Abstract
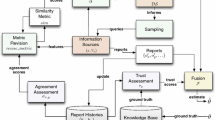
We present a trust-based mechanism for the acquisition of information from possibly unreliable sources. Our mechanism addresses the case where the acquired information cannot be verified. The idea is to intersperse questions (“challenges”) for which the correct answers are known. By evaluating the answers to these challenges, probabilistic conclusions about the correctness of the unverifiable information can be drawn. Less challenges need to be used if an information provider has shown to be trustworthy. This work focuses on three major issues of such a mechanism. First, how to estimate the correctness of the unverifiable information. Second, how to determine an optimal number of challenges. And finally, how to establish trust and use it to reduce the number of challenges. Our approach can resist collusion and shows great promise for various application areas such as distributed computing or peer-to-peer networks.
Preview
Unable to display preview. Download preview PDF.
Similar content being viewed by others
References
Sabater, J., Sierra, C.: Review on computational trust and reputation models. Artif. Intell. Rev. 24(1), 33–60 (2005)
Ramchurn, S.D., Huynh, T.D., Jennings, N.R.: Trust in multi-agent systems. Knowl. Eng. Rev. 19(1), 1–25 (2004)
Anderson, D.P., Cobb, J., Korpela, E., Lebofsky, M., Werthimer, D.: SETI@home: An experiment in public-resource computing. Commun. ACM 45(11), 56–61 (2002)
Rehák, M., Pechoucek, M.: Trust modeling with context representation and generalized identities. In: Klusch, M., Hindriks, K.V., Papazoglou, M.P., Sterling, L. (eds.) CIA 2007. LNCS (LNAI), vol. 4676, pp. 298–312. Springer, Heidelberg (2007)
Berman, F., Fox, G., Hey, A.J.G.: Grid Computing: Making the Global Infrastructure a Reality. John Wiley & Sons, Inc., New York (2003)
Weiss, A.: Computing in the clouds. netWorker 11(4), 16–25 (2007)
Toh, C.K.: Ad Hoc Wireless Networks: Protocols and Systems. Prentice Hall PTR, Upper Saddle River (2001)
Christin, N., Weigend, A.S., Chuang, J.: Content availability, pollution and poisoning in file sharing peer-to-peer networks. In: EC 2005: Proc. of the 6th ACM Conf. on Electronic commerce, pp. 68–77. ACM Press, New York (2005)
Abdul-Rahman, A., Hailes, S.: Supporting trust in virtual communities. In: HICSS 2000: Proc. of the 33rd Hawaii Int. Conf. on System Sciences. IEEE Computer Society Press, Los Alamitos (2000)
Rohatgi, V.K.: Statistical Inference. Dover Publications, Incorporated, Mineola (2003)
Kinateder, M., Baschny, E., Rothermel, K.: Towards a generic trust model - comparison of various trust update algorithms. In: Herrmann, P., Issarny, V., Shiu, S.C.K. (eds.) Trust 2005. LNCS, vol. 3477, pp. 177–192. Springer, Heidelberg (2005)
Wang, Y., Singh, M.P.: Formal trust model for multiagent systems. In: IJCAI 2007: Proc. of the 20th Int. Joint Conf. on Artificial Intelligence, pp. 1551–1556 (2007)
Teacy, W.T.L., Patel, J., Jennings, N.R., Luck, M.: Travos: Trust and reputation in the context of inaccurate information sources. Auton. Agents Multi-Agent Syst. 12(2), 183–198 (2006)
Jaynes, E.T.: Probability Theory: The Logic of Science. Cambridge University Press, Cambridge (2003)
Montgomery, D.C.: Introduction to Statistical Quality Control, 5th edn. John Wiley, Chichester (2004)
Dumais, S.T., Furnas, G.W., Landauer, T.K., Deerwester, S., Harshman, R.: Using latent semantic analysis to improve access to textual information. In: CHI 1988: Proc. of the SIGCHI Conf. on Human Factors in Computing Systems, pp. 281–285. ACM, New York (1988)
Hofmann, T.: Probabilistic latent semantic indexing. In: SIGIR 1999: Proc. of the 22nd annual Int. ACM SIGIR Conf. on Research and Development in Information Retrieval, pp. 50–57. ACM, New York (1999)
Karypis, G., Han, E.: Concept indexing: A fast dimensionality reduction algorithm with applications to document retrieval and categorization. Technical Report TR-00-0016, University of Minnesota (2000)
Dearden, R., Friedman, N., Andre, D.: Model based bayesian exploration. In: UAI 1999: Proc. of the 15th Conf. on Uncertainty in Artificial Intelligence, pp. 150–159 (1999)
Chalkiadakis, G., Boutilier, C.: Coordination in multiagent reinforcement learning: a bayesian approach. In: AAMAS 2003: Proc. of the 2nd Int. Joint Conf. on Autonomous Agents and Multiagent Systems, pp. 709–716. ACM Press, New York (2003)
Buchegger, S., Boudec, J.Y.L.: A robust reputation system for mobile ad hoc networks. Technical Report IC/2003/50, EPFL-IC-LCA, CH-1015 Lausanne (July 2003)
Jøsang, A., Ismail, R.: The beta reputation system. In: Proc. of the 15th Bled Conf. on Electronic Commerce, pp. 324–337 (2002)
Fullam, K.K., Park, J., Barber, K.S.: Trust-driven information acquisition for secure and quality decision-making. In: KIMAS 2005: Proc. of Int. Conf. on Integration of Knowledge Intensive Multi-Agent Systems, pp. 303–310 (2005)
Liau, C.J.: Belief, information acquisition, and trust in multi-agent systems: a modal logic formulation. Artif. Intell. 149(1), 31–60 (2003)
Otway, D., Rees, O.: Efficient and timely mutual authentication. SIGOPS Oper. Syst. Rev. 21(1), 8–10 (1987)
Steiner, J.G., Neuman, C., Schiller, J.I.: Kerberos: An authentication service for open network systems. In: Proc. of the Winter 1988 Usenix Conference, pp. 191–2024 (1988)
Author information
Authors and Affiliations
Editor information
Rights and permissions
Copyright information
© 2008 Springer-Verlag Berlin Heidelberg
About this paper
Cite this paper
Staab, E., Fusenig, V., Engel, T. (2008). Towards Trust-Based Acquisition of Unverifiable Information. In: Klusch, M., Pěchouček, M., Polleres, A. (eds) Cooperative Information Agents XII. CIA 2008. Lecture Notes in Computer Science(), vol 5180. Springer, Berlin, Heidelberg. https://doi.org/10.1007/978-3-540-85834-8_6
Download citation
DOI: https://doi.org/10.1007/978-3-540-85834-8_6
Publisher Name: Springer, Berlin, Heidelberg
Print ISBN: 978-3-540-85833-1
Online ISBN: 978-3-540-85834-8
eBook Packages: Computer ScienceComputer Science (R0)