Abstract
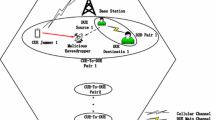
A heterogeneous network supporting D2D communications is a typical framework to cope with data sharing in a cyber physical system. In the network, there exists more interference than traditional cellular networks, which promotes interference cancellation (IC) technologies. Yet, how IC can improve security performance of D2D-enabled networks is still unknown. In addition, how to establish a secure physical transmission link for users in these networks is of great significance. In this paper, with IC or not, we first derive the expressions of the secrecy outage probability in D2D-enabled heterogeneous networks, respectively. Then, according to the transmission constraint and the security constraint, we present two cooperative jamming schemes based on devices in D2D networks for achieving secure uplink of cellular users. In these schemes, we formulate the above secure challenge as an optimization problem with or without fully IC and provide the corresponding optimal solutions to improve the secrecy performance of cellular uplink. Finally, numerical simulation demonstrates that the secure performance of cellular uplink is remarkably enhanced using our cooperative jamming schemes.
Access this chapter
Tax calculation will be finalised at checkout
Purchases are for personal use only
Similar content being viewed by others
References
Zheng, X., Cai, Z., Li, J., Gao, H.: A study on application-aware scheduling in wireless networks. IEEE Trans. Mob. Comput. 16(7), 1787–1801 (2017)
Cheng, S., Cai, Z., Li, J., Fang, X.: Drawing dominant dataset from big sensory data in wireless sensor networks. In: 2015 IEEE Conference on Computer Communications (INFOCOM), pp. 531–539, April 2015
Cai, Z., Chen, Z.-Z., Lin, G.: A 3.4713-approximation algorithm for the capacitated multicast tree routing problem. Theor. Comput. Sci. 410(52), 5415–5424 (2009)
Li, J., Cheng, S., Cai, Z., Yu, J., Wang, C., Li, Y.: Approximate holistic aggregation in wireless sensor networks. ACM Trans. Sen. Netw. 13(2), 11:1–11:24 (2017)
Cheng, S., Cai, Z., Li, J., Gao, H.: Extracting kernel dataset from big sensory data in wireless sensor networks. IEEE Trans. Knowl. Data Eng. 29(4), 813–827 (2017)
Huo, Y., Hu, C., Qi, X., Jing, T.: LoDPD: a location difference-based proximity detection protocol for fog computing. IEEE Internet Things J. 4(5), 1117–1124 (2017)
Asadi, A., Wang, Q., Mancuso, V.: A survey on device-to-device communication in cellular networks. IEEE Commun. Surv. Tutor. 16(4), 1801–1819 (2014)
Huo, Y., Tian, Y., Ma, L., Cheng, X., Jing, T.: Jamming strategies for physical layer security. IEEE Wirel. Commun. 25(1), 148–153 (2018)
He, Z., Cai, Z., Cheng, S., Wang, X.: Approximate aggregation for tracking quantiles and range countings in wireless sensor networks. Theor. Comput. Sci. 607(P3), 381–390 (2015)
Cai, Z., Lin, G., Xue, G.: Improved approximation algorithms for the capacitated multicast routing problem. In: Wang, L. (ed.) COCOON 2005. LNCS, vol. 3595, pp. 136–145. Springer, Heidelberg (2005). https://doi.org/10.1007/11533719_16
Cheng, S., Cai, Z., Li, J.: Curve query processing in wireless sensor networks. IEEE Trans. Veh. Technol. 64(11), 5198–5209 (2015)
Lee, N., Lin, X., Andrews, J.G., Heath, R.W.: Power control for D2D underlaid cellular networks: modeling, algorithms, and analysis. IEEE J. Sel. Areas Commun. 33(1), 1–13 (2015)
Huang, Y., Nasir, A.A., Durrani, S., Zhou, X.: Mode selection, resource allocation, and power control for D2D-enabled two-tier cellular network. IEEE Trans. Commun. 64(8), 3534–3547 (2016)
Memmi, A., Rezki, Z., Alouini, M.S.: Power control for D2D underlay cellular networks with channel uncertainty. IEEE Trans. Wirel. Commun. 16(2), 1330–1343 (2017)
Lin, X., Andrews, J.G., Ghosh, A.: Spectrum sharing for device-to-device communication in cellular networks. IEEE Trans. Wirel. Commun. 13(12), 6727–6740 (2014)
