Abstract
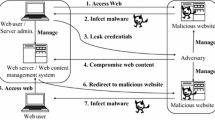
Malicious Web content poses a serious threat to the Internet, organizations and users. Current approaches to detecting malicious Web content employ high-powered honey clients to scan the Web for potentially malicious pages. These approaches, while effective at detecting malicious content, have the drawbacks of being few and far between, presenting a single snapshot in time of very dynamic phenomena, and having artificial test data. To address these problems, we developed a virtualized Web browser that uses large-scale collaboration to identify URLs that host malicious content on a continuing basis by building in an elective reporting system. The system, which we call a Web canary, runs a standard Web browser in a known, pristine OS every time the browser starts. Users not only report malicious URLs but also benefit from protection against malicious content. Experimental results show that it can detect the malicious Web pages effectively with acceptable overhead.
This work was supported in part by DARPA under contract W31P4Q-07-C-0244 and the National Science Foundation under grant CNS-0716323.
Access this chapter
Tax calculation will be finalised at checkout
Purchases are for personal use only
Preview
Unable to display preview. Download preview PDF.
Similar content being viewed by others
References
Wang, Y.-M., Beck, D., Jiang, X., Roussev, R., Verbowski, C., Chen, S., King, S.: Automated Web Patrol with Strider HoneyMonkeys: Finding Web Sites That Exploit Browser Vulnerabilities. In: 13th Annual Network and Distributed System Security Symposium, Internet Society, San Diego (2006)
MITRE HoneyClient, http://www.honeyclient.org/trac
Capture HPC client honeypot, https://projects.honeynet.org/capture-hpc
VMware, http://www.VMware.com
Sapuntzakis, C., Lam, M.: Virtual appliances in the collective: A road to hassle-free computing. In: Workshop on Hot Topics in Operating Systems, pp. 55–60 (2003)
Jackson, C., Bortz, A., Boneh, D., Mitchell, J.: Protecting Browser State from Web Privacy Attacks. In: Proc. WWW (2006)
Ross, B., Jackson, C., Miyake, N., Boneh, D., Mitchell, J.: Stronger Password Authentication Using Browser Extensions. In: Proc. USENIX Security (2005)
Zhang, Y., Egelman, S., Cranor, L.F., Hong, J.: Phinding Phish: Evaluating Anti-Phishing Tools. In: Proceedings of the 14th Annual Network & Distributed System Security Symposium (NDSS 2007), San Diego, CA (2007)
Know Your Enemy: Malicious Web Servers, http://www.honeynet.org/papers/mws/
Provos, N., McNamee, D., Mavrommatis, P., Wang, K., Modadugu, N.: The Ghost In The Browser -Analysis of Web-based Malware. In: Proceedings of the 2007 HotBots, Usenix, Cambridge (2007)
Cox, R., Gribble, S., Levy, H., Hansen, J.: A safety-oriented platform for Web applications. In: Proceedings of the 2006 IEEE Symposium on Security and Privacy, Washington, DC (May 2006)
Moshchuk, et al.: SpyProxy: Execution-based Detection of Malicious Web Content - Usenix 2007 (2007)
ForceField (August 2008), http://download.zonealarm.com/bin/forcefield_x/index.html
IE7 Protected Mode (August 2008), http://www.microsoft.com/windows/windows-vista/features/IE7-protected-mode.aspx
Chong, S., Liu, J., Myers, A.C., Qi, X., Vikram, K., Zheng, L., Zheng, X.: Secure web applications via automatic partitioning. In: Proceedings of the 21st ACM Symposium on Operating Systems Principles (SOSP 2007) (October 2007)
Howell, J., Jackson, C., Wang, H.J., Fan, X.: MashupOS: Operating system abstractions for client mashups. In: Proceedings of the Workshop on Hot Topics in Operating Systems (May 2007)
Browser Appliance (August 2008), http://www.vmware.com/appliances/directory/815
Reis, C., Dunagan, J., Wang, H.J., Dubrovsky, O., Esmeir, S.: BrowserShield: vulnerability-driven filtering of dynamic HTML. In: Proceedings of the 7th conference on USENIX Symposium on OSDI, Seattle, WA, November 6-8 (2006)
Zhang, J., Porras, P.: Highly Predictive Blacklisting. In: Proceedings of 17th USENIX Security Symposium (July 2008)
Barth, A., Jackson, C., Reis, C.: The Security Architecture of the Chromium Browser, Technical report (2008)
Grier, C., Tang, S., King, S.T.: Secure Web Browsing with the OP Web Browser. In: Proceedings of the 2008 IEEE Symposium on Security and Privacy, Oakland (May 2008)
Author information
Authors and Affiliations
Editor information
Editors and Affiliations
Rights and permissions
Copyright information
© 2009 ICST Institute for Computer Science, Social Informatics and Telecommunications Engineering
About this paper
Cite this paper
Wang, J., Ghosh, A., Huang, Y. (2009). Web Canary: A Virtualized Web Browser to Support Large-Scale Silent Collaboration in Detecting Malicious Web Sites. In: Bertino, E., Joshi, J.B.D. (eds) Collaborative Computing: Networking, Applications and Worksharing. CollaborateCom 2008. Lecture Notes of the Institute for Computer Sciences, Social Informatics and Telecommunications Engineering, vol 10. Springer, Berlin, Heidelberg. https://doi.org/10.1007/978-3-642-03354-4_3
Download citation
DOI: https://doi.org/10.1007/978-3-642-03354-4_3
Publisher Name: Springer, Berlin, Heidelberg
Print ISBN: 978-3-642-03353-7
Online ISBN: 978-3-642-03354-4
eBook Packages: Computer ScienceComputer Science (R0)