Abstract
Spoofing attacks provided by fake individuals are considered as a major interest on biometric systems. To implement a robust face biometric system, deploying a reliable anti-spoofing scheme is needed. The concentration of this study to organize the anti-spoofing technique is on overlapped face textures together with image quality assessment. Our proposed fake detection scheme applies double anti-spoofing solution to distinguish live and fake identities. Firstly, image quality assessment method is used to differentiate fake and real samples by comparing their quality. The fake detection method using overlapped histograms of LBP texture descriptor is then applied for those samples recognized as real to increase the robustness of the biometric system against unreliable quality of images. Proposed spoof detection method presents an effective strategy for detecting fake face samples for video and print attacks. Demonstration of results on public spoof databases clarifies the robustness of the proposed solution for face fake detection.
You have full access to this open access chapter, Download conference paper PDF
Similar content being viewed by others
Keywords
1 Introduction
The increasing emphasis of biometric systems security and their robustness evaluation has led to introduce new protection techniques and research over the past years [1,2,3,4,5,6]. Generally, two types of attacks on biometric systems can be considered namely ‘indirect attacks’ and ‘direct attacks’ [7]. Indirect attacks need knowledge of system or internal parameters access while direct attacks or spoofing concentrate on submitting a counterfeited biometric to the sensor [7]. In general, spoofing attacks, particularly print and replay attacks for face biometrics, represent a serious vulnerability for biometric system evaluation. In this respect, biometric community concentration for detection of spoofing attacks is on analyzing the vulnerability of biometric system to this kind of attack as a big challenge [5,6,7,8,9,10,11,12].
Spoof detection for biometric system recognition is categorized as texture, motion and liveness detection [13]. Texture analysis focuses on detecting texture patterns of images, motion analysis represents the motion features of images to get over texture pattern dependencies, and liveness analysis considers the vitality signs of biometrics by evaluating spontaneous movements of images which is not able to detect. In fact, considering a global solution to all spoofing attacks is not possible due to the nature of attacks, biometric traits and spoof detection approaches. On the other hand, image distortions during acquisition, capturing, processing, transmission and reproduction causes degradation of image qualities. Therefore, development of Image quality assessment methods (IQA) for improving the quality of digital images specifically for print and video attacks has been motivated in the recent years [2, 5, 9, 16,17,18]. Indeed, the IQA methods differentiate fake and real samples by detecting the quality differences between real and fake samples [5].
In this study, we attempt to propose a robust face anti-spoofing technique against print and video attacks according to IQA and texture-based methods. The texture-based techniques typically concentrate on texture patterns of print failures and/or overall image blurs to detect attacks while IQA techniques aim to compare the real and fake image quality. Therefore, the use of these two techniques to detect both print and video attacks can be successful in both identification and verification systems. In this study, we consider full-reference (FR) assessment to measure the quality of face test images against print, video and combination of print and video attacks. Moreover, we apply Local Binary Patterns (LBP), Histogram Oriented Gradient (HOG) and overlapped histogram of LBP (OVLBP) as texture-based strategy to analyze print, video and print + video attacks. Therefore, we can summarize the contribution of the proposed method as: introducing a robust face anti-spoofing scheme for both print and video attacks, the proposed scheme can be implemented in any person identification and verification systems using face images to detect print, video and combination of print and video attacks, the use of overlapped histograms for face spoof detection is introduced as a robust protection strategy based on biometric texture patterns.
The organization of reminder of paper is as follow: Sect. 2 summarizes the research works of spoofing attacks and protection techniques. Section 3 describes IQA methods while the concentration of Sect. 4 is on texture-based approaches applied in this study. The description of proposed spoof detection strategy is in Sect. 5. Section 6 presents the databases and experimental result implemented in this study. Finally, Sect. 7 draws the conclusion of this study.
2 Related Works
Recently, several fake detection techniques in literature on face biometrics are discussed [5, 10, 13,14,15, 19,20,21]. In [5], a novel software-based spoof detection is proposed for liveness detection using image quality assessment. The authors proposed to apply 25 different image quality features of an image to recognize fake samples. Face spoofing detection method in face videos using motion magnification is proposed in [10]. Their proposed framework improved LBP performance to detect fake samples. They also applied successfully a motion estimated based technique using Histogram of Oriented Optical Flow (HOOF) descriptor on the Print-Attack and Replay-Attack databases. The authors of [13] compared different algorithms based on motion analysis, texture analysis and liveness detection to detect 2D facial print based spoof attacks. They found the effectiveness of applying multiple techniques for detection of print based spoof attacks. The evaluation of trajectory of several face parts using the optical flow of lines has been proposed successfully for liveness detection in separating live face sequences in [14]. They applied a model-based local Gabor decomposition and Support Vector Machine (SVM) experts for face part detection in their liveness detection framework. In [15], a holistic liveness detection paradigm has been introduced as an anti-spoofing technique for 2D face biometric. They suggested combining anti-spoofing measures in interactive scenarios to have reliable liveness detection. The researchers in [19] applied multi-scale LBP to convert the micro-textures into an enhanced feature histogram for face fake detection using texture analysis. They then classified fake and real samples using SVM in front of camera. The structures and dynamics of facial micro-textures for real faces have been used based on LBP in [20] as anti-spoofing method on Replay-Attack and CASIA Face Anti-Spoofing databases. In [21], the authors proposed image distortion analysis (IDA) to detect spoof attacks. They extracted specular reflection, blurriness, chromic moment, and color diversity feature of 2D face images to construct IDA features.
