Abstract
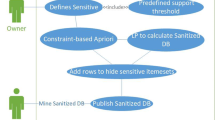
Frequent pattern mining is a popular topic in data mining. With the advance of this technique, privacy issues attract more and more attention in recent years. In this field, previous works based hiding sensitive information on a uniform support threshold or a disclosure threshold. However, in practical applications, we probably need to apply different support thresholds to different itemsets for reflecting their significance. In this paper, we propose a new hiding strategy to protect sensitive frequent patterns with multiple sensitive thresholds. Based on different sensitive thresholds, the sanitized dataset is able to highly fulfill user requirements in real applications, while preserving more information of the original dataset. Empirical studies show that our approach can protect sensitive knowledge well not only under multiple thresholds, but also under a uniform threshold. Moreover, the quality of the sanitized dataset can be maintained.
Preview
Unable to display preview. Download preview PDF.
Similar content being viewed by others
References
Agrawal, R., Imieliński, T., Swami, A.: Mining Associations Rule Between Sets of Items in Massive Database. In: Proc. of the ACM SIGMOD Int. Conf. on Management of Data, pp. 207–216 (1993)
Clifton, C., Marks, D.: Security and Privacy Implication of Data Mining. In: ACM SIGMOD Workshop on Data Mining and Knowledge Discovery, pp. 15–19 (1996)
Chen, X., Orlowska, M., Li, X.: A New Framework of Privacy Preserving Data Sharing. In: Proc. of IEEE 4th Int. Workshop on Privacy and Security Aspects of Data Mining, pp. 47–56 (2004)
Wang, E.T., Lee, G., Lin, Y.T.: A Novel Method for Protecting Sensitive Knowledge in Association Rules Mining. In: Proc. of the 29th Annual Int. COMPSAC, vol. 1, pp. 511–516 (2005)
Wu, Y.H., Chiang, C.M., Chen, A.L.P.: Hiding Sensitive Association Rules with Limited Side Effects. IEEE Transactions on Knowledge and Data Engineering 19(1), 29–42 (2007)
Verykios, V.S., Elmagarmid, A., Bertino, E., Saygin, Y., Dasseni, E.: Association Rule Hiding. IEEE Transactions on Knowledge and Data Engineering 16(4), 434–447 (2004)
Xingzhi, S., Yu, P.S.: A Border-Based Approach for Hiding Sensitive Frequent Itemsets. In: Proc. of 5th IEEE Int. Conf. on Data Mining, pp. 426–433 (2005)
Lee, Y.C., Hong, T.P., Lin, W.Y.: Mining Association Rules with Multiple Minimum Supports Using Maximum Constraints. Int. Journal of Approximate Reasoning on Data Mining and Granular Computing 40(1–2), 44–54 (2005)
Atallah, M., Bertino, E., Elmagarmid, A., Ibrahim, M., Verykios, V.: Disclosure Limitation of Sensitive Rules. In: Proc. of the IEEE Knowledge and Data Exchange Workshop, pp. 45–52 (1999)
Gkoulalas-Divanis, A., Verykios, V.S.: An Integer Programming Approach for Frequent Itemset Hiding. In: Proc. of Int. Conf. on Information and Knowledge Management, pp. 748–757 (2006)
Mielikainen, T.: On Inverse Frequent Set Mining. In: Proc. of the 2nd IEEE ICDM Workshop on Privacy Preserving Data Mining (2003)
Wu, X., Wu, Y., Wang, Y., Li, Y.: Privacy-Aware Market Basket Data Set Generation: A Feasible Approach for Inverse Frequent Set Mining. In: Proc. 5th SIAM Int. Conf. on Data Mining (2005)
Guo, Y.: Reconstruction-Based Association Rule Hiding. In: Proc. of SIGMOD 2007 Ph.D. Workshop on Innovative Database Research (2007)
Liu, B., Hsu, W., Ma, Y.: Mining Association Rules with Multiple Minimum Supports. In: Proc. of the 5th ACM SIGKDD Int. Conf. on Knowledge Discovery and Data Mining, pp. 337–341 (1999)
Wang, K., Fung, B.C.M., Yu, P.S.: Template-Based Privacy Preservation in Classification Problems. In: Proc. - IEEE Int. Conf. on Data Mining, pp. 466–473 (2005)
Dwork, C.: Ask a Better Question, Get a Better Answer: A New Approach to Private Data Analysis. In: Schwentick, T., Suciu, D. (eds.) ICDT 2007. LNCS, vol. 4353, pp. 18–27. Springer, Heidelberg (2006)
Oliveira, S.R.M., Zaíane, O.R.: A Unified Framework for Protecting Sensitive Association Rules in Business Collaboration. Int. J. of Business Intelligence and Data Mining 1(3), 247–287 (2006)
Wang, K., He, Y., Han, J.: Pushing Support Constraints into Association Rules Mining. IEEE Transactions on Knowledge and Data Engineering 15(3), 642–658 (2003)
Geurts, K., Wets, G., Brijs, T., Vanhoof, K.: Profiling High-Frequency Accident Locations Using Association Rules. In: Proc. of the 82th Annual Transportation Research Board, p. 18 (2003)
Blake, C.L., Merz, C.J.: UCIRepository of machine learning databases. University of Califarnia, Dept. of Inf. and CS, Irvine (1998), http://www.ics.uci.edu/~mlearn/MLRepository.html
Author information
Authors and Affiliations
Editor information
Rights and permissions
Copyright information
© 2008 Springer-Verlag Berlin Heidelberg
About this paper
Cite this paper
Kuo, YP., Lin, PY., Dai, BR. (2008). Hiding Frequent Patterns under Multiple Sensitive Thresholds. In: Bhowmick, S.S., Küng, J., Wagner, R. (eds) Database and Expert Systems Applications. DEXA 2008. Lecture Notes in Computer Science, vol 5181. Springer, Berlin, Heidelberg. https://doi.org/10.1007/978-3-540-85654-2_2
Download citation
DOI: https://doi.org/10.1007/978-3-540-85654-2_2
Publisher Name: Springer, Berlin, Heidelberg
Print ISBN: 978-3-540-85653-5
Online ISBN: 978-3-540-85654-2
eBook Packages: Computer ScienceComputer Science (R0)