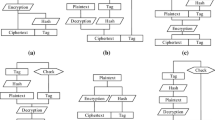
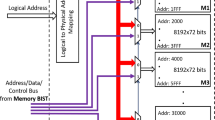
Abstract
Replay attacks are often the most costly attacks to thwart when dealing with off-chip memory integrity. With a trusted System-on-Chip, the existing countermeasures against replay require a large amount of on-chip memory to provide tamper-proof storage for metadata such as hash values or nonces. Tree-based strategies can be deployed to reduce this unacceptable overhead; for example, the well-known Merkle tree technique decreases this overhead to a single hash value. However, it comes at the cost of performance-killing characteristics for embedded systems – e.g. non-parallelizable hash computations on tree updates. In this paper, we propose an alternative solution: the Tamper-Evident Counter Tree (TEC-Tree). It allows for tamper-evident off-chip storage of the nonces involved in a replay countermeasure; TEC-Tree parallelizes the computations involved in both the authentication and tree update processes. Moreover, because our tree relies on block encryption, it provides data confidentiality at no extra cost. TEC-Tree is a deployable solution for memory integrity, with low performance hit and hardware cost.
Chapter PDF
Similar content being viewed by others
Keywords
References
Kocher, P., Lee, R.B., McGraw, G., Raghunathan, A., Ravi, S.: Security as a New Dimension in Embedded System Design. In: Proceedings of the Design Automation Conference (DAC), pp. 753–760 (June 2004)
Huang, A.: Keeping Secrets in Hardware the Microsoft Xbox Case Study. MIT AI Memo (2002)
Kuhn, M.G.: Cipher Instruction Search Attack on the Bus-Encryption Security Microcontroller DS5002FP. IEEE Trans. Comput. 47, 1153–1157 (1998)
Fruhwirth, C.: New Methods in Hard Disk Encryption. Institute for Computer Languages, Theory and Logic Group, Vienna University of Technology (2005)
Elbaz, R., Torres, L., Sassatelli, G., Guillemin, P., Bardouillet, M., Martinez, A.: A Parallelized Way to Provide Data Encryption and Integrity Checking on a Processor-Memory Bus. In: Proceedings of the 43rd Design Automation Conference DAC (July 2006)
Elbaz, R.: Hardware Mechanisms for Secured Processor Memory Transactions in Embedded Systems. PhD Thesis, University of Montpellier (December 2006)
Merkle, R.C.: Protocols for Public Key Cryptography. In: IEEE Symp. on Security and Privacy, pp. 122–134 (1980)
Gassend, B., Suh, G.E., Clarke, D., van Dijk, M., Devadas, S.: Caches and Merkle Trees for Efficient Memory Integrity Verification. In: Proceedings of Ninth International Symposium on High Performance Computer Architecture (February 2003)
Yan, C., Rogers, B., Englender, D., Solihin, Y., Prvulovic, M.: Improving Cost, Performance, and Security of Memory Encryption and Authentication. In: Proc. of the International Symposium on Computer Architecture (2006)
Hall, W.E., Jutla, C.S.: Parallelizable authentication trees. In: Cryptology ePrint Archive (December 2002)
Hall, W.E., Jutla, C.S.: Parallelizable Authentication Tree for Random Access Storage. U.S. Patent No. 2004/0107341 A1 (June 2004)
Suh, G.E.: AEGIS: A Single-Chip Secure Processor. PhD thesis, Massachusetts Institute of Technology (September 2005)
Shannon, C.: Communication theory of secrecy systems. Bell System Technical Journal, 28 (1949)
Daemen, J., Rijmen, V.: AES Proposal: Rijndael (March 1999), available at: http://csrc.nist.gov/CryptoToolkit/aes/rijndael/Rijndael-ammended.pdf
Author information
Authors and Affiliations
Editor information
Rights and permissions
Copyright information
© 2007 Springer-Verlag Berlin Heidelberg
About this paper
Cite this paper
Elbaz, R., Champagne, D., Lee, R.B., Torres, L., Sassatelli, G., Guillemin, P. (2007). TEC-Tree: A Low-Cost, Parallelizable Tree for Efficient Defense Against Memory Replay Attacks. In: Paillier, P., Verbauwhede, I. (eds) Cryptographic Hardware and Embedded Systems - CHES 2007. CHES 2007. Lecture Notes in Computer Science, vol 4727. Springer, Berlin, Heidelberg. https://doi.org/10.1007/978-3-540-74735-2_20
Download citation
DOI: https://doi.org/10.1007/978-3-540-74735-2_20
Publisher Name: Springer, Berlin, Heidelberg
Print ISBN: 978-3-540-74734-5
Online ISBN: 978-3-540-74735-2
eBook Packages: Computer ScienceComputer Science (R0)