Abstract
Although the transactions on the Bitcoin blockchain have the main purpose of recording currency transfers, they can also carry a few bytes of metadata. A sequence of transaction metadata forms a subchain of the Bitcoin blockchain, and it can be used to store a tamper-proof execution trace of a smart contract. Except for the trivial case of contracts which admit any trace, in general there may exist inconsistent subchains which represent incorrect contract executions. A crucial issue is how to make it difficult, for an adversary, to subvert the execution of a contract by making its subchain inconsistent. Existing approaches either postulate that subchains are always consistent, or give weak guarantees about their security (for instance, they are susceptible to Sybil attacks). We propose a consensus protocol, based on Proof-of-Stake, that incentivizes nodes to consistently extend the subchain. We empirically evaluate the security of our protocol, and we show how to exploit it as the basis for smart contracts on Bitcoin.
Access this chapter
Tax calculation will be finalised at checkout
Purchases are for personal use only
Notes
- 1.
This is important, because non-standard transactions are discarded by nodes running the official Bitcoin client.
- 2.
Source: crypto-currency market capitalizations http://coinmarketcap.com.
- 3.
in-script and out-script are respectively referred as scriptPubKey and scriptSig in the Bitcoin documentation.
- 4.
Note that a similar hypothesis, but related to computational power rather than stake, holds in Bitcoin, where honest miners are supposed to control more computational power than dishonest ones.
- 5.
We assume that all meta-nodes agree on the Bitcoin blockchain; since \(\eta \) is a projection of the blockchain, they also agree on \(\eta \).
- 6.
Under this assumption, meta-nodes can ensure that the arbiter is honest.
- 7.
The
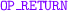 instruction allows to save 80 bytes metadata in a transaction; an out-script containing
instruction allows to save 80 bytes metadata in a transaction; an out-script containing  always evaluates to false, hence it is unspendable.
always evaluates to false, hence it is unspendable. - 8.
Assuming a single adversary is not less general than having many non-colluding meta-nodes which carry on individual attacks. Indeed, in this setting meta-nodes do not join their funds to increase the stake ratio \(\mu \).
- 9.
Note that saying the update queue is not always saturated is equivalent to model an adversary with a stronger \(\mu \): this because honest meta-nodes cannot spend all their stake in a single protocol stage, i.e. reducing their actual power. Thus, studying this particular case will not give any additional contribution to the analysis.
References
Making sense of blockchain smart contracts. http://www.coindesk.com/making-sense-smart-contracts/. Accessed 14 Jan 2017
opreturn.org. http://opreturn.org/. Accessed 15 Dec 2016
Andrychowicz, M., Dziembowski, S., Malinowski, D., Mazurek, Ł.: Fair two-party computations via Bitcoin deposits. In: Böhme, R., Brenner, M., Moore, T., Smith, M. (eds.) FC 2014. LNCS, vol. 8438, pp. 105–121. Springer, Heidelberg (2014). https://doi.org/10.1007/978-3-662-44774-1_8
Babaioff, M., Dobzinski, S., Oren, S., Zohar, A.: On Bitcoin and red balloons. In: ACM Conference on Electronic Commerce (EC), pp. 56–73 (2012)
Banasik, W., Dziembowski, S., Malinowski, D.: Efficient zero-knowledge contingent payments in cryptocurrencies without scripts. In: Askoxylakis, I., Ioannidis, S., Katsikas, S., Meadows, C. (eds.) ESORICS 2016. LNCS, vol. 9879, pp. 261–280. Springer, Cham (2016). https://doi.org/10.1007/978-3-319-45741-3_14
Bartoletti, M., Pompianu, L.: An analysis of Bitcoin OP_RETURN metadata. In: Financial Cryptography Workshops (2017). Also available as CoRR abs/1702.01024
Bartoletti, M., Zunino, R.: Constant-deposit multiparty lotteries on Bitcoin. In: Financial Cryptography Workshops (2017). Also available as IACR Cryptology ePrint Archive 955/2016
Bentov, I., Gabizon, A., Mizrahi, A.: Cryptocurrencies without proof of work. In: Clark, J., Meiklejohn, S., Ryan, P.Y.A., Wallach, D., Brenner, M., Rohloff, K. (eds.) FC 2016. LNCS, vol. 9604, pp. 142–157. Springer, Heidelberg (2016). https://doi.org/10.1007/978-3-662-53357-4_10
Bentov, I., Kumaresan, R.: How to use Bitcoin to design fair protocols. In: Garay, J.A., Gennaro, R. (eds.) CRYPTO 2014. LNCS, vol. 8617, pp. 421–439. Springer, Heidelberg (2014). https://doi.org/10.1007/978-3-662-44381-1_24
Blockstore: key-value store for name registration and data storage on the Bitcoin blockchain (2014). https://github.com/blockstack/blockstore
