Abstract
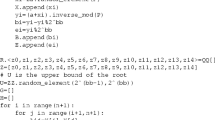
In this paper, we propose an improved algorithm to solve the univariate modular equations with mutually co-prime moduli problem. This problem was first proposed in Håstad’s original RSA broadcast attack. At PKC 2008, May and Ritzenhofen improved Håstad’s result by using a slightly different transformation from polynomial systems to a single polynomial. In this work, we propose a new construction method to combine all the k equations into a single equation \(f(x)\equiv 0 \mod \prod _{i=1}^{k}N_i\). Our improved algorithm possesses two advantages compared with the two previous ones. Compared with Håstad’s approach, our algorithm only needs fewer number of equations which suffice for a recovery of all common roots. Compared with May and Ritzenhofen’s, our method obtains the single equation f(x) with a smaller degree. The benefit is that this new algorithm will find the small solution \(x_0\) more efficiently when we invoke Coppersmith’s algorithm.
Access this chapter
Tax calculation will be finalised at checkout
Purchases are for personal use only
Similar content being viewed by others
References
Bi, J., Coron, J.-S., Faugère, J.-C., Nguyen, P.Q., Renault, G., Zeitoun, R.: Rounding and chaining LLL: finding faster small roots of univariate polynomial congruences. In: Krawczyk, H. (ed.) PKC 2014. LNCS, vol. 8383, pp. 185–202. Springer, Heidelberg (2014). https://doi.org/10.1007/978-3-642-54631-0_11
Bach, E., Shallit, J.: Algorithmic Number Theory: Efficient Algorithms - Volume 1. The MIT Press, Cambridge (1996)
Boneh, D.: Twenty years of attacks on the RSA cryptosystem. Not. AMS 46, 203–213 (1999)
Boneh, D., Venkatesan, R.: Breaking RSA may not be equivalent to factoring. In: Nyberg, K. (ed.) EUROCRYPT 1998. LNCS, vol. 1403, pp. 59–71. Springer, Heidelberg (1998). https://doi.org/10.1007/BFb0054117
Brown, D.: Breaking RSA may be as difficult as factoring. Cryptology ePrint Archive Report 2005/380 (2005)
Coppersmith, D.: Finding small solutions to small degree polynomials. In: Silverman, J.H. (ed.) CaLC 2001. LNCS, vol. 2146, pp. 20–31. Springer, Heidelberg (2001). https://doi.org/10.1007/3-540-44670-2_3
Coppersmith, D.: Small solutions to polynomial equations and low exponent vulnerabilities. J. Cryptol. 10(4), 223–260 (1997)
Coppersmith, D., Franklin, M., Patarin, J., Reiter, M.: Low-exponent rsa with related messages. In: Maurer, U. (ed.) EUROCRYPT 1996. LNCS, vol. 1070, pp. 1–9. Springer, Heidelberg (1996). https://doi.org/10.1007/3-540-68339-9_1
Hastad, J.: N using RSA with low exponent in a public key network. In: Williams, H.C. (ed.) CRYPTO 1985. LNCS, vol. 218, pp. 403–408. Springer, Heidelberg (1986). https://doi.org/10.1007/3-540-39799-X_29
Håstad, J.: Solving simultaneous modular equations of low degree. SIAM J. Comput. 17(2), 336–341 (1988)
Leander, G., Rupp, A.: On the equivalence of RSA and factoring regarding generic ring algorithms. In: Lai, X., Chen, K. (eds.) ASIACRYPT 2006. LNCS, vol. 4284, pp. 241–251. Springer, Heidelberg (2006). https://doi.org/10.1007/11935230_16
Lenstra, A.K., Lenstra, H.W., Lovsz, L.: Factoring polynomials with rational coefficients. Math. Ann. 261, 513–534 (1982)
May, A.: Using LLL-reduction for solving RSA and factorization problems: a survey. In: LLL+25 Conference in Honour of the 25th Birthday of the LLL Algorithm (2007)
May, A., Ritzenhofen, M.: Solving systems of modular equations in one variable: how many RSA-encrypted messages does eve need to know? In: Cramer, R. (ed.) PKC 2008. LNCS, vol. 4939, pp. 37–46. Springer, Heidelberg (2008). https://doi.org/10.1007/978-3-540-78440-1_3
Nguên, P.Q., Stehlé, D.: Floating-point LLL revisited. In: Cramer, R. (ed.) EUROCRYPT 2005. LNCS, vol. 3494, pp. 215–233. Springer, Heidelberg (2005). https://doi.org/10.1007/11426639_13
Rivest, R., Shamir, A., Adleman, L.: A method for obtaining digital signatures and public-key cryptosystems. Commun. ACM 21(2), 120–126 (1978)
Shoup, V.: A Computational Introduction to Number Theory and Algebra. Cambridge University Press, Cambridge (2005)
Simmons, G.: A weak privacy protocol using the RSA crypto algorithm. Cryptologia 7(2), 180–182 (1983)
Acknowledgments
This paper is partially supported by: NSF of China under grants No. 61502269 & 61672019, 973 Program grant 2013CB834205 and the national key research and development program of China grant No. 2017YFA0303903.
Author information
Authors and Affiliations
Corresponding author
Editor information
Editors and Affiliations
Rights and permissions
Copyright information
© 2018 Springer International Publishing AG, part of Springer Nature
About this paper
Cite this paper
Bi, J., Wang, M., Wei, W. (2018). An Improved Algorithm to Solve the Systems of Univariate Modular Equations. In: Kang, B., Kim, T. (eds) Information Security Applications. WISA 2017. Lecture Notes in Computer Science(), vol 10763. Springer, Cham. https://doi.org/10.1007/978-3-319-93563-8_5
Download citation
DOI: https://doi.org/10.1007/978-3-319-93563-8_5
Published:
Publisher Name: Springer, Cham
Print ISBN: 978-3-319-93562-1
Online ISBN: 978-3-319-93563-8
eBook Packages: Computer ScienceComputer Science (R0)