Analysis of malware application based on massive network traffic. China Commun. 13(8), 209–221 (2016)
Alazab, M., Venkatraman, S., Watters, P., et al.: Zero-day malware detection based on supervised learning algorithms of API call signatures. In: Proceedings of the Ninth Australasian Data Mining Conference, vol. 121, pp. 171–182. Australian Computer Society, Inc. (2011)
Cui, B., Wang, F., Guo, T., et al.: Flowwalker: a fast and precise off-line taint analysis framework. In: Fourth International Conference on Emerging Intelligent Data and Web Technologies (EIDWT), 2013, pp. 583–588. IEEE (2013)
Jingling, Z., Shilei, C., Mengchen, C.A.O., et al.: Malware algorithm recognition based on offline instruction-flow analyse. J. Tsinghua Univ. (Sci. Technol.) 65(5), 484–492 (2016)
Cepeda, C., Tien, D.L.C., Ordóñez, P.: Feature selection and improving classification performance for malware detection. In: IEEE International Conferences on Big Data and Cloud Computing (BDCloud), Social Computing and Networking (SocialCom), Sustainable Computing and Communications (SustainCom)(BDCloud-SocialCom-SustainCom), 2016, pp. 560–566. IEEE (2016)
Author information
Authors and Affiliations
Corresponding author
Editor information
Editors and Affiliations
Rights and permissions
Copyright information
© 2018 Springer International Publishing AG
About this paper
Cite this paper
Wang, C., Ding, J., Guo, T., Cui, B. (2018). A Malware Detection Method Based on Sandbox, Binary Instrumentation and Multidimensional Feature Extraction. In: Barolli, L., Xhafa, F., Conesa, J. (eds) Advances on Broad-Band Wireless Computing, Communication and Applications. BWCCA 2017. Lecture Notes on Data Engineering and Communications Technologies, vol 12. Springer, Cham. https://doi.org/10.1007/978-3-319-69811-3_39
Download citation
DOI: https://doi.org/10.1007/978-3-319-69811-3_39
Published:
Publisher Name: Springer, Cham
Print ISBN: 978-3-319-69810-6
Online ISBN: 978-3-319-69811-3
eBook Packages: EngineeringEngineering (R0)