Abstract
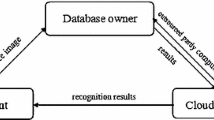
Face recognition is increasingly deployed as a means to unobtrusively verify the identity of people. The widespread use of biometrics raises important privacy concerns, in particular if the biometric matching process is performed at a central or untrusted server, and calls for the implementation of Privacy-Enhancing Technologies. In this paper we propose for the first time a strongly privacy-enhanced face recognition system, which allows to efficiently hide both the biometrics and the result from the server that performs the matching operation, by using techniques from secure multiparty computation. We consider a scenario where one party provides a face image, while another party has access to a database of facial templates. Our protocol allows to jointly run the standard Eigenfaces recognition algorithm in such a way that the first party cannot learn from the execution of the protocol more than basic parameters of the database, while the second party does not learn the input image or the result of the recognition process. At the core of our protocol lies an efficient protocol for securely comparing two Pailler-encrypted numbers. We show through extensive experiments that the system can be run efficiently on conventional hardware.
Supported in part by the European Commission through the IST Programme under Contract IST-2006-034238 SPEED and by CASED (www.cased.de).
Preview
Unable to display preview. Download preview PDF.
Similar content being viewed by others
References
The Database of Faces, (formerly ‘The ORL Database of Faces’) AT&T Laboratories Cambridge, http://www.cl.cam.ac.uk/research/dtg/attarchive/facedatabase.html
Avidan, S., Butman, M.: Blind vision. In: Leonardis, A., Bischof, H., Pinz, A. (eds.) ECCV 2006. LNCS, vol. 3953, pp. 1–13. Springer, Heidelberg (2006)
Blake, I.F., Kolesnikov, V.: Strong Conditional Oblivious Transfer and Computing on Intervals. In: Lee, P.J. (ed.) ASIACRYPT 2004. LNCS, vol. 3329, pp. 515–529. Springer, Heidelberg (2004)
Blake, I.F., Kolesnikov, V.: Conditional Encrypted Mapping and Comparing Encrypted Numbers. In: Di Crescenzo, G., Rubin, A. (eds.) FC 2006. LNCS, vol. 4107, pp. 206–220. Springer, Heidelberg (2006)
Bowcott, O.: Interpol wants facial recognition database to catch suspects. Guardian (October 20, 2008), http://www.guardian.co.uk/world/2008/oct/20/interpol-facial-recognition
Canny, J.F.: Collaborative filtering with privacy. In: IEEE Symposium on Security and Privacy, pp. 45–57 (2002)
Cramer, R., Damgård, I., Nielsen, J.B.: Multiparty Computation from Threshold Homomorphic Encryption. In: Pfitzmann, B. (ed.) EUROCRYPT 2001. LNCS, vol. 2045, pp. 280–299. Springer, Heidelberg (2001)
Damgård, I., Geisler, M., Krøigaard, M.: Efficient and Secure Comparison for On-Line Auctions. In: Pieprzyk, J., Ghodosi, H., Dawson, E. (eds.) ACISP 2007. LNCS, vol. 4586, pp. 416–430. Springer, Heidelberg (2007)
Damgård, I., Geisler, M., Krøigaard, M.: A correction to Efficient and secure comparison for on-line auctions. Cryptology ePrint Archive, Report 2008/321 (2008), http://eprint.iacr.org/
Damgård, I., Jurik, M.: A Generalization, a Simplification and some Applications of Paillier’s Probabilistic Public-Key System. Technical report, Department of Computer Science, University of Aarhus (2000)
Du, W., Han, Y.S., Chen, S.: Privacy-preserving multivariate statistical analysis: Linear regression and classification. In: Proceedings of the Fourth SIAM International Conference on Data Mining, Lake Buena Vista, Florida, USA, April 22-24, pp. 222–233. SIAM, Philadelphia (2004)
Dufaux, F., Ebrahimi, T.: Scrambling for video surveillance with privacy. In: 2006 Conference on Computer Vision and Pattern Recognition Workshop (CVPRW 2006). IEEE Press, Los Alamitos (2006)
Erkin, Z., Piva, A., Katzenbeisser, S., et al.: Protection and retrieval of encrypted multimedia content: When cryptography meets signal processing. EURASIP Journal on Information Security, Article ID 78943 (2007)
Fischlin, M.: A Cost-Effective Pay-Per-Multiplication Comparison Method for Millionaires. In: Naccache, D. (ed.) CT-RSA 2001. LNCS, vol. 2020, pp. 457–472. Springer, Heidelberg (2001)
Garay, J.A., Schoenmakers, B., Villegas, J.: Practical and Secure Solutions for Integer Comparison. In: Okamoto, T., Wang, X. (eds.) PKC 2007. LNCS, vol. 4450, pp. 330–342. Springer, Heidelberg (2007)
Goethals, B., Laur, S., Lipmaa, H., Mielikainen, T.: On secure scalar product computation for privacy-preserving data mining. In: Park, C.-s., Chee, S. (eds.) ICISC 2004. LNCS, vol. 3506, pp. 104–120. Springer, Heidelberg (2005)
Goldreich, O., Micali, S., Wigderson, A.: How to Play any Mental Game or A Completeness Theorem for Protocols with Honest Majority. In: ACM Symposium on Theory of Computing – STOC 1987, May 25-27, pp. 218–229. ACM Press, New York (1987)
