Abstract
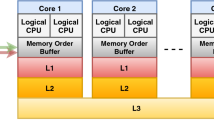
Side-channel attacks are effective attacks against modern cryptographic schemes, which exploit the leaking information besides input and output to the algorithm. As one of the cache-based side-channel attacks, Flush+Reload features high resolution, low noise, and virtual machine compatibility. However, a state-of-the-art Flush+Reload attack only reveals whether the memory address is accessed or not. This paper presents differential Flush+Reload attack that can recover the access sequence of memory addresses, which could lead to new vulnerabilities. The idea is to analyze statistical difference among multiple Flush+Reload results. Specifically, we add controlled delay between the start of victim calculation and the memory flush. Multiple Flush+Reload results with different delays are measured to determine the memory access sequence. Under this concept, we demonstrate the details of a successful recovery of T-table access sequences for an AES implementation from MatrixSSL version 3.9.3 on an Intel CPU.
Access this chapter
Tax calculation will be finalised at checkout
Purchases are for personal use only
Similar content being viewed by others
References
Aciiçmez, O.: Yet another microarchitectural attack: exploiting I-cache. In: Proceedings of the 2007 ACM Workshop on Computer Security Architecture, pp. 11–18. ACM (2007)
Bernstein, D.J.: Cache-timing attacks on AES. Vlsi Des. IEEE Comput. Soc. 51(2), 218–221 (2005)
Brumley, D., Boneh, D.: Remote timing attacks are practical. Comput. Netw. 48(5), 701–716 (2005). https://doi.org/10.1016/j.comnet.2005.01.010
Chen, C., Wang, T., Kou, Y., Chen, X., Li, X.: Improvement of trace-driven I-cache timing attack on the RSA algorithm. J. Syst. Softw. 86(1), 100–107 (2013). https://doi.org/10.1016/j.jss.2012.07.020
Gullasch, D., Bangerter, E., Krenn, S.: Cache games - bringing access-based cache attacks on AES to practice. In: Security and Privacy (SP), IEEE Symposium on 2011, pp. 490–505. IEEE (2011)
Gülmezoğlu, B., İnci, M.S., Irazoqui, G., Eisenbarth, T., Sunar, B.: A faster and more realistic flush+reload attack on AES. In: Mangard, S., Poschmann, A.Y. (eds.) COSADE 2014. LNCS, vol. 9064, pp. 111–126. Springer, Cham (2015). https://doi.org/10.1007/978-3-319-21476-4_8
Hu, W.M.: Lattice scheduling and covert channels. In: Proceedings Research in Security and Privacy, 1992 IEEE Computer Society Symposium on 1992. pp. 52–61. IEEE (1992). DOI: https://doi.org/10.1109/RISP.1992.213271
Irazoqui, G., Inci, M.S., Eisenbarth, T., Sunar, B.: Wait a minute! A fast, cross-VM attack on AES. In: Stavrou, A., Bos, H., Portokalidis, G. (eds.) RAID 2014. LNCS, vol. 8688, pp. 299–319. Springer, Cham (2014). https://doi.org/10.1007/978-3-319-11379-1_15
Kelsey, J., Schneier, B., Wagner, D., Hall, C.: Side channel cryptanalysis of product ciphers. In: Quisquater, J.-J., Deswarte, Y., Meadows, C., Gollmann, D. (eds.) ESORICS 1998. LNCS, vol. 1485, pp. 97–110. Springer, Heidelberg (1998). https://doi.org/10.1007/BFb0055858
Kocher, P.C.: Timing attacks on implementations of diffie-hellman, RSA, DSS, and other systems. In: Koblitz, N. (ed.) CRYPTO 1996. LNCS, vol. 1109, pp. 104–113. Springer, Heidelberg (1996). https://doi.org/10.1007/3-540-68697-5_9
Koeune, F., Standaert, F.-X.: A tutorial on physical security and side-channel attacks. In: Aldini, A., Gorrieri, R., Martinelli, F. (eds.) FOSAD 2004-2005. LNCS, vol. 3655, pp. 78–108. Springer, Heidelberg (2005). https://doi.org/10.1007/11554578_3
Moghimi, A., Irazoqui, G., Eisenbarth, T.: CacheZoom: how SGX amplifies the power of cache attacks. In: Fischer, W., Homma, N. (eds.) CHES 2017. LNCS, vol. 10529, pp. 69–90. Springer, Cham (2017). https://doi.org/10.1007/978-3-319-66787-4_4
Osvik, D.A., Shamir, A., Tromer, E.: Cache attacks and countermeasures: the case of AES. In: Pointcheval, D. (ed.) CT-RSA 2006. LNCS, vol. 3860, pp. 1–20. Springer, Heidelberg (2006). https://doi.org/10.1007/11605805_1
Page, D.: Theoretical use of cache memory as a cryptanalytic side-channel. IACR Cryptol. Eprint Arch. 2002, 169 (2002)
Page, D.: Defending against cache-based side-channel attacks. Inf. Secur. Tech. Rep. 8(1), 30–44 (2003)
Tsunoo, Y., Saito, T., Suzaki, T., Shigeri, M., Miyauchi, H.: Cryptanalysis of DES implemented on computers with cache. In: Walter, C.D., Koç, Ç.K., Paar, C. (eds.) CHES 2003. LNCS, vol. 2779, pp. 62–76. Springer, Heidelberg (2003). https://doi.org/10.1007/978-3-540-45238-6_6
Yarom, Y., Benger, N.: Recovering OpenSSL ecdsa nonces using the flush+reload cache side-channel attack. IACR Cryptol. Eprint Arch. 2014, 140 (2014)
Yarom, Y., Falkner, K.: Flush+reload: a high resolution, low noise, l3 cache side-channel attack. In: Usenix Conference on Security Symposium, pp. 719–732 (2014)
Zhou, Z., Reiter, M.K., Zhang, Y.: A software approach to defeating side channels in last-level caches. In: Proceedings of the 2016 ACM SIGSAC Conference on Computer and Communications Security, pp. 871–882. ACM (2016)
Acknowledgement
This work was supported by National Natural Science Foundation of China 61602239, Jiangsu Province Natural Science Foundation BK20160808 and JSPS KAKENHI Grant Number JP18H05289.
Author information
Authors and Affiliations
Corresponding author
Editor information
Editors and Affiliations
Rights and permissions
Copyright information
© 2018 Springer Nature Switzerland AG
About this paper
Cite this paper
Yuan, Z., Li, Y., Sakiyama, K., Sugawara, T., Wang, J. (2018). Recovering Memory Access Sequence with Differential Flush+Reload Attack. In: Su, C., Kikuchi, H. (eds) Information Security Practice and Experience. ISPEC 2018. Lecture Notes in Computer Science(), vol 11125. Springer, Cham. https://doi.org/10.1007/978-3-319-99807-7_26
Download citation
DOI: https://doi.org/10.1007/978-3-319-99807-7_26
Published:
Publisher Name: Springer, Cham
Print ISBN: 978-3-319-99806-0
Online ISBN: 978-3-319-99807-7
eBook Packages: Computer ScienceComputer Science (R0)