Buterin, V.: Ethereum: a next generation smart contract and decentralized application platform (2013). https://github.com/ethereum/wiki/wiki/White-Paper
Cai, M., Chervenak, A., Frank, M.: A peer-to-peer replica location service based on a distributed hash table. In: ACM/IEEE Conference on High Performance Networking and Computing, p. 56. IEEE Computer Society (2004)
Crary, K., Sullivan, M.J.: Peer-to-peer affine commitment using Bitcoin. In: ACM PLDI, pp. 479–488 (2015)
Dermody, R., Krellenstein, A., Slama, O., Wagner, E.: CounterParty: protocol specification (2014). http://counterparty.io/docs/protocol_specification/
Dwork, C., Naor, M.: Pricing via processing or combatting junk mail. In: Brickell, E.F. (ed.) CRYPTO 1992. LNCS, vol. 740, pp. 139–147. Springer, Heidelberg (1993). https://doi.org/10.1007/3-540-48071-4_10
Eyal, I., Sirer, E.G.: Majority is not enough: Bitcoin mining is vulnerable. In: Christin, N., Safavi-Naini, R. (eds.) FC 2014. LNCS, vol. 8437, pp. 436–454. Springer, Heidelberg (2014). https://doi.org/10.1007/978-3-662-45472-5_28
Garay, J., Kiayias, A., Leonardos, N.: The Bitcoin backbone protocol: analysis and applications. In: Oswald, E., Fischlin, M. (eds.) EUROCRYPT 2015. LNCS, vol. 9057, pp. 281–310. Springer, Heidelberg (2015). https://doi.org/10.1007/978-3-662-46803-6_10
Göbel, J., Joschko, P., Koors, A., Page, B.: The discrete event simulation framework DESMO-J: review, comparison to other frameworks and latest development. In: European Conference on Modelling and Simulation (ECMS), pp. 100–109. European Council for Modeling and Simulation (2013)
Hern, A.: A history of Bitcoin hacks. March 2014. http://www.theguardian.com/technology/2014/mar/18/history-of-bitcoin-hacks-alternative-currency
Iyer, S., Rowstron, A., Druschel, P.: Squirrel: a decentralized peer-to-peer web cache. In: PODC, pp. 213–222. ACM (2002)
Kiayias, A., Konstantinou, I., Russell, A., David, B., Oliynykov, R.: Ouroboros: a provably secure proof-of-stake blockchain protocol (2016). IACR Cryptology ePrint Archive, 2016:889
Kiayias, A., Zhou, H.-S., Zikas, V.: Fair and robust multi-party computation using a global transaction ledger. In: Fischlin, M., Coron, J.-S. (eds.) EUROCRYPT 2016. LNCS, vol. 9666, pp. 705–734. Springer, Heidelberg (2016). https://doi.org/10.1007/978-3-662-49896-5_25
Kumaresan, R., Bentov, I.: How to use Bitcoin to incentivize correct computations. In: ACM CCS, pp. 30–41 (2014)
Kumaresan, R., Moran, T., Bentov, I.: How to use Bitcoin to play decentralized poker. In: ACM CCS, pp. 195–206 (2015)
Maymounkov, P., Mazières, D.: Kademlia: a peer-to-peer information system based on the XOR metric. In: Druschel, P., Kaashoek, F., Rowstron, A. (eds.) IPTPS 2002. LNCS, vol. 2429, pp. 53–65. Springer, Heidelberg (2002). https://doi.org/10.1007/3-540-45748-8_5
Nakamoto, S.: Bitcoin: a peer-to-peer electronic cash system (2018). https://bitcoin.org/bitcoin.pdf
Rosenfeld, M.: Analysis of hashrate-based double spending (2014). CoRR, abs/1402.2009
Ruffing, T., Kate, A., Schröder, D.: Liar, liar, coins on fire!: penalizing equivocation by loss of Bitcoins. In: ACM CCS, pp. 219–230 (2015)
Szabo, N.: Formalizing and securing relationships on public networks. First Monday, 2(9) (1997)
Tomescu, A., Devadas, S.: Catena: efficient non-equivocation via Bitcoin. In: IEEE Symposium on Security and Privacy (2017)
Acknowledgments
This work is partially supported by Aut. Reg. of Sardinia grant P.I.A. 2013 “NOMAD”. Alessandro Sebastian Podda gratefully acknowledges Sardinia Regional Government for the financial support of her PhD scholarship (P.O.R. Sardegna F.S.E. Operational Programme of the Autonomous Region of Sardinia, European Social Fund 2007-2013 - Axis IV Human Resources, Objective l.3, Line of Activity l.3.1).
Author information
Authors and Affiliations
Corresponding author
Editor information
Editors and Affiliations
Rights and permissions
Copyright information
© 2017 International Financial Cryptography Association
About this paper
Cite this paper
Bartoletti, M., Lande, S., Podda, A.S. (2017). A Proof-of-Stake Protocol for Consensus on Bitcoin Subchains. In: Brenner, M., et al. Financial Cryptography and Data Security. FC 2017. Lecture Notes in Computer Science(), vol 10323. Springer, Cham. https://doi.org/10.1007/978-3-319-70278-0_36
Download citation
DOI: https://doi.org/10.1007/978-3-319-70278-0_36
Published:
Publisher Name: Springer, Cham
Print ISBN: 978-3-319-70277-3
Online ISBN: 978-3-319-70278-0
eBook Packages: Computer ScienceComputer Science (R0)


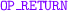 instruction allows to save 80 bytes metadata in a transaction; an
instruction allows to save 80 bytes metadata in a transaction; an  always evaluates to false, hence it is unspendable.
always evaluates to false, hence it is unspendable.