3 Image Quality Assessment for Fake Face Detection
Image quality assessment (IQA) expects “quality-difference” of fake and real samples in an attack attempt [5]. The quality difference commonly includes degree of sharpness, color and luminance levels, local artifacts, amount of information in real and fake images, structural distortion or natural appearance [5]. Generally, IQA contains a wide range of techniques for measuring the quality of images. In this study, we attempt to apply well known full-reference (FR) measures to assess image quality using pixel difference measurements by computing the distortion between fake and real images. This measure [5] involves peak signal-to-noise ratio (PSNR), mean-squared error (MSE), maximum difference (MD), normalized absolute error (NAE) and average difference (AD), structural similarity measures such as similarity index measure (SSIM) and correlation-based measures such as normalized cross-correlation (NXC). Among aforementioned IQA metrics the best measurement against video attack and print attack is then selected in this study experimentally. Therefore, any fake/real test sample is compared with fake and real images stored in a training set to decide on the output as fake or real.
4 Texture-Based Approaches for Fake Face Detection
The computation of textural differences between real and fake image samples is performed using LBP [22], HOG [23] and OVLBP [24] texture descriptors in this study. LBP is a powerful gray-scale texture descriptor for face analysis that divides the image into several blocks in order to extract histogram of local features. The local histograms are then concatenated to provide a single global feature vector [22]. On the other hand, HOG is another texture descriptor approach that divides the image into several blocks and then counts occurrences of gradient orientations of local blocks. Finally the calculated local histograms are concatenated into a global feature vector [23]. The use of LBP and HOG as powerful texture descriptors in different face spoofing datasets demonstrated good performance to detect attacks especially for print and video attacks [8, 10, 19, 20]. This can be evidence of capability of histograms in anti-spoofing frameworks for print and video attacks. The idea of applying overlapped LBP histograms [24] is then suggested in this study to achieve more representative histograms and explore its effect on print, video and combination of both attacks. In order to detect print and video attacks OVLBP divides the image using overlapping of blocks to obtain more sub-windows over the image which involves micro-textons of more local primitive textures regarding to spots, flat areas, edges, edge ends and curves [24]. These small windows may involve more specific and exact texture information due to fusion of more descriptive histograms of overlapped regions which are able to detect print and video attacks in spoofed scenarios.
5 Proposed Face Spoof Detection
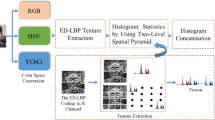
The proposed fake detection scheme protects face databases against video and print attacks as depicted in Fig. 1. In order to detect attacks, we first extract real and attack images of sample videos to construct spoof datasets. Mean squared error (MSE) as the best image quality assessment measurement is selected experimentally for detecting video and print attacks in this study. Decision on fake and real test samples is made using nearest neighbor (NN) classifiers by considering minimum error between test and reference samples. The recognized fake images by MSE image quality assessment are considered as attack using the anti-spoofing scheme.
On the other hand, IQA may not be successful for the realistic scenarios of print and video attacks when face images are spoofed using high quality artifacts which lead to produce images similar to real templates. To cope with this problem and increase the security of our face biometric systems, we consider OVLBP which achieves improvement against both print and video attacks. Prior to applying the overlapped histogram, all extracted face images are resized to 60 × 60 and undergo histogram equalization and mean variance normalization techniques. Therefore, we divide all fake and live images into 36 sub-regions of 10 × 10 window size for extracting the texture descriptors OVLBP. The proposed anti-spoofing framework considers 50% overlapping of each face block which leads to increasing the number of sub-windows and subsequently features for each face image. The scheme then selects optimized subset of textures by removing the redundant information using linear discriminant analysis (LDA) and decreasing the feature space dimension. The proposed scheme applies Manhattan distance measurement to compute the similarity scores between fake and real samples. Finally, NN classifier is used to make the decision as real or attack.
