Abstract
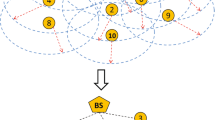
Topology Maintenance in Wireless Sensor Networks (WSNs), that is, alternating duty cycles with sleep cycles while having an adequate number of nodes monitoring the environment, is a necessary requirement to allow the WSNs to move from niche applications to widespread adoption; topology maintenance is even mandatory when the WSNs are used in a security sensitive context.
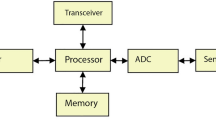
In this work, we present the first scalable Secure Topology Maintenance Protocol (Sec-TMP) for Wireless Sensor Networks that does not require pair-wise node confidentiality. The aim of Sec-TMP is to enforce event delivery to the BS while providing a standard topology maintenance service to the WSN. Sec-TMP enjoys the following features: it does not require pair-wise node confidentiality; it does not need any underlying routing—just one-hop communications are used; and, it is highly scalable. Sec-TMP reaches its goal being also resilient to the known attacks on TMPs: snooze attack; sleep deprivation attack; and, network substitution attack. Furthermore, Sec-TMP confines node replication attack: once a node is captured, the protocol limits the possible usage of the corresponding node’s ID to a single neighbourhood. Finally, extensive simulations support our findings.
This work is partially supported by Caspur under grant HPC-2007.
Access this chapter
Tax calculation will be finalised at checkout
Purchases are for personal use only
Preview
Unable to display preview. Download preview PDF.
Similar content being viewed by others
References
Akyildiz, I.F., Su, W., Sankarasubramaniam, Y., Cayirci, E.: Wireless sensor networks: a survey. International Journal of Computer and Telecommunications Networking - Elsevier 38(4), 393–422 (2002)
Anastasi, G., Conti, M., Francesco, M.D., Passarella, A.: Mobile Ad Hoc and Pervasive Communications. In: How to Prolong the Lifetime of Wireless Sensor Networks, ch. 6. American Scientific Publishers (2007)
Basagni, S., Carosi, A., Melachrinoudis, E., Petrioli, C., Wang, Z.M.: Controlled sink mobility for prolonging wireless sensor networks lifetime. ACM/Springer Journal on Wireless Networks (WINET) 14(6), 831–858 (2008)
Bryan, P., Perrig, A., Gligor, V.: Distributed detection of node replication attacks in sensor networks. In: Proc. of the 26th IEEE International Symposium on Security and Privacy (S&P 2005), pp. 49–63 (2005)
Cerpa, A., Estrin, D.: Ascent: Adaptive self-configuring sensor networks topologies. IEEE Transactions on Mobile Computing 3(3), 272–285 (2004)
Chen, B., Jamieson, K., Balakrishnan, H., Morris, R.: Span: An energy-efficient coordination algorithm for topology maintenance in ad hoc wireless networks. ACM Wireless Networks Journal 8(5), 481–494 (2002)
Conti, M., Di Pietro, R., Mancini, L.V.: Ecce: Enhanced cooperative channel establishment for secure pair-wise communication in wireless sensor networks. Ad Hoc Networks (Elsevier) 5(1), 49–62 (2007)
Conti, M., Di Pietro, R., Mancini, L.V., Mei, A.: A randomized, efficient, and distributed protocol for the detection of node replication attacks in wireless sensor networks. In: Proc. of the 8th ACM International Symposium on Mobile Ad Hoc Networking and Computing (MobiHoc 2007), pp. 80–89 (2007)
Crossbow Technology Inc. MICA Sensor Node, http://www.xbow.com
Di Pietro, R., Mancini, L.V., Mei, A.: Energy efficient node-to-node authentication and communication confidentiality in wireless sensor networks. Wireless Sensor Networks 12(6), 709–721 (2006)
Di Pietro, R., Mancini, L.V., Soriente, C., Spognardi, A., Tsudik, G.: Catch me (if you can): Data survival in unattended sensor networks. In: Proc. of the 6th IEEE International Conference on Pervasive Computing and Communications (PERCOM 2008), pp. 185–194 (2008)
Eschenauer, L., Gligor, V.D.: A key-management scheme for distributed sensor networks. In: Proc. of the 9th ACM International Conference on Computer and Communications Security (CCS 2002), pp. 41–47 (2002)
