Abstract
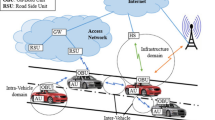
Broadcast is frequently used operation in vehicular adhoc network (VANETs) for sharing traffic, weather, and safety information among vehicles. Relevance based approach forward high priority traffic for information sharing and removes the redundant and surplus messages. The relevance based approach depends upon the intermediate nodes and consider ideal scenario where there is no selfish and malicious node but it is not possible in real life scenario. We in this paper simulate the relevance based approach using NS-2 in a real scenario and consider the impact of malicious node and determine how much throughput of network is affected by malicious node.
Access this chapter
Tax calculation will be finalised at checkout
Purchases are for personal use only
Preview
Unable to display preview. Download preview PDF.
Similar content being viewed by others
References
Ni, S.-Y., Tseng, Y.-C., Chen, Y.-S., Sheu, J.-P.: The broadcast storm problem in mobile ad hoc networks. In: Proc. ACM MobiCom 1999, Seatle, USA (August 1999)
Williams, B., Camp, T.: Comparison of Broadcasting Techniques for Mobile Ad Hoc Networks. In: ACM MOBIHOC (2002)
Yoo, J., Gil, H.-r., Kim, C.-k.: INK: Implicit Neighbor Knowledge Routing in Ad Hoc Networks. IEEE, Los Alamitos (2003)
Osafune, T., Lin, L., Lenardi, M.: Multi-Hop Vehicular Broadcast (MHVB). In: 6th Intermational Coference on ITS Teleconuiiic&ations (2006)
Kosch, T., Adler, C.J., Eichler, S., Schroth, C., Strassberger, M.: The scalability problem of vehicular ad hoc networks and how to solve it. IEEE Wireless Communications (October 2006)
Rahim, A., Yasin, M., Ahmad, I., Khan, Z.S., Sher, M.: Relevance Based Approach with Virtual Queue Using 802.11e protocol for Vehicular Adhoc Networks. In: 2nd International conference on Computer, Control and Communication, Karachi, February 14 (2009)
Eichler, S., Schroth, C., Kosch, T., Strassberger, M.: Strategies for context-adaptive message dissemination in vehicular ad hoc networks. In: e Second International Workshop on Vehicle-to-Vehicle Communications (July 2006)
Schroth, C., Eigner, R., Eichler, S., Strassberger, M.: A Framework for Network Utility Maximization in VANETs. In: International Conference on Mobile Computing and Networking, USA, September 29. ACM, New York (2006)
Adler, C., Eichler, S., Kosch, T., Schroth, C., Strassberger, M.: Self-organized and Context-Adaptive Information Diffusion in Vehicular Ad Hoc Networks. In: 3rd International Symposium on Wireless Communication Systems, ISWCS 2006 (2006)
NetworkSimulator, ns2, http://www.isi.edu/nsnam/ns
Baumann, R., Legendre, F., Sommer, P.: Generic Mobility Simulation Framework (GMSF). In: MobilityModels 2008, Hong Kong SAR, China, May 26. ACM, New York (2008)
Author information
Authors and Affiliations
Editor information
Editors and Affiliations
Rights and permissions
Copyright information
© 2009 Springer-Verlag Berlin Heidelberg
About this paper
Cite this paper
Rahim, A., Muyaha, F.b. (2009). Impact of Malicious Node on Broadcast Schemes. In: Ślęzak, D., Kim, Th., Fang, WC., Arnett, K.P. (eds) Security Technology. SecTech 2009. Communications in Computer and Information Science, vol 58. Springer, Berlin, Heidelberg. https://doi.org/10.1007/978-3-642-10847-1_11
Download citation
DOI: https://doi.org/10.1007/978-3-642-10847-1_11
Publisher Name: Springer, Berlin, Heidelberg
Print ISBN: 978-3-642-10846-4
Online ISBN: 978-3-642-10847-1
eBook Packages: Computer ScienceComputer Science (R0)