Ma, C., Li, Y., Yu, H., Gan, X., Wang, X., Ren, Y., Xu, J.J.: Cooperative spectrum sharing in D2D-enabled cellular networks. IEEE Trans. Commun. 64(10), 4394–4408 (2016)
Tanbourgi, R., Jakel, H., Jondral, F.K.: Cooperative interference cancellation using device-to-device communications. IEEE Commun. Mag. 52(6), 118–124 (2014)
Ni, Y., Jin, S., Xu, W., Wang, Y., Matthaiou, M., Zhu, H.: Beamforming and interference cancellation for D2D communication underlaying cellular networks. IEEE Trans. Commun. 64(2), 832–846 (2016)
Lv, S., Xing, C., Zhang, Z., Long, K.: Guard zone based interference management for D2D-aided underlaying cellular networks. IEEE Trans. Veh. Technol. 66(6), 5466–5471 (2017)
Haus, M., Waqas, M., Ding, A.Y., Li, Y., Tarkoma, S., Ott, J.: Security and privacy in device-to-device (D2D) communication: a review. IEEE Commun. Surv. Tutor. 19(2), 1054–1079 (2017)
Barki, A., Bouabdallah, A., Gharout, S., Traor, J.: M2M security: challenges and solutions. IEEE Commun. Surv. Tutor. 18(2), 1241–1254 (2016)
Huang, L., Fan, X., Huo, Y., Hu, C., Tian, Y., Qian, J.: A novel cooperative jamming scheme for wireless social networks without known CSI. IEEE Access 5, 26476–26486 (2017)
Zhang, R., Cheng, X., Yang, L.: Joint power and access control for physical layer security in D2D communications underlaying cellular networks. In: 2016 IEEE International Conference on Communications (ICC), pp. 1–6, May 2016
Wang, L., Wu, H., Liu, L., Song, M., Cheng, Y.: Secrecy-oriented partner selection based on social trust in device-to-device communications. In: 2015 IEEE International Conference on Communications (ICC), pp. 7275–7279, June 2015
Zhang, R., Cheng, X., Yang, L.: Cooperation via spectrum sharing for physical layer security in device-to-device communications underlaying cellular networks. IEEE Trans. Wirel. Commun. 15(8), 5651–5663 (2016)
Alavi, F., Yamchi, N.M., Javan, M.R., Cumanan, K.: Limited feedback scheme for device-to-device communications in 5G cellular networks with reliability and cellular secrecy outage constraints. IEEE Trans. Veh. Technol. 66(9), 8072–8085 (2017)
Ma, C., Wu, W., Cui, Y., Wang, X.: On the performance of interference cancelation in D2D-enabled cellular networks. Wirel. Commun. Mob. Comput. 16(16), 2619–2635 (2016)
Acknowledgments
This work was supported by the National Natural Science Foundation of China (Grant No. 61471028, 61572070, and 61702062), and the Fundamental Research Funds for the Central Universities (Grant No. 2017JBM004 and 2016JBZ003).
Author information
Authors and Affiliations
Corresponding author
Editor information
Editors and Affiliations
Appendices
Appendix A: Proof of Lemma 1
To proof Lemma 1, we first discuss \(F_{\gamma _c}(T)\triangleq 1-\mathrm {Pr}^{\mathrm {(N)}}(\gamma _c>T)\) based on the CDF definition. Here, \(\mathrm {Pr}^{\mathrm {(N)}}(\gamma _c>T)\) represents the coverage probability of the cellular link without IC capability, which is
where \(\mathcal {L}^{\mathrm {(N)}}(s)=E_{\varPhi _{c,d}}\left[ e^{-s\sum _{k\in \varPhi _{c,d}}p_d\left| h_{kM}\right| ^2r_{kM}^{-\alpha }} \right] \) denotes the Laplace transform of s for the scenario without IC capability. Specifically,
where \(\mathrm {(a)}\) follows the PDF of PPP, and \(\mathrm {(b)}\) holds because of the definition of a surface integral. Accordingly, (12) can be rewritten as follows.
Next, we can derive the PDF of the most detrimental Eve, \(g(\cdot )\), based on the partial differential of the corresponding CDF, \(G(\cdot )\). Assuming M as the best SINR of eavesdroppers, \(G(M)\triangleq \mathrm {Pr}(\max \gamma _{e}<M)\) can be calculated as follows.
where \(\mathrm {(c)}\) holds by substituting \(\mathcal {L}^{\mathrm {(N)}}(\cdot )\).
As a result, the secrecy outage probability of CU\(_c\) can be expressed as
where \(A=\pi (\frac{p_d}{p_c})^{\frac{2}{\alpha }}\varGamma (1+\frac{2}{\alpha })\varGamma (1-\frac{2}{\alpha })R^2\) and \(B=\frac{\pi \lambda _e R^2}{A}\). And this completes the proof of Lemma 1.
