Abstract
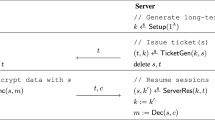
We examine the role of session identifiers (SIDs) in security proofs for key establishment protocols. After reviewing the practical importance of SIDs we use as a case study the three-party server-based key distribution (3PKD) protocol of Bellare and Rogaway, proven secure in 1995. We show incidentally that the partnership function used in the existing security proof is flawed. There seems to be no way to define a SID for the 3PKD protocol that will preserve the proof of security. A small change to the protocol allows a natural definition for a SID and we prove that the new protocol is secure using this SID to define partnering.
This work was partially funded by the Australian Research Council Discovery Project Grant DP0345775.
Preview
Unable to display preview. Download preview PDF.
Similar content being viewed by others
References
Bellare, M.: A Note on Negligible Functions. Journal of Cryptology 15(4), 271–284 (2002)
Bellare, M., Boldyreva, A., Micali, S.: Public-key Encryption in a Multi-User Setting: Security Proofs and Improvements. In: Preneel, B. (ed.) EUROCRYPT 2000. LNCS, vol. 1807, pp. 259–274. Springer, Heidelberg (2000)
Bellare, M., Kilian, J., Rogaway, P.: The Security of the Cipher Block Chaining Message Authentication Code. Journal of Computer and System Sciences 61(3), 362–399 (2000)
Bellare, M., Pointcheval, D., Rogaway, P.: Authenticated Key Exchange Secure Against Dictionary Attacks. In: Preneel, B. (ed.) EUROCRYPT 2000. LNCS, vol. 1807, pp. 139–155. Springer, Heidelberg (2000)
Bellare, M., Rogaway, P.: Entity Authentication and Key Distribution. In: Stinson, D.R. (ed.) CRYPTO 1993. LNCS, vol. 773, pp. 110–125. Springer, Heidelberg (1994)
Bellare, M., Rogaway, P.: Provably Secure Session Key Distribution: The Three Party Case. In: 27th ACM Symposium on the Theory of Computing, pp. 57–66. ACM Press, New York (1995)
Bellovin, S.M., Merritt, M.: Encrypted Key Exchange: Password-Based Protocols Secure Against Dictionary Attacks. In: Symposium on Security and Privacy, pp. 72–84. IEEE, Los Alamitos (1992)
Bellovin, S.M., Merritt, M.: Augmented Encrypted Key Exchange: A Password-Based Protocol Secure Against Dictionary Attacks and Password File Compromise. In: 1st Annual Conference on Computer and Communications Security, pp. 72–84. ACM, New York (1993)
Blake-Wilson, S., Menezes, A.: Security Proofs for Entity Authentication and Authenticated Key Transport Protocols Employing Asymmetric Techniques. In: Security Protocols Workshop. Springer, Heidelberg (1997)
Blake-Wilson, S., Menezes, A.: Authenticated Diffie-Hellman Key Agreement Protocols. In: Tavares, S., Meijer, H. (eds.) SAC 1998. LNCS, vol. 1556, pp. 339–361. Springer, Heidelberg (1999)
Boyd, C., Nieto, J.M.G.: Round-optimal Contributory Conference Key Agreement. In: Desmedt, Y.G. (ed.) PKC 2003. LNCS, vol. 2567, pp. 161–174. Springer, Heidelberg (2002)
Bresson, E., Chevassut, O., Pointcheval, D.: Provably Authenticated Group Diffie-Hellman Key Exchange - The Dynamic Case. In: Boyd, C. (ed.) ASIACRYPT 2001. LNCS, vol. 2248, pp. 209–223. Springer, Heidelberg (2001)
Bresson, E., Chevassut, O., Pointcheval, D.: Dynamic Group Diffie-Hellman Key Exchange under Standard Assumptions. In: Knudsen, L.R. (ed.) EUROCRYPT 2002. LNCS, vol. 2332, pp. 321–336. Springer, Heidelberg (2002)
Bresson, E., Chevassut, O., Pointcheval, D., Quisquater, J.-J.: Provably Authenticated Group Diffie–Hellman Key Exchange. In: 8th ACM Conference on Computer and Communications Security, pp. 209–223. ACM Press, New York (2001)
Canetti, R., Krawczyk, H.: Analysis of Key-Exchange Protocols and Their Use for Building Secure Channels. In: Pfitzmann, B. (ed.) EUROCRYPT 2001. LNCS, vol. 2045, pp. 453–474. Springer, Heidelberg (2001)
Goldwasser, S., Micali, S.: Probabilisitic Encryption. Journal of Computer and System Sciences 28, 270–299 (1984)
Goldwasser, S., Micali, S., Rivest, R.L.: A Digital Signature Scheme Secure Against Adaptive Chosen-Message Attacks. SIAM Journal on Computing 17(2), 281–308 (1988)
The Internet Engineering Task Force. RFC 0204 Sockets in Use (August 1971), http://www.ietf.org/rfc.html/
The Internet Engineering Task Force. RFC 0147 Definition of a Socket (May 1971), http://www.ietf.org/rfc/rfc0147.txt?number=0147
Jakobsson, M., Pointcheval, D.: Mutual Authentication and Key Exchange Protocol for Low Power Devices. In: Syverson, P.F. (ed.) FC 2001. LNCS, vol. 2339, pp. 178–195. Springer, Heidelberg (2002)
Katz, J., Yung, M.: Scalable Protocols for Authenticated Group Key Exchange. In: Boneh, D. (ed.) CRYPTO 2003. LNCS, vol. 2729, pp. 110–125. Springer, Heidelberg (2003)
Shoup, V., Rubin, A.: Session Key Distribution Using Smart Cards. In: Maurer, U.M. (ed.) EUROCRYPT 1996. LNCS, vol. 1070, pp. 321–331. Springer, Heidelberg (1996)
Stallings, W.: Data and Computer Communications, 7th edn. Prentice-Hall, Englewood Cliffs (2004)
Author information
Authors and Affiliations
Editor information
Editors and Affiliations
Rights and permissions
Copyright information
© 2005 Springer-Verlag Berlin Heidelberg
About this paper
Cite this paper
Choo, KK.R., Boyd, C., Hitchcock, Y., Maitland, G. (2005). On Session Identifiers in Provably Secure Protocols. In: Blundo, C., Cimato, S. (eds) Security in Communication Networks. SCN 2004. Lecture Notes in Computer Science, vol 3352. Springer, Berlin, Heidelberg. https://doi.org/10.1007/978-3-540-30598-9_25
Download citation
DOI: https://doi.org/10.1007/978-3-540-30598-9_25
Publisher Name: Springer, Berlin, Heidelberg
Print ISBN: 978-3-540-24301-4
Online ISBN: 978-3-540-30598-9
eBook Packages: Computer ScienceComputer Science (R0)