Abstract
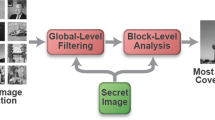
This paper presents a cover selection steganography method based on introduction of a technique for computing steganography capacity as a property of images. An ensemble system that uses different steganalyzer units, determines the upper bound of embedding rate in a cover image. In this technique, each steganalyzer unit is a combination of multiple steganalyzers with a same type but each one trained to detect stego images with a certain payload. Our proposed method minimizes the risk of detection by selecting a proper cover image that its steganography capacity is sufficient to hide a specific secret data securely. Experimental results demonstrate the efficiency and practicability of the proposed technique in enhancing the security of stego images.
Preview
Unable to display preview. Download preview PDF.
Similar content being viewed by others
References
Sallee, P.: Model-based steganography. In: Kalker, T., Cox, I., Ro, Y.M. (eds.) IWDW 2003. LNCS, vol. 2939, pp. 154–167. Springer, Heidelberg (2004)
Fridrich, J., Goljan, M., Soukal, D.: Perturbed quantization steganography with wet paper codes. In: ACM Multimedia Workshop, Germany (2004)
Solanki, K., Sarkar, A., Manjunath, B.S.: YASS: yet another steganographic scheme that resists blind steganalysis. In: Furon, T., Cayre, F., Doërr, G., Bas, P. (eds.) IH 2007. LNCS, vol. 4567, pp. 16–31. Springer, Heidelberg (2008)
Chandramouli, R., Memon, N.D.: Steganography Capacity: A Steganalysis Perspective. In: SPIE Security and Watermarking of Multimedia Contents, vol. 5020, pp. 173–177 (2003)
Fridrich, J., Pevny, T., Kodovsky, J.: Statistically Undetectable JPEG Steganography: Dead Ends, Challenges, and Opportunities. In: MM&Sec, USA (2007)
Cachin, C.: An information-theoretic model for steganography. In: Aucsmith, D. (ed.) IH 1998. LNCS, vol. 1525, pp. 306–318. Springer, Heidelberg (1998)
Moulin, P., Mihcak, M.K.: A framework for evaluating the data hiding capacity of image sources. IEEE Trans. Image Processing 11, 1029–1042 (2002)
Dong, Y., Han, K.: Boosting SVM classifiers by ensemble. In: International conference ACM on World Wide Web, pp. 1072–1073 (2005)
Ker, A.: A Capacity Result for Batch Steganography. IEEE Signal Processing Let. 14(8), 525–528 (2007)
Kharrazi, M., Sencar, T.H., Memon, N.: Benchmarking steganographic and steganalysis, techniques. In: EI SPIE, San Jose, CA (2005)
Avcibas, I., Kharrazi, M., Memon, N., Sankur, B.: Image steganalysis with binary similarity measures. EURASIP Journal on Applied Signal Processing (2005)
Lyu, S., Farid, H.: Detecting hidden messages using higher-order statistics and support vector machines. In: Petitcolas, F.A.P. (ed.) IH 2002. LNCS, vol. 2578, pp. 340–354. Springer, Heidelberg (2003)
Lyu, S., Farid, H.: Steganalysis using color wavelet statistics and one-class support vector machines. In: SPIE Symposium on Electronic Imaging, San Jose, CA (2004)
Fridrich, J.: Feature-based steganalysis for jpeg images and its implications for future design of steganographic schemes. In: Fridrich, J. (ed.) IH 2004. LNCS, vol. 3200, pp. 67–81. Springer, Heidelberg (2004)
Dietterich, T.G.: Ensemble methods in machine learning. In: Kittler, J., Roli, F. (eds.) MCS 2000. LNCS, vol. 1857, pp. 1–15. Springer, Heidelberg (2000)
Burges, C.J.C.: A tutorial on support vector machines for pattern recognition. Data Mining and Knowledge Discovery 2, 121–167 (1998)
Pevny, T., Fridrich, J.: Merging Markov and DCT features for multi-class JPEG steganalysis. In: SPIE, San Jose, CA (2007)
Chen, C., Shi, Y.Q., Chen, W., Xuan, G.: Statistical moments based universal steganalysis using JPEG-2D array and 2-D characteristic function. In: ICIP, pp. 105–108 (2006)
Sajedi, H., Jamzad, M.: A Steganalysis Method Based on Contourlet Transform Coefficients. In: Intelligent Information Hiding and Multimedia Signal Processing (2008)
Kermani, Z.Z., Jamzad, M.: A Robust Steganography Algorithm Based On Texture Similarity Using Gabor Filter. In: IEEE Symposium on Signal processing and Information Technology, pp. 578–582 (2005)
Sajedi, H., Jamzad, M.: Cover Selection Steganography Method Based on Similarity of Image Blocks. In: IEEE CIT, Sydney, Australia (2008)
Kharrazi, M., Sencar, H., Memon, N.: Cover Selection for Steganographic Embedding. In: ICIP, pp. 117–121 (2006)
Washington University image database, http://www.cs.washington.edu/research/imagedatabase
Author information
Authors and Affiliations
Editor information
Editors and Affiliations
Rights and permissions
Copyright information
© 2009 Springer-Verlag Berlin Heidelberg
About this paper
Cite this paper
Sajedi, H., Jamzad, M. (2009). Secure Cover Selection Steganography. In: Park, J.H., Chen, HH., Atiquzzaman, M., Lee, C., Kim, Th., Yeo, SS. (eds) Advances in Information Security and Assurance. ISA 2009. Lecture Notes in Computer Science, vol 5576. Springer, Berlin, Heidelberg. https://doi.org/10.1007/978-3-642-02617-1_33
Download citation
DOI: https://doi.org/10.1007/978-3-642-02617-1_33
Publisher Name: Springer, Berlin, Heidelberg
Print ISBN: 978-3-642-02616-4
Online ISBN: 978-3-642-02617-1
eBook Packages: Computer ScienceComputer Science (R0)