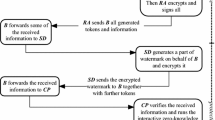
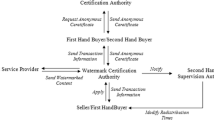
Abstract
The ease and convenience that electronic commerce provides, especially when multimedia material is involved, is helping the growth in the number and volume of electronic transactions through the Internet. But this new type of trading operations has highlighted new problems related to copyright protection. Watermarking seems to be an interesting approach to solve these problems. However, watermarks by themselves do not provide enough protection, but they must be used in certain scenarios fulfilling a number of requirements. In this paper we present the results of the application of a risk analysis technique (specifically ‘attack trees’ technique) to the most demanding schemes developed so far, and a new protocol or business model derived from the main conclusions of this process, which we have called SecDP (Secure Distribution Protocol).
Access this chapter
Tax calculation will be finalised at checkout
Purchases are for personal use only
Preview
Unable to display preview. Download preview PDF.
Similar content being viewed by others
References
Furon, T., Venturini, I., Duhamel, P.: Unified approach of asymmetric watermarking schemes. Security and watermarking of multimedia contents III. In: Wong, P.W., Delp, E. (eds.) Proc. SPIE, vol. 4314, pp. 269–279 (2001)
Piva, A., Bartolini, F., Barni, M.: Managing Copyright in Open Networks. IEEE Internet Computing (2002)
Qian, L., Nahrstedt, K.: Watermarking Schemes and Protocols for Protecting Rightful Ownership and Customer’s Rights. Journal of Visual Communications and Image Representation 9(3), 194–202 (1998)
Memon, N., Wong, P.: A Buyer- Seller Watermarking Protocol. In: IEEE Signal Processing Society. Electronic Proceedings, Los Angeles, USA (1998)
Amoroso, E.: Fundamentals of Computer Security Technology. Prentice Hall PTR, Englewood Cliffs (1994)
Schneier, B.: Modeling security threats. Dr. Dobb’s Journal (1999), http://www.schneier.com/paper-attacktrees-ddj-ft.html
Tomsich, P., Katzenbeisser, S.: Copyright protection protocols for multimedia distribution based on trusted hardware. In: PROMS 2000, Cracow, Poland, pp. 249–256 (2000)
Piva, A., Bartolini, F., Barni, M.: Managing Copyright in Open Networks. IEEE Internet Computing (2002)
Cox, I.J., Miller, M.L., Bloom, J.A.: Digital Watermarking. Morgan Kaufmann, San Francisco (2002)
Goirizelaia, I., Unzilla, J.J.: A new watermarking method using high frequency components to guide the insertion process in the spatial domain. Lectures Notes in Computer Science. Springer, Ljubljana (1999)
Katzenbesisser, S., Peticolas, F.A.P.: Information Hiding: techniques for steganography and digital watermarking. Artech House (2000)
Johnson, N., Duric, Z., Jajodia, S.: Information Hiding: steganography and watermarking – attacks and countermeasures. Kluwer Academic Publishers, Dordrecht (2001)
Peticolas, F.A.P., Anderson, R.J., Jun, M.G.: Attacks on copyright marking systems. In: Aucsmith, D. (ed.) IH 1998. LNCS, vol. 1525, pp. 415–438. Springer, Heidelberg (1998)
Craver, S., Memon, B., Yeo, L., Yeung, M.M.: Resolving Rightful Ownerships with Invisible Watermarking Techniques: Limitations, Attacks, and Implications. IEEE Journal of Selected Areas in Communication 16, 573–586 (1998)
Voloshynovskiy, S., Pereira, S., Pun, T.: Attacks on digital watermarks: classification, estimation-based attacks and benchmarks. IEEE Communications Magazine 39 (2001)
Amenaza Technologies Limited, http://www.amenaza.com
Author information
Authors and Affiliations
Editor information
Editors and Affiliations
Rights and permissions
Copyright information
© 2004 Springer-Verlag Berlin Heidelberg
About this paper
Cite this paper
Higuero, M.V., Unzilla, J.J., Jacob, E., Sáiz, P., Luengo, D. (2004). Application of ‘Attack Trees’ Technique to Copyright Protection Protocols Using Watermarking and Definition of a New Transactions Protocol SecDP (Secure Distribution Protocol). In: Roca, V., Rousseau, F. (eds) Interactive Multimedia and Next Generation Networks. MIPS 2004. Lecture Notes in Computer Science, vol 3311. Springer, Berlin, Heidelberg. https://doi.org/10.1007/978-3-540-30493-7_24
Download citation
DOI: https://doi.org/10.1007/978-3-540-30493-7_24
Publisher Name: Springer, Berlin, Heidelberg
Print ISBN: 978-3-540-23928-4
Online ISBN: 978-3-540-30493-7
eBook Packages: Springer Book Archive