Abstract
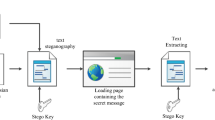
This research work proposes a steganography on social media communications. Nowadays, people frequently use messenger or social network such as Skype, Line, Facebook, Whatsapp and Twitter, etc. to communicate with other people and these platforms become popular to be used to exchange secrets or preserve personal information. Personal information like accounts and passwords might not be seen and embedded to cover objects when two clients communicate to each other. Those objects shall be pictures, music, or text messages. The proposed scheme will be deployed on the cover text. A strategy is designed to increase the capacity of hidden data and try to make any simple piece of text to be the cover text; such as letters, article of news or the common messages. The new approach – Extended Line will be adopted, and then together with White Space between to increase the capacity of a text. The simulation results disclose that the algorithm not only increases the capacity, but also increases the efficiency of decoding. Moreover, it still works on any kind of cover text.
Access this chapter
Tax calculation will be finalised at checkout
Purchases are for personal use only
Similar content being viewed by others
References
Katzenbeisser, S., Petitcolas, F.A.P.: Information Hiding Techniques for Steganography and Digital Watermarking. Artech House, Norwood (2000)
Petitcolas, F.A.P., Anderson, R.J., Kuhn, M.G.: Information hiding: a survey. Proc. IEEE (Spec. Issue) 87, 1062–1078 (1999)
Li, B., He, J., Huang, J., Shi, Y.Q.: A survey on image steganography and steganalysis. J. Inf. Hiding Multimedia Signal Process. 2, 142–172 (2011)
Bender, W., Morimoto, N., Lu, A.: Techniques for data hiding. IBM Syst. J. 35, 313–336 (1996)
Shiu, H.J., Tang, S.Y., Huang, C.H., Lee, R.C.T., Lei, C.L.: A reversible acoustic data hiding method based on analog modulation. Inf. Sci. 273, 233–246 (2014)
Shiu, H.J., Lin, B.S., Cheng, C.W., Huang, C.H., Lei, C.L.: High-capacity data-hiding scheme on synthesized pitches using amplitude enhancement-a new vision of non-blind audio steganography. Symmetry 9(6), 92–111 (2017)
Shiu, H.J., Ng, K.L., Fang, J.F., Lee, R.C.T., Huang, C.H.: Data hiding methods based upon DNA sequences. Inf. Sci. 180, 2196–2208 (2010)
Rafat, K.F.: Enhanced text steganography in SMS. In: 2nd International Conference on Computer, Control and Communication (2009)
Shirali-Shahreza, M., Shirali-Shahreza, M.H.: A new approach to Persian/Arabic text steganography. In: 5th IEEE/ACIS International Conference on Computer and Information Science (2006)
Shirali-Shahreza, M., Shirali-Shahreza, M.H.: Text steganography in SMS. In: 2007 International Conference on Convergence Information Technology (2007)
Shirali-Shahreza, M., Shirali-Shahreza, M.H.: A new synonym text steganography. In: International Conference on Intelligent Information Hiding and Multimedia Signal Processing (2008)
Shirali-Shahreza, M., Shirali-Shahreza, M.H.: Text steganography in chat. In: 3rd IEEE/IFIP International Conference in Central Asia on Internet (2007)
Shirali-Shahreza, M.: Test steganography by changing words spelling. In: 10th International Conference on Advanced Communication Technology (2008)
Roy, S., Manasmita, M.: A novel approach to format based text steganography. In: 2011 International Conference on Communication, Computing and Security (2011)
Author information
Authors and Affiliations
Corresponding author
Editor information
Editors and Affiliations
Rights and permissions
Copyright information
© 2018 Springer International Publishing AG, part of Springer Nature
About this paper
Cite this paper
Shiu, HJ., Lin, BS., Lin, BS., Huang, PY., Huang, CH., Lei, CL. (2018). Data Hiding on Social Media Communications Using Text Steganography. In: Cuppens, N., Cuppens, F., Lanet, JL., Legay, A., Garcia-Alfaro, J. (eds) Risks and Security of Internet and Systems. CRiSIS 2017. Lecture Notes in Computer Science(), vol 10694. Springer, Cham. https://doi.org/10.1007/978-3-319-76687-4_15
Download citation
DOI: https://doi.org/10.1007/978-3-319-76687-4_15
Published:
Publisher Name: Springer, Cham
Print ISBN: 978-3-319-76686-7
Online ISBN: 978-3-319-76687-4
eBook Packages: Computer ScienceComputer Science (R0)