6 Experimental Results and Databases
The concentration of this section is on presenting different datasets of Print-Attack and Replay-Attack face databases and experimental results. Idiap Print-Attack [25] and Repla-Attack [26] databases contain short videos of real and attack access of 50 individuals for print and video attacks. In order to validate the robustness of proposed anti-spoofing framework, we consider 3 datasets. In total 10 real samples and 10 attack samples of 50 individuals are extracted from available video clips of Print-Attack database as dataset1. The same number of real and attack samples are extracted from the video clips of Replay-Attack database for 50 individuals as dataset2. Consequently, dataset3 combines print and video attacks using 10 real samples (5 print real samples + 5 video real samples) and 10 attack samples (5 print attack samples + 5 video attack samples) of aforementioned 50 individuals to test the robustness of proposed scheme in present of both attacks. The extracted real and attack samples are different with samples of dataset1 and dataset2. We assigned 15 individuals to set parameters and select best IQA for print and video attacks. The rest of individuals are then used to test the proposed anti-spoofing method by considering 5 reference and 5 testing samples. The partitioning of 50 individuals is repeated three times into aforementioned sets due to small size of database. We also applied 10 times partitioning of reference and test samples without overlapping to consider Holdout cross-validation of 30 different times. Therefore, the experimental results reported in this study are averaged on 30 runs and reported as means and standard deviations. Our anti-spoofing scheme considers Half Total Error Rate (HTER) which is half of sum of False Genuine Rate (FGR) and False Fake Rate (FFR) of spoof detection errors [5] to report the experimental results. In general, FGR calculates number of false samples that are classified as genuine incorrectly and FFR is number of real samples that are classified as fake [5].
The first set of experiments in this study involves the strength of seven general image quality assessment measures (IQA) [5] against print and video attacks as shown in Table 1. In fact, the aim of this experiment is to select the best IQA technique for print and video attacks to be used in the proposed face fake detection framework.
As reported in Table 1, PSNR, NAE and MSE techniques have obtained minimum HTER compared to other IQA measurements for both video and print attacks. However, the best performance of HTER belongs to MSE technique as 8.75% and 9.05% for print and video attacks respectively. Therefore, in implementation of the proposed spoof detection scheme MSE is considered as the best IQA measurement as depicted in Fig. 1.
In addition, in order to test the robustness of our proposed anti-spoofing pipeline we performed another set of experiments in Table 2. This table aims to compare the result of applying LBP and HOG as popular feature vectors against spoofing with OVLBP, MSE technique and proposed anti-spoofing framework. The experiments are conducted on dataset1, dataset2 and dataset3 respectively to analyze print attack, video attack and print + video attack respectively on face images.
The experiments done in Table 2 demonstrate the effectiveness of proposed anti-spoofing framework by reporting the minimum classification accuracy in terms of HTER for all kind of attacks. Analyzing the results shows the robustness of our proposed method, OVLBP with and without LDA against both kinds of attacks specifically on Replay-Attack database. The best result reported as HTER of 3.64% using proposed fake detection scheme for vide attacks. Comparison of results in Table 2 clarifies the strength of combining IQA-based protection methods with texture-based anti-spoofing methods to increase the security of face biometric systems while the type of attack (print or video) is not known for the system previously.
7 Conclusion
Proposing a novel anti-spoofing pipeline is presented in this study based on the overlapped face textures and image quality assessment. The proposed method first considers IQA techniques to recognize real and attack attempts in a face biometric system. Optimized overlapped texture-based anti-spoofing step is then applied in case of spoofing using high quality artifacts and therefore producing images similar to real templates. We compared our proposed method with state-of-the-art fake detection feature vectors such as LBP and HOG. The proposed scheme outperforms implemented fake detection methods in this study for print, video and combination of both attacks. Specifically, the use of OVLBP + LDA achieved the spoof detection improvement of 6.47% due to selection of optimized sub set of textures for video attacks over applying OVLBP texture descriptor without optimum feature selection. The idea of embedding overlapped LBP histograms into the proposed framework leads to achievement of more representative histograms for dealing both print and video attacks.
