Abstract
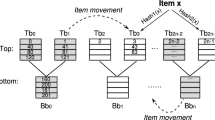
This paper presents a hardware scheme to realize memory integrity verification. Firstly, this paper introduces the general situation of related works; then, brings forward an approach basing on hash tree and MAC combined way to provide memory integrity. This approach integrates the checking principle of hash tree with the authentication ability of MAC, and utilizes their advantages. MAC is used to decrease the space needing to be protected by hash tree. Hash tree is optimized through hot-access-window method, which can reduce the cost of checking process effectively. This paper elaborates how to realize such a hardware memory integrity verification mechanism, also gives some test results. Analysis and experimental simulation show that this approach can provide available memory integrity protection, with significantly good performance.
Access this chapter
Tax calculation will be finalised at checkout
Purchases are for personal use only
Preview
Unable to display preview. Download preview PDF.
Similar content being viewed by others
References
Merkle, R.C.: Protocols for public key cryptography. In: IEEE Symposium on Security and Privacy, pp. 122–134 (1980)
Gassend, B., Suh, G.E., Clarke, D., van Dijk, M., Devadas, S.: Caches and merkle trees for efficient memory authentication. In: Ninth International Symposium on High Performance Computer Architecture (2003)
Clarke, D., Gassend, B., Suh, G.E., van Dijk, M., Devadas, S.: Offline integrity checking of untrusted storage. Technical report, MIT LCS TR-871 (2002)
Suh, G.E., Clarke, D., Gassend, B., van Dijk, M., Devadas, S.: Hardware Mechanisms for Memory Integrity Checking. Technical report, MIT LCS TR-872 (2003)
Maheshwari, U., Vingralek, R., Shapiro, W.: How to Build a Trusted Database System on Untrusted Storage. In: 4th USENIX Symposium on Operationg System Design and Implementation (2000)
Mazieres, D., Shasha, D.: Don’t trust your file server. In: 8th Workshop on Hot Topics in Operating Systems (2001)
Tomonori, F., Masanori, O.: Protecting the Integrity of an Entire File System. In: First IEEE International Workshop on Information Assurance (2003)
Rivest, R.: RFC 1321: The MD5 Message-Digest Algorithm (1992)
Eastlake, D., Jones, P.: RFC 3174: US Secure Hash Algorithm 1, SHA1 (2001)
Intel, Inc.: IA-32 Intel Architecture Software Developer’s Manual Volume 1: Basic Architecture (2003), http://www.intel.com
Author information
Authors and Affiliations
Editor information
Editors and Affiliations
Rights and permissions
Copyright information
© 2004 Springer-Verlag Berlin Heidelberg
About this paper
Cite this paper
Hou, F., Wang, Z., Tang, Y., Liu, J. (2004). Verify Memory Integrity Basing on Hash Tree and MAC Combined Approach. In: Yang, L.T., Guo, M., Gao, G.R., Jha, N.K. (eds) Embedded and Ubiquitous Computing. EUC 2004. Lecture Notes in Computer Science, vol 3207. Springer, Berlin, Heidelberg. https://doi.org/10.1007/978-3-540-30121-9_83
Download citation
DOI: https://doi.org/10.1007/978-3-540-30121-9_83
Publisher Name: Springer, Berlin, Heidelberg
Print ISBN: 978-3-540-22906-3
Online ISBN: 978-3-540-30121-9
eBook Packages: Springer Book Archive