Abstract
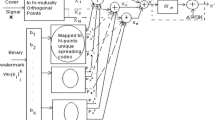
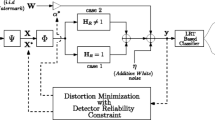
In most existing spread spectrum watermarking algorithms, the embedding parameters, such as the embedding strength and spreading code length, are frequently determined via experiments. In this paper, the theoretical formulas that associate the embedding strength with the user number, or with the spreading code length, are estimated and tested, by analyzing the CDMA (Code Division Multiple Access) spreading strategies in quantization-based data hiding scenario. Moreover, a performance analytical schema in terms of BER (bit error rate) and SNR (signal-to-noise ratio) is proposed and tested both theoretically and experimentally. The interesting conclusions show that the performance of the CDMA-based data-hiding systems, focusing on quantization scheme, is independent of the user number under the constraints of imperceptibility, and an increase of the spreading code length will lead to a decrease of the robust performance. The simulation results are presented to support the conclusions. Although the work presented in this paper focuses on image watermarking, it may be extended to audio/video watermarking.
Support by NSF of China (60325208, 60133020), NSF of Guangdong (04205407), funding of China National Education Ministry.
Preview
Unable to display preview. Download preview PDF.
Similar content being viewed by others
References
Cox, I.J., Miller, M.L., Bloom, J.A.: Digital Watermarking. Morgan Kaufmann, San Francisco (2001)
Fang, Y., Huang, J.: Image Watermarking Algorithm Applying CDMA. In: Proc. of IEEE Int. Sym. on Circuits and Systems, Bangkok, Thailand, vol. 2(5), pp. 948–951 (2003)
Joseph, J.K., Ruanaidh, Ò., Thierry, P.: Rotation, Scale and Translation Invariant Spread Spectrum Digital Image Watermarking. Signal Processing 66(3), 303–317 (1998)
Silvestre, G.C.M., Dowling, W.J.: Embedding Data in Digital Images Using CDMA Techniques. In: Proc. of IEEE Int. Conf. on Image Processing, Vancouver, Canada, vol. 1, pp. 589–592 (2000)
Kohda, T., Ookubo, Y., Shinokura, K.: Digital Watermarking Through CDMA Channels Using Spread Spectrum Techniques. In: IEEE 6th Int. Sym. on Spread Spectrum Techniques and Applications, Parsippany, NJ, USA, vol. 2, pp. 671–674 (2000)
Vassaux, B., Bas, P., Chassery, J.M.: A New CDMA Technique for Digital Image Watermarking Enhancing Capacity of Insertion and Robustness. In: Proc. of IEEE Int. Conf. on Image Processing, Thessalonica, Greece, vol. 3, pp. 983–986 (2001)
Bijan, G.M.: Exploring CDMA for Watermarking of Digital Video, Villanova, PA, USA, 19085, http://www.ece.villanova.edu/~mobasser/mypage/3657-10.pdf
Bijan, G.M.: Direct Sequence Watermarking of Digital Video Using m-frames. In: Proc. of IEEE Int. Conf. on Image Processing, Chicago, Illinois, USA, vol. 2, pp. 399–403 (1998)
Gu, L.M., Huang, J.W., Shi, Y.Q.: Analysis of the Role Played by Error Correcting Coding in Robust Watermarking. In: Proc. of IEEE Int. Sym. on Circuits and Systems, vol. 3(5), pp. 798–801 (2003)
Sencar, H.T., Ramkumar, M., Akansu, A.N.: A Robust Type-III Data Hiding Technique against Cropping & Resizing Attacks. In: Proc. of IEEE Int. Sym. on Circuits and Systems, vol. 2(5), pp. 444–446 (2002)
Tsai, M.J., Yu, K.Y., Chen, Y.Z.: Joint Wavelet and Spatial Transformation for Digital Watermarking. IEEE Trans. On Consumer Electronics 46(1), 241–245 (2000)
Liu, R.Z., Tan, T.N.: A General Watermark Framework for Optimal Energy Estimation, Chinese J. Computer 24(3), 242–246 (2001)
Cao, Z.G., Qian, Y.S.: The Principle of Modern Communication. Tsinghua University Press, Beijing (1992)
Author information
Authors and Affiliations
Editor information
Editors and Affiliations
Rights and permissions
Copyright information
© 2005 Springer-Verlag Berlin Heidelberg
About this paper
Cite this paper
Fang, Y., Gu, L., Huang, J. (2005). Performance Analysis of CDMA-Based Watermarking with Quantization Scheme. In: Deng, R.H., Bao, F., Pang, H., Zhou, J. (eds) Information Security Practice and Experience. ISPEC 2005. Lecture Notes in Computer Science, vol 3439. Springer, Berlin, Heidelberg. https://doi.org/10.1007/978-3-540-31979-5_30
Download citation
DOI: https://doi.org/10.1007/978-3-540-31979-5_30
Publisher Name: Springer, Berlin, Heidelberg
Print ISBN: 978-3-540-25584-0
Online ISBN: 978-3-540-31979-5
eBook Packages: Computer ScienceComputer Science (R0)