Grose, T.: When surveillance cameras talk. Time Magazine (February 11, 2008), http://www.time.com/time/world/article/0,8599,1711972,00.html
Interpol wants facial recognition database to catch suspects. Heise Online UK (March 20, 2008), http://www.heise-online.co.uk/news/British-police-build-a-database-of-portrait-photos-for-facial–recognition–110363
Jacobsson, M., Juels, A.: Mix and match: Secure function evaluation via ciphertexts. In: Okamoto, T. (ed.) ASIACRYPT 2000. LNCS, vol. 1976, pp. 162–177. Springer, Heidelberg (2000)
Jagannathan, G., Wright, R.N.: Privacy-preserving distributed k-means clustering over arbitrarily partitioned data. In: KDD 2005: Proceeding of the eleventh ACM SIGKDD international conference on Knowledge discovery in data mining, pp. 593–599. ACM Press, New York (2005)
Kerschbaum, F., Atallah, M.J., M’Raïhi, D., Rice, J.R.: Private fingerprint verification without local storage. In: Zhang, D., Jain, A.K. (eds.) ICBA 2004. LNCS, vol. 3072, pp. 387–394. Springer, Heidelberg (2004)
Kevenaar, T.: Protection of Biometric Information. In: Security with Noisy Data, pp. 169–193. Springer, Heidelberg (2007)
Kruger, L., Jha, S., Goh, E.-J., Boneh, D.: Secure function evaluation with ordered binary decision diagrams. In: Proceedings of the 13th ACM conference on Computer and communications security CCS 2006, Virginia, U.S.A, pp. 410–420. ACM Press, New York (2006)
Magnier, M.: Many eyes will watch visitors. Los Angeles Times (August 07, 2008), http://articles.latimes.com/2008/aug/07/world/fg-snoop7
Naor, M., Nissim, K.: Communication complexity and secure function evaluation. Electronic Colloquium on Computational Complexity (ECCC), 8(062) (2001)
Naor, M., Nissim, K.: Communication preserving protocols for secure function evaluation. In: ACM Symposium on Theory of Computing, pp. 590–599 (2001)
Naor, M., Pinkas, B., Sumner, R.: Privacy preserving auctions and mechanism design. In: ACM Conference on Electronic Commerce, pp. 129–139 (1999)
Paillier, P.: Public-Key Cryptosystems Based on Composite Degree Residuosity Classes. In: Stern, J. (ed.) EUROCRYPT 1999. LNCS, vol. 1592, pp. 223–238. Springer, Heidelberg (1999)
Ratha, N., Connell, J., Bolle, R., Chikkerur, S.: Cancelable biometrics: A case study in fingerprints. In: Proceedings of the 18th International Conference on Pattern Recognition (ICPR), vol. IV, pp. 370–373. IEEE Press, Los Alamitos (2006)
Schoenmakers, B., Tuyls, P.: Computationally Secure Authentication with Noisy Data. In: Security with Noisy Data, pp. 141–149. Springer, Heidelberg (2007)
Senior, A., Oankanti, A., Hampapur, A., et al.: Enabling video privacy through computer vision. IEEE Security and Privacy Magazine 3(3), 50–57 (2005)
Smaragdis, P., Shashanka, M.: A framwork for secure speech recognition. IEEE Transactions on Audio, Speech and Language Processing 15(4), 1404–1413 (2007)
Turk, M.A., Pentland, A.P.: Eigenfaces for Recognition. Journal of Cognitive Neuroscience 3(1), 71–86 (1991)
Turk, M.A., Pentland, A.P.: Face recognition using eigenfaces. In: IEEE Computer Society Conference on Computer Vision and Pattern Recognition, pp. 586–591 (1991)
Tuyls, P., Akkermans, A.H.M., Kevenaar, T.A.M., Schrijen, G.-J., Bazen, A.M., Veldhuis, R.N.J.: Practical biometric authentication with template protection. In: Kanade, T., Jain, A., Ratha, N.K. (eds.) AVBPA 2005. LNCS, vol. 3546, pp. 436–446. Springer, Heidelberg (2005)
Vaidya, J., Tulpule, B.: Enabling better medical image classification through secure collaboration. In: Proc. IEEE International Conference on Image Processing (ICIP), pp. IV–461–IV–464 (2007)
Yao, A.C.-C.: Protocols for Secure Computations (Extended Abstract). In: Annual Symposium on Foundations of Computer Science – FOCS 1982, November 3-5, pp. 160–164. IEEE Computer Society Press, Los Alamitos (1982)
Yu, X., Chinomi, K., Koshimizu, et al.: Privacy protecting visual processing for secure video surveillance. In: IEEE International Conference on Image Processing (ICIP 2008). IEEE Computer Society Press, Los Alamitos (2008)
Author information
Authors and Affiliations
Editor information
Editors and Affiliations
Rights and permissions
Copyright information
© 2009 Springer-Verlag Berlin Heidelberg
About this paper
Cite this paper
Erkin, Z., Franz, M., Guajardo, J., Katzenbeisser, S., Lagendijk, I., Toft, T. (2009). Privacy-Preserving Face Recognition. In: Goldberg, I., Atallah, M.J. (eds) Privacy Enhancing Technologies. PETS 2009. Lecture Notes in Computer Science, vol 5672. Springer, Berlin, Heidelberg. https://doi.org/10.1007/978-3-642-03168-7_14
Download citation
DOI: https://doi.org/10.1007/978-3-642-03168-7_14
Publisher Name: Springer, Berlin, Heidelberg
Print ISBN: 978-3-642-03167-0
Online ISBN: 978-3-642-03168-7
eBook Packages: Computer ScienceComputer Science (R0)