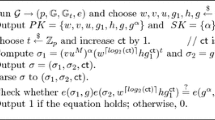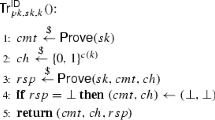Abstract
Kabastianskii, Krouk and Smeets proposed in 1997 a digital signature scheme based on random error-correcting codes. In this paper we investigate the security and the efficiency of their proposal. We show that a passive attacker who may intercept just a few signatures can recover the private key. We give precisely the number of signatures required to achieve this goal. This enables us to prove that all the schemes given in the original paper can be broken with at most 20 signatures. We improve the efficiency of these schemes by firstly providing parameters that enable to sign about 40 messages, and secondly, by describing a way to extend these few-times signatures into classical multi-time signatures. We finally study their key sizes and a mean to reduce them by means of more compact matrices.
Preview
Unable to display preview. Download preview PDF.
Similar content being viewed by others
References
Berlekamp, E.R., McEliece, R.J., van Tilborg, H.C.A.: On the intractability of certain coding problems. IEEE Transactions on Information Theory 24(3), 384–386 (1978)
Canteaut, A., Chabaud, F.: A new algorithm for finding minimum-weight words in a linear code: Application to McEliece’s cryptosystem and to narrow-sense BCH codes of length 511. IEEE Transactions on Information Theory 44(1), 367–378 (1998)
Courtois, N.T., Finiasz, M., Sendrier, N.: How to achieve a McEliece-based digital signature scheme. In: Boyd, C. (ed.) ASIACRYPT 2001. LNCS, vol. 2248, pp. 157–174. Springer, Heidelberg (2001)
Engelbert, D., Overbeck, R., Schmidt, A.: A summary of McEliece-type cryptosystems and their security, Cryptology ePrint Archive, Report 2006/162 (2006), http://eprint.iacr.org/
Gaborit, P.: Shorter keys for code based cryptography. In: WCC 2005. LNCS, vol. 3969, pp. 81–91. Springer, Heidelberg (2006)
Kabatianskii, G., Krouk, E., Smeets, B.J.M.: A digital signature scheme based on random error-correcting codes. In: Darnell, M. (ed.) Cryptography and Coding. LNCS, vol. 1355, pp. 161–167. Springer, Heidelberg (1997)
Lamport, L.: Constructing digital signatures from a one way function, Tech. Report CSL-98, SRI International (October 1979)
Lee, P.J., Brickell, E.F.: An observation on the security of McEliece’s public-key cryptosystem. In: Günther, C.G. (ed.) EUROCRYPT 1988. LNCS, vol. 330, pp. 275–280. Springer, Heidelberg (1988)
Leon, J.S.: A probabilistic algorithm for computing minimum weights of large error-correcting codes. IEEE Transactions on Information Theory 34(5), 1354–1359 (1988)
Li, Y.X., Deng, R.H., Wang, X.-M.: On the equivalence of McEliece’s and Niederreiter’s public-key cryptosystems. IEEE Transactions on Information Theory 40(1), 271–273 (1994)
MacWilliams, F.J., Sloane, N.J.A.: The theory of error-correcting codes, 5th edn. North–Holland, Amsterdam (1986)
McEliece, R.J.: A public-key system based on algebraic coding theory, pp. 114–116, Jet Propulsion Lab, DSN Progress Report 44 (1978)
Merkle, R.C.: A certified digital signature. In: Brassard, G. (ed.) CRYPTO 1989. LNCS, vol. 435, pp. 218–238. Springer, Heidelberg (1989)
Niederreiter, H.: Knapsack-type cryptosystems and algebraic coding theory. Problems Control Inform. Theory 15(2), 159–166 (1986)
Perrig, A.: The BiBa one-time signature and broadcast authentication protocol. In: Proceedings of the 8th ACM Conference on Computer and Communications Security, pp. 28–37. ACM Press, New York (2001)
Reyzin, L., Reyzin, N.: Better than BiBa: Short One-Time Signatures with Fast Signing and Verifying. In: Batten, L.M., Seberry, J. (eds.) ACISP 2002. LNCS, vol. 2384, pp. 144–153. Springer, Heidelberg (2002)
Stern, J.: A method for finding codewords of small weight. In: Wolfmann, J., Cohen, G. (eds.) Coding Theory and Applications. LNCS, vol. 388, pp. 106–113. Springer, Heidelberg (1989)
Stern, J.: A new identification scheme based on syndrome decoding. In: Stinson, D.R. (ed.) CRYPTO 1993. LNCS, vol. 773, pp. 13–21. Springer, Heidelberg (1994)
Véron, P.: Problème SD, opérateur trace, schémas d’identification et codes de goppa, Ph.D. thesis, Université Toulon et du Var, Toulon, France (1995)
Author information
Authors and Affiliations
Editor information
Rights and permissions
Copyright information
© 2007 Springer-Verlag Berlin Heidelberg
About this paper
Cite this paper
Cayrel, PL., Otmani, A., Vergnaud, D. (2007). On Kabatianskii-Krouk-Smeets Signatures. In: Carlet, C., Sunar, B. (eds) Arithmetic of Finite Fields. WAIFI 2007. Lecture Notes in Computer Science, vol 4547. Springer, Berlin, Heidelberg. https://doi.org/10.1007/978-3-540-73074-3_18
Download citation
DOI: https://doi.org/10.1007/978-3-540-73074-3_18
Publisher Name: Springer, Berlin, Heidelberg
Print ISBN: 978-3-540-73073-6
Online ISBN: 978-3-540-73074-3
eBook Packages: Computer ScienceComputer Science (R0)