Abstract
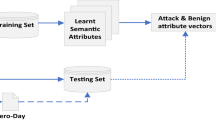
One of the main problems in Network Intrusion Detection comes from constant rise of new attacks, so that not enough labeled examples are available for the new classes of attacks. Traditional Machine Learning approaches hardly address such problem. This can be overcome with Zero-Shot Learning, a new approach in the field of Computer Vision, which can be described in two stages: the Attribute Learning and the Inference Stage. The goal of this paper is to propose a new Inference Stage algorithm for Network Intrusion Detection. In order to attain this objective, we firstly put forward an experimental setup for the evaluation of the Zero-Shot Learning in Network Intrusion Detection related tasks. Secondly, a decision tree based algorithm is applied to extract rules for generating the attributes in the AL stage. Finally, using a representation of a Zero-Shot Class as a point in the Grassmann manifold, an explicit formula for the shortest distance between points in that manifold can be used to compute the geodesic distance between the Zero-Shot Classes which represent the new attacks and the Known Classes corresponding to the attack categories. The experimental results in the datasets KDD Cup 99 and NSL-KDD show that our approach with Zero-Shot Learning successfully addresses the Network Intrusion Detection problem.
Access this chapter
Tax calculation will be finalised at checkout
Purchases are for personal use only
Similar content being viewed by others
Notes
- 1.
Available at http://www.kdd.org/kddcup/index.php.
- 2.
- 3.
Due to space limitations we present only the NSL-KDD setup for Zero-Shot Learning.
- 4.
Note that by adding the number of KC (15, 2nd column) and the number ZSC (8, 4th column) we obtain the total number of 23 classes for this dataset.
References
Akata, Z., Perronnin, F., Harchaoui, Z., Schmid, C.: Label-embedding for attribute-based classification. In: IEEE Conference on Computer Vision and Pattern Recognition, pp. 819–826. IEEE Computer Society, Washington, DC (2013)
Lampert, C.H., Nickisch, H., Harmeling, S.: Attribute-based classification for zero-shot visual object categorization. IEEE Trans. Pattern Anal. Mach. Intell. 36(3), 453–465 (2014)
Romera-Paredes, B., Torr, P.: An embarrassingly simple approach to zero-shot learning. In: Bach, F., David, B. (eds.) 32nd International Conference on Machine Learning, pp. 2152–2161. JMLR.org (2015)
Pérez, J.L.R., Ribeiro, B.: Attribute learning for network intrusion detection. In: Angelov, P., Manolopoulos, Y., Iliadis, L., Roy, A., Vellasco, M. (eds.) INNS 2016. AISC, vol. 529, pp. 39–49. Springer, Cham (2017). doi:10.1007/978-3-319-47898-2_5
Lampert, C.H., Nickisch, H., Harmeling, S.: Learning to detect unseen object classes by between-class attribute transfer. In: IEEE Conference on Computer Vision and Pattern Recognition, pp. 951–958. Curran Associates, Inc. (2009)
Socher, R., Ganjoo, M., Manning, C.D., Ng, A.: Zero-shot learning through cross-modal transfer. In: Advances in Neural Information Processing Systems, vol. 26, pp. 935–943 (2013)
Yang, Y., Hospedales, T.: Zero-shot domain adaptation via kernel regression on the Grassmannian. In: 1st International Workshop on Differential Geometry in Computer Vision for Analysis of Shapes, Images and Trajectories (2015)
Hamm, J., Lee, D.D.: Grassmann discriminant analysis: a unifying view on subspace-based learning. In: 25th International Conference on Machine Learning, pp. 376–383. ACM (2008)
Batzies, E., Hüper, K., Machado, L., Silva-Leite, F.: Geometric mean and geodesic regression on Grassmannians. Linear Algebra Appl. 466, 83–101 (2015)
Gonzalez, H., Morell, C., Ferri, F.J.: Improving nearest neighbor based multi-target prediction through metric learning. In: Beltrán-Castaõón, C., Nyström, I., Famili, F. (eds.) CIARP 2016. LNCS, vol. 10125, pp. 368–376. Springer, Cham (2017). doi:10.1007/978-3-319-52277-7_45
Acknowledgments
Erasmus Mundus Action 2 is acknowledged for partial funding of the first author.
SASSI Project (33/SI/2015&DT) is gratefully acknowledged for partial financial support.
Author information
Authors and Affiliations
Corresponding author
Editor information
Editors and Affiliations
Rights and permissions
Copyright information
© 2017 Springer International Publishing AG
About this paper
Cite this paper
Rivero, J., Ribeiro, B., Chen, N., Leite, F.S. (2017). A Grassmannian Approach to Zero-Shot Learning for Network Intrusion Detection. In: Liu, D., Xie, S., Li, Y., Zhao, D., El-Alfy, ES. (eds) Neural Information Processing. ICONIP 2017. Lecture Notes in Computer Science(), vol 10634. Springer, Cham. https://doi.org/10.1007/978-3-319-70087-8_59
Download citation
DOI: https://doi.org/10.1007/978-3-319-70087-8_59
Published:
Publisher Name: Springer, Cham
Print ISBN: 978-3-319-70086-1
Online ISBN: 978-3-319-70087-8
eBook Packages: Computer ScienceComputer Science (R0)