Abstract
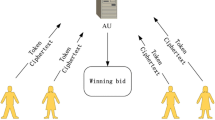
We modified the multi-agent negotiation test-bed which was proposed by Collins et al. In 2004, Jaiswal et al. have modified Collins’s scheme, but Jaiswal’s scheme still has some security weaknesses: such as replay data attack and DOS (denial-of-service) attack, anonymity disclosure, collision between customers and a certain supplier. So the proposed protocol tries to reduce DOS attack and avoids replay data attack by providing ticket token and deal sequence number to the supplier. It utilizes efficient LPN-based authentication method to accomplish lightweight authentication. And it publishes an interpolating polynomial for sharing the determination process data and avoids collusion between a customer and a certain supplier. Also the proposed scheme relaxes the trust assumptions for three-party in Jaiswal’s scheme. According to comparison and analysis with other protocols, our proposed protocol shows good security and less computation cost.
Preview
Unable to display preview. Download preview PDF.
Similar content being viewed by others
References
Collins, J., Ketter, W., Gini, M.: A multi-agent negotiation testbed for contracting tasks with temporal and precedence constraints. International Journal of Electronic Commerce 7(1), 35–57 (2002)
Jaiswal, A., kim, Y., Gini, M.: design and implementation of a secure multi-agent marketplace. Electronic Commerce Research and Applications 3(4), 355–368 (2004)
Chang, C.C., Chang, Y.F.: Efficient anonymous auction protocols with freewheeling bids. computer & security 22(8), 728–734 (2003)
Jiang, R., Pan, L., Li, J.H.: An improvement on efficient anonymous auction protocols. computer & security 24(2), 169–174 (2005)
Chang, Y.F., Chang, C.C.: Enhanced anonymous auction protocols with freewheeling bids. In: Proceedings of 20th International Conference on Advanced Information Networking and Applications(AINA), vol. 1, pp. 353–358 (2006)
Hwang, M.S., Lu, E.J.L., Lin, I.C.: Adding timestamps to the electronic auction protocol. Data & Knowledge Engineering 40(2), 155–162 (2002)
Liaw, H.-T., Juang, W.-S., Lin, C.-K.: An electronic online bidding auction protocol with both security and efficiency. Applied Mathematics and Computation 174(2), 1487–1497 (2006)
Rivest, R.L., Shamir, A., Wagner, D.A.: Time-lock puzzles and timed-release crypto, Technical Report MIT/LCS/TR-684. MIT Press, Cambridge (1996)
Ingemaresson, I., Tang, T.D., Wong, C.K.: A conference key distribution system. IEEE Trans. Info. Theory 28(5), 714–720 (1982)
Tang, Q., Mitchell, C.J.: Comments on two anonymous conference key distribution systems. Computer Standards & Interfaces 27(4), 397–400 (2005)
Regev, O.: On Lattices, Learning with errors, Random Linear Codes. and Cryptography. In: 37th ACM symposium on theory of computing, pp. 84–93 (2005)
Juels, A., Weis, S.: Authenticating pervasive devices with human protocols. In: Shoup, V. (ed.) CRYPTO 2005. LNCS, vol. 3621, pp. 293–308. Springer, Heidelberg (2005)
Gilbert, H., Robshaw, M., Silbert, H.: An active attack against HB+ – a provable secure lightweight authentication protocol. Cryptology ePrint Archive, Report 2005/237 (2005)
Kesdogan, D., Palmer, C.: Technical challenges of network anonymity. Computer Communications 29(3), 306–324 (2006)
Buttyan, L., Ben Salem, N.: A Payment Scheme for Broadcast Multimedia Streams. In: Proceedings of the 6th IEEE Symposium on Computers and Communications, pp. 668–673 (2001)
Fan, C.-I., Chan, Y.-C., Zhang, Z.-K.: Robust remote authentication scheme with smart cards. Computers & Security 24(8), 619–628 (2005)
Chang, C.C., Lail, C.S., Harn, L.: Contemporary Cryptography and its Applications, 2nd edn. Unalis Co (2001)
Author information
Authors and Affiliations
Editor information
Rights and permissions
Copyright information
© 2008 Springer-Verlag Berlin Heidelberg
About this paper
Cite this paper
Shi, W., Jang, I., Yoo, H.S. (2008). An Efficient Electronic Marketplace Bidding Auction Protocol with Bid Privacy. In: Zhang, Y., Yu, G., Bertino, E., Xu, G. (eds) Progress in WWW Research and Development. APWeb 2008. Lecture Notes in Computer Science, vol 4976. Springer, Berlin, Heidelberg. https://doi.org/10.1007/978-3-540-78849-2_31
Download citation
DOI: https://doi.org/10.1007/978-3-540-78849-2_31
Publisher Name: Springer, Berlin, Heidelberg
Print ISBN: 978-3-540-78848-5
Online ISBN: 978-3-540-78849-2
eBook Packages: Computer ScienceComputer Science (R0)