Ye, F., Zhong, G., Lu, S., Zhang, L.: Peas: A robust energy conserving protocol for long-lived sensor networks. In: Proc. of the 23rd IEEE International Conference on Distributed Computing System (ICDCS 2003), pp. 28–37 (2003)
Gabrielli, A., Mancini, L.V.: Bio-inspired topology maintenance protocols for secure wireless sensor networks. In: Liò, P., Yoneki, E., Crowcroft, J., Verma, D.C. (eds.) BIOWIRE 2007. LNCS, vol. 5151, pp. 399–410. Springer, Heidelberg (2008)
Gabrielli, A., Mancini, L.V., Setia, S., Jajodia, S.: Securing topology maintenance protocols for sensor networks: Attacks and countermeasures. In: Proc. of the 1st IEEE/CreateNet International Conference on Security and Privacy for Emerging Areas in Communication Networks (SecureComm 2005), pp. 101–112 (2005)
Jiang, Z., Wu, J., Agah, A., Lu, B.: Topology control for secured coverage in wireless sensor networks. In: Proc. of the 4th IEEE International Conference on Mobile Adhoc and Sensor Systems (MASS 2007), pp. 1–6 (2007)
Karlof, C., Sastry, N., Wagner, D.: Tinysec: A link layer security architecture for wireless sensor networks. In: SenSys 2004, pp. 162–175 (2004)
Karlof, C., Wagner, D.: Secure routing in wireless sensor networks: attacks and countermeasures. Ad Hoc Networks 1(2-3), 293–315 (2003)
Newsome, J., Shi, E., Song, D., Perrig, A.: The sybil attack in sensor networks: Analysis & defenses. In: Proc. of the 3rd IEEE and ACM International Symposium on Information Processing in Sensor Networks (IPSN 2004), pp. 259–268 (2004)
Rhee, I., Warrier, A., Aia, M., Min, J., Sichitiu, M.L.: Z-mac: a hybrid mac for wireless sensor networks. IEEE/ACM Transactions on Networking 16(3), 511–524 (2008)
Stajano, F., Anderson, R.: The resurrecting duckling: Security issues for ad-hoc wireless networks. In: Proc. of the 7th International Workshop on Security Protocols, pp. 172–182 (1999)
Wander, A., Gura, N., Eberle, H., Gupta, V., Shantz, S.C.: Energy analysis of public-key cryptography for wireless sensor networks. In: PERCOM 2005, pp. 324–328 (2005)
Wang, X., Xing, G., Zhang, Y., Lu, C., Pless, R., Gill, C.: Integrated coverage and connectivity configuration in wireless sensor networks. In: Proc. of the 1st ACM International Conference on Embedded Networked Sensor Systems (SenSys 2003), pp. 28–39 (2003)
Wang, Y., Li, F., Dahlberg, T.A.: Energy-efficient topology control for three-dimensional sensor networks. International Journal of Sensor Networks 4(1/2), 68–78 (2008)
Xu, Y., Heidemann, J., Estrin, D.: Adaptive Energy-Conserving Routing for Multihop Ad Hoc Networks. Research Report 527, USC/Information Sciences Institute (2000)
Xu, Y., Heidemann, J., Estrin, D.: Geography-informed energy conservation for ad hoc routing. In: Proc. of the 7th ACM International Conference on Mobile Computing and Networking (MobiCom 2001), pp. 70–84 (2001)
Zhu, S., Setia, S., Jajodia, S.: Leap: Efficient security mechanisms for large-scale distributed sensor networks. In: Proc. of the 10th ACM International Conference on Computer and Communications Security (CCS 2003), pp. 62–72 (2003)
Author information
Authors and Affiliations
Editor information
Editors and Affiliations
Rights and permissions
Copyright information
© 2009 ICST Institute for Computer Science, Social Informatics and Telecommunications Engineering
About this paper
Cite this paper
Gabrielli, A., Conti, M., Di Pietro, R., Mancini, L.V. (2009). Sec-TMP: A Secure Topology Maintenance Protocol for Event Delivery Enforcement in WSN. In: Chen, Y., Dimitriou, T.D., Zhou, J. (eds) Security and Privacy in Communication Networks. SecureComm 2009. Lecture Notes of the Institute for Computer Sciences, Social Informatics and Telecommunications Engineering, vol 19. Springer, Berlin, Heidelberg. https://doi.org/10.1007/978-3-642-05284-2_15
Download citation
DOI: https://doi.org/10.1007/978-3-642-05284-2_15
Publisher Name: Springer, Berlin, Heidelberg
Print ISBN: 978-3-642-05283-5
Online ISBN: 978-3-642-05284-2
eBook Packages: Computer ScienceComputer Science (R0)