References
Prabhakar, S., Pankanti, S., Jain, A.K.: Biometric recognition: security and privacy concerns. IEEE Secur. Priv. 1(2), 33–42 (2003)
Galbally, J., Alonso-Fernandez, F., Fierrez, J., Ortega-Garcia, J.: A high performance fingerprint liveness detection method based on quality related features. Future Generat. Comput. Syst. 28(1), 311–321 (2012)
Galbally, J., Fierrez, J., Alonso-Fernandez, F., Martinez-Diaz, M.: Evaluation of direct attacks to fingerprint verification systems. J. Telecommun. Syst. 47(3–4), 243–254 (2011)
Nixon, K.A., Aimale, V., Rowe, R.K.: Spoof detection schemes. In: Jain, A.K., Flynn, P., Ross, A.A. (eds.) Handbook of Biometrics, pp. 403–423. Springer, New York (2008). https://doi.org/10.1007/978-0-387-71041-9_20
Galbally, J., Sébastien, M., Fierrez, J.: Image quality assessment for fake biometric detection: application to iris, fingerprint, and face recognition. IEEE Trans. Image Process. 23(2), 710–724 (2014)
Eskandari, M., Toygar, Ö.: Selection of optimized features and weights on face-iris fusion using distance images. Comput. Vis. Image Underst. 137, 63–75 (2015)
Biggio, B., Akhtar, Z., Fumera, G., Marcialis, G.L., Roli, F.: Security evaluation of biometric authentication systems under real spoofing attacks. IET Biom. 1(1), 11–24 (2012)
Gupta, P., et al.: On iris spoofing using print attack. In: 2014 22nd International Conference on Pattern Recognition (ICPR). IEEE (2014)
He, X., Lu, Y., Shi, P.: A fake iris detection method based on FFT and quality assessment. In: Chinese Conference on Pattern Recognition, CCPR 2008. IEEE (2008)
Samarth, B., et al.: Computationally efficient face spoofing detection with motion magnification. In: Proceedings of the IEEE Conference on Computer Vision and Pattern Recognition Workshops (2013)
Gomez-Barrero, M., Galbally, J., Fierrez, J.: Efficient software attack to multimodal biometric systems and its application to face and iris fusion. Pattern Recognit. Lett. 36, 243–253 (2014)
Akhtar, Z., Kale, S., Alfarid, N.: Spoof attacks on multimodal biometric systems. In: Proceedings of International Conference on Information and Network Technology (IPCSIT), vol. 4 (2011)
Chakka, M.M., et al.: Competition on counter measures to 2-d facial spoofing attacks. In: 2011 International Joint Conference on Biometrics (IJCB). IEEE (2011)
Kollreider, K., Fronthaler, H., Bigun, J.: Evaluating liveness by face images and the structure tensor. In: 2005 Fourth IEEE Workshop on Automatic Identification Advanced Technologies. IEEE (2005)
Kollreider, K., Fronthaler, H., Bigun, J.: Verifying liveness by multiple experts in face biometrics. In: 2008 IEEE Computer Society Conference on Computer Vision and Pattern Recognition Workshops, CVPRW 2008. IEEE (2008)
Bayram, S., et al.: Image manipulation detection. J. Electron. Imaging 15(4), 041102 (2006)
Stamm, M.C., RayLiu, K.J.: Forensic detection of image manipulation using statistical intrinsic fingerprints. IEEE Trans. Inf. Forensics Secur. 5(3), 492–506 (2010)
Galbally, J., et al.: Iris liveness detection based on quality related features. In: 2012 5th IAPR International Conference on Biometrics (ICB). IEEE (2012)
Määttä, J., Hadid, A., Pietikäinen, M.: Face spoofing detection from single images using micro-texture analysis. In: 2011 International Joint Conference on Biometrics (IJCB). IEEE (2011)
de Freitas Pereira, T., et al.: Face liveness detection using dynamic texture. EURASIP J. Image Video Process. 2014(1), 1–15 (2014)
Wen, D., Han, H., Jain, A.K.: Face spoof detection with image distortion analysis. IEEE Trans. Inf. Forensics Secur. 10(4), 746–761 (2015)
Ojala, T., Pietikäinen, M., Harwood, D.: A comparative study of texture measure with classification based on feature distributions. Pattern Recognit. 29, 51–59 (1996)
Dalal, N., Triggs, B.: Histograms of oriented gradients for human detection. In: 2005 IEEE Computer Society Conference on Computer Vision and Pattern Recognition, CVPR 2005, vol. 1. IEEE (2005)
Guo, Z., Zhang, D., Zhang, D.: A completed modeling of local binary pattern operator for texture classification. IEEE Trans. Image Process. 19(6), 1657–1663 (2010)
Print Attack face database. https://www.idiap.ch/dataset/printattack. Accessed Oct 2014
Replay Attack face database. https://www.idiap.ch/dataset/replayattack. Accessed Oct 2014
Author information
Authors and Affiliations
Corresponding author
Editor information
Editors and Affiliations
Rights and permissions
Copyright information
© 2018 Springer International Publishing AG, part of Springer Nature
About this paper
Cite this paper
Eskandari, M., Sharifi, O. (2018). Designing Efficient Spoof Detection Scheme for Face Biometric. In: Mansouri, A., El Moataz, A., Nouboud, F., Mammass, D. (eds) Image and Signal Processing. ICISP 2018. Lecture Notes in Computer Science(), vol 10884. Springer, Cham. https://doi.org/10.1007/978-3-319-94211-7_46
Download citation
DOI: https://doi.org/10.1007/978-3-319-94211-7_46
Published:
Publisher Name: Springer, Cham
Print ISBN: 978-3-319-94210-0
Online ISBN: 978-3-319-94211-7
eBook Packages: Computer ScienceComputer Science (R0)