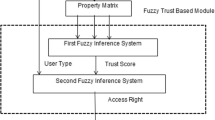
Abstract
Trust-based access control model uses the value of users’ static trust corresponding to the static attributes to get security of access control. However, facing the large number of users in the open system, the calculation of trust not only includes the static properties but also the context information with the ever-changing environment in the system. Using the fixed value to express the trust of the user to grant permissions without considering the dynamic context information may reduce the effectively of access control. Therefore, this paper proposes to use the fuzzy theory into the trust-based access control to solve the problem of dynamic access control by constructing reasonable structure with the fuzzy membership interval of the context information, along with establishing fuzzy rules for fuzzy inference.
Preview
Unable to display preview. Download preview PDF.
Similar content being viewed by others
References
Sandhu, R., Coyne, E., Feinstein, H.: Role-based Access Control Models. IEEE Computer 29(2), 38–47 (1996)
Ray, I., Chakraborty, S.: TrustBAC-Integrating Trust Relationships into the RBAC Model for Access Control in Open Sytems. In: SACMAT 2006, Lake Tahoe, California, USA, pp. 7–9 (2006)
Weiser, M.: The computer for the twenty-first century. Scientific American 265(3), 94–104 (1991)
Sandhu, S.: The ARBAC 1997 Model for Role-Based Administration of Roles: Preliminary Description and Outline. In: Proceedings of the second ACM workshop on Role-based access control, November 1997, pp. 41–50 (1997)
Zhang, L., Wang, X.: Trustworthiness-based fuzzy adaptive access control model for pervasive computing. Application Research of Computers (1), 311–316 (2009)
Hilary, H.H.: Security is fuzzy: applying the fuzzy logic paradigm to the multipolicy paradigm. In: Proc. of the ACM Workshop on New Security Paradigms, pp. 175–184. ACM Press, New York (1993)
Janczewski, L.J., Portougal, V.: Need-to-know principle and fuzzy security clearances modeling. Information Management & Computer Security 8(5), 210–217 (2000)
Chang, E., Thomson, P., Dillon, T., et al.: The fuzzy and dynamic nature of trust. In: Katsikas, S.K., López, J., Pernul, G. (eds.) TrustBus 2005. LNCS, vol. 3592, pp. 161–174. Springer, Heidelberg (2005)
Charalampos, P., Karamolegkos, P., Voulodimos, A., et al.: Security and privacy in pervasive computing. IEEE Pervasive Computing 6(4), 73–75 (2007)
Author information
Authors and Affiliations
Editor information
Editors and Affiliations
Rights and permissions
Copyright information
© 2009 Springer-Verlag Berlin Heidelberg
About this paper
Cite this paper
Su, R., Zhang, Y., He, Z., Fan, S. (2009). Trust-Based Fuzzy Access Control Model Research. In: Liu, W., Luo, X., Wang, F.L., Lei, J. (eds) Web Information Systems and Mining. WISM 2009. Lecture Notes in Computer Science, vol 5854. Springer, Berlin, Heidelberg. https://doi.org/10.1007/978-3-642-05250-7_42
Download citation
DOI: https://doi.org/10.1007/978-3-642-05250-7_42
Publisher Name: Springer, Berlin, Heidelberg
Print ISBN: 978-3-642-05249-1
Online ISBN: 978-3-642-05250-7
eBook Packages: Computer ScienceComputer Science (R0)