Abstract
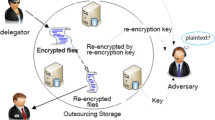
A proxy re-encryption (PRE) scheme supports the delegation of decryption rights via a proxy, who makes the ciphertexts decryptable by the delegatee. PRE is useful in various applications such as encrypted email forwarding. In this paper, we introduce a more generalized notion of conditional proxy broadcast re-encryption (CPBRE). A CPBRE scheme allows Alice to generate a re-encryption key for some condition specified during the encryption, such that the re-encryption power of the proxy is restricted to that condition only. This enables a more fine-grained delegation of decryption right. Moreover, Alice can delegate decryption rights to a set of users at a time. That is, Alice’s ciphertexts can be re-broadcasted. This saves a lot of computation and communication cost. We propose a basic CPBRE scheme secure against chosen-plaintext attacks, and its extension which is secure against replayable chosen-ciphertext attacks (RCCA). Both schemes are unidirectional and proved secure in the standard model. Finally, we show that it is easy to get a unidirectional RCCA-secure identity-based proxy re-encryption from our RCCA-secure CPBRE construction.
Funded by A*STAR project SEDS-0721330047.
Preview
Unable to display preview. Download preview PDF.
Similar content being viewed by others
References
Ateniese, G., Fu, K., Green, M., Hohenberger, S.: Improved proxy re-encryption schemes with applications to secure distributed storage. In: Proceedings of the Network and Distributed System Security Symposium (NDSS 2005). The Internet Society (2005)
Attrapadung, N., Furukawa, J., Imai, H.: Forward-secure and searchable broadcast encryption with short ciphertexts and private keys. In: Lai, X., Chen, K. (eds.) ASIACRYPT 2006. LNCS, vol. 4284, pp. 161–177. Springer, Heidelberg (2006)
Blaze, M., Bleumer, G., Strauss, M.: Divertible protocols and atomic proxy cryptography. In: Nyberg, K. (ed.) EUROCRYPT 1998. LNCS, vol. 1403, pp. 127–144. Springer, Heidelberg (1998)
Boneh, D., Boyen, X.: Efficient selective-id secure identity-based encryption without random oracles. In: Cachin, C., Camenisch, J.L. (eds.) EUROCRYPT 2004. LNCS, vol. 3027, pp. 223–238. Springer, Heidelberg (2004)
Boneh, D., Gentry, C., Waters, B.: Collusion resistant broadcast encryption with short ciphertexts and private keys. In: Shoup, V. (ed.) CRYPTO 2005. LNCS, vol. 3621, pp. 258–275. Springer, Heidelberg (2005)
Boneh, D., Goh, E.-J., Matsuo, T.: Proposal for P1363.3 proxy re-encryption (2006), http://grouper.ieee.org/groups/1363/IBC/submissions
Boyen, X., Mei, Q., Waters, B.: Direct chosen ciphertext security from identity-based techniques. In: Proceedings of the 12th ACM Conference on Computer and Communications Security - CCS 2005, pp. 320–329. ACM Press, New York (2005)
Canetti, R., Hohenberger, S.: Chosen-ciphertext secure proxy re-encryption. In: Proceedings of ACM Conference on Computer and Communications Security (CCS 2007), pp. 185–194. ACM Press, New York (2007)
Canetti, R., Krawczyk, H., Nielsen, J.B.: Relaxing chosen-ciphertext security. In: Boneh, D. (ed.) CRYPTO 2003. LNCS, vol. 2729, pp. 565–582. Springer, Heidelberg (2003)
Chu, C.-K., Tzeng, W.-G.: Identity-based proxy re-encryption without random oracles. In: Garay, J.A., Lenstra, A.K., Mambo, M., Peralta, R. (eds.) ISC 2007. LNCS, vol. 4779, pp. 189–202. Springer, Heidelberg (2007)
Deng, R.H., Weng, J., Liu, S., Chen, K.: Chosen-ciphertext secure proxy re-encryption without pairings. In: Franklin, M.K., Hui, L.C.K., Wong, D.S. (eds.) CANS 2008. LNCS, vol. 5339, pp. 1–17. Springer, Heidelberg (2008)
Green, M., Ateniese, G.: Identity-based proxy re-encryption. In: Katz, J., Yung, M. (eds.) ACNS 2007. LNCS, vol. 4521, pp. 288–306. Springer, Heidelberg (2007)
Libert, B., Vergnaud, D.: Tracing malicious proxies in proxy re-encryption. In: Galbraith, S.D., Paterson, K.G. (eds.) Pairing 2008. LNCS, vol. 5209, pp. 332–353. Springer, Heidelberg (2008)
Libert, B., Vergnaud, D.: Unidirectional chosen-ciphertext secure proxy re-encryption. In: Cramer, R. (ed.) PKC 2008. LNCS, vol. 4939, pp. 360–379. Springer, Heidelberg (2008)
Matsuo, T.: Proxy re-encryption systems for identity-based encryption. In: Takagi, T., Okamoto, T., Okamoto, E., Okamoto, T. (eds.) Pairing 2007. LNCS, vol. 4575, pp. 247–267. Springer, Heidelberg (2007)
Shao, J., Cao, Z.: CCA-secure proxy re-encryption without pairings. In: Jarecki, S., Tsudik, G. (eds.) PKC 2009. LNCS, vol. 5443, pp. 357–376. Springer, Heidelberg (2009)
Tang, Q.: Type-based proxy re-encryption and its construction. In: Soomaruga, G. (ed.) Formal Theories of Information. LNCS, vol. 5363, pp. 130–134. Springer, Heidelberg (2008)
Weng, J., Deng, R.H., Ding, X., Chu, C.-K., Lai, J.: Conditional proxy re-encryption secure against chosen-ciphertext attack. In: Proceedings of ACM Symposium on Information, Computer & Communication Security (ASIACCS 2009). ACM Press, New York (to appear, 2009)
Weng, J., Deng, R.H., Liu, S., Chen, K., Lai, J., Wang, X.: Chosen-ciphertext secure proxy re-encryption schemes without pairings. Technical report, Cryptology ePrint Archive: Report 2008/509 (Version 3) (2008)
Author information
Authors and Affiliations
Editor information
Editors and Affiliations
Rights and permissions
Copyright information
© 2009 Springer-Verlag Berlin Heidelberg
About this paper
Cite this paper
Chu, CK., Weng, J., Chow, S.S.M., Zhou, J., Deng, R.H. (2009). Conditional Proxy Broadcast Re-Encryption. In: Boyd, C., González Nieto, J. (eds) Information Security and Privacy. ACISP 2009. Lecture Notes in Computer Science, vol 5594. Springer, Berlin, Heidelberg. https://doi.org/10.1007/978-3-642-02620-1_23
Download citation
DOI: https://doi.org/10.1007/978-3-642-02620-1_23
Publisher Name: Springer, Berlin, Heidelberg
Print ISBN: 978-3-642-02619-5
Online ISBN: 978-3-642-02620-1
eBook Packages: Computer ScienceComputer Science (R0)