Appendix B: Proof of Lemma 2
Similar to the proof of Lemma 1, we first provide the coverage probability of cellular links with IC capability follows [27].
where \(\mathcal {L}^{\mathrm {(I)}}(s)=e^{-\lambda _{c,d}2\pi (\phi _1(s)+\phi _2(s)-\phi _3)}\) denotes the Laplace transform for the IC-enabled scenario. Here, \(\phi _1(s)=\frac{1}{2}(sp_d)^{\frac{2}{\alpha }}\varGamma (1+\frac{2}{\alpha })\varGamma (1-\frac{2}{\alpha }), \phi _2(s)=\frac{1}{\alpha }(sp_d)^{\frac{2}{\alpha }}\varGamma (1+\frac{2}{\alpha })\varGamma (-\frac{2}{\alpha },s\tau )\), and \(\phi _3=\frac{1}{\alpha }(\tau ^{-1}p_d)^{\frac{2}{\alpha }}\varGamma (\frac{2}{\alpha })\).
As a result, the secrecy outage probability of CU\(_c\) can be derived as follows,
where \(P=\mathrm {Pr}^{\mathrm {(I)}}(\gamma _c > \mathrm {Th}(x))\). And this completes the proof of Lemma 2.
Appendix C: Proof of Lemma 3
Assuming \(T=2^{R_t}-1\) and \(M=2^{R_t-R_s}-1\) in (14) and (15), then the transmission constraint and the security constraint can be rewritten as \(P_{\mathrm {TC}}=\frac{1-e^{-\hat{A}\lambda _{c,d}}}{\hat{A}\lambda _{c,d}}\) and \(P_{\mathrm {SC}}=e^{-\frac{\hat{B}}{\lambda _{c,d}}}\). Then, an extremum of \(P_{\mathrm {STP}}\) can be computed by its first derivative of \(\lambda _{c,d}\), i.e.,
where \(f(\lambda _{c,d})=e^{\hat{A}\lambda _{c,d}}-\frac{\hat{A}\lambda _{c,d}^2}{\lambda _{c,d}-\hat{B}}-1\). Then, We analyze the existence of the extremum and explain that the extremum is the maximum value.
Existence: Considering the properties of continuous function, we analyse two cases of \(f(\lambda _{c,d})\). Because \(\frac{\mathrm {d} f(\lambda _{c,d})}{\mathrm {d} \lambda _{c,d}}=\hat{A}\left[ e^{\hat{A}\lambda _{c,d}}-1+(\frac{\hat{B}}{\lambda _{c,d}-\hat{B}})^2 \right] >0\) holds and \(f(\lambda _{c,d})\) is continuous, \(f(\lambda _{c,d})\) is larger than zero with \(\lambda _{c,d}\in (0,\hat{B})\). Similarly, there must exists only one solution \(\lambda _{c,d}^*\) to ensure \(f(\lambda _{c,d}) =0\) with \(\lambda _{c,d}\in (\hat{B},+\infty )\).
The Maximum Value: It’s easy to know that \(\frac{\mathrm {d} P_{\mathrm {STP}}^{(\mathrm {N})}}{\mathrm {d} \lambda _{c,d}}>0\) with \(\lambda _{c,d}\in (0,\hat{B})\cap (\hat{B},\lambda _{c,d}^* )\). For the full range of \(\lambda _{c,d}\), we still need to consider \(\frac{\mathrm {d} P_{\mathrm {STP}}^{(\mathrm {N})}(\hat{B})}{\mathrm {d} \lambda _{c,d}}=\frac{\hat{A}}{\hat{B}}e^{-1-\hat{A}\hat{B}}>0\). Similarly, \(\frac{\mathrm {d} P_{\mathrm {STP}}^{(\mathrm {N})}}{\mathrm {d} \lambda _{c,d}}<0\) with \(\lambda _{c,d}\in (\lambda _{c,d}^*,+\infty )\).
According to the above analysis of the extremum of \(P_{\mathrm {STP}}\), we know that \(P_{\mathrm {STP}}^{(\mathrm {N})}\) is a unimodal function of \(\lambda _{c,d}\). And this completes the proof of Lemma 3.
Rights and permissions
Copyright information
© 2018 Springer International Publishing AG, part of Springer Nature
About this paper
Cite this paper
Fan, J., Huo, Y., Fan, X., Hu, C., Jing, G. (2018). A Cooperative Jamming Based Secure Uplink Transmission Scheme for Heterogeneous Networks Supporting D2D Communications. In: Chellappan, S., Cheng, W., Li, W. (eds) Wireless Algorithms, Systems, and Applications. WASA 2018. Lecture Notes in Computer Science(), vol 10874. Springer, Cham. https://doi.org/10.1007/978-3-319-94268-1_9
Download citation
DOI: https://doi.org/10.1007/978-3-319-94268-1_9
Published:
Publisher Name: Springer, Cham
Print ISBN: 978-3-319-94267-4
Online ISBN: 978-3-319-94268-1
eBook Packages: Computer ScienceComputer Science (R0)