Abstract
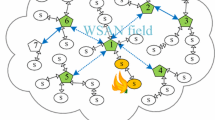
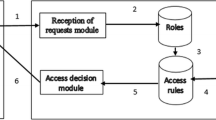
The widespread proliferation of wireless networks (WLAN) demands formal evaluation and analysis of security policy management in enterprise networks. The enforcement of organizational security policies in wireless local area networks (WLANs) requires protection over the network resources from unauthorized access. Hence it is required to ensure correct distribution of access control rules to the network access points conforming to the security policy. In WLAN security policy management, the role-based access control (RBAC) mechanisms can be deployed to strengthen the security perimeter over the network resources. Further, there is a need to model the time and location dependent access constraints. In this paper, we propose WLAN security management system supported by a spatio-temporal RBAC (STRBAC) model and a SAT based verification framework. The system stems from logical partitioning of the WLAN topology into various security policy zones. It includes a Global Policy Server (GPS) that formalizes the organizational access policies and determines the high level policy configurations; a Central Authentication & Role Server (CARS) which authenticates the users and the access points (AP) in various zones and also assigns appropriate roles to the users. Each policy zone consists of an Wireless Policy Zone Controller (WPZCon) that co-ordinates with a dedicated Local Role Server (LRS) to extract the low level access configurations corresponding to the zone access router. We also propose a formal spatio-temporal RBAC (STRBAC) model to represent the global security policies formally and a SAT based verification framework to verify the access configurations.
Access this chapter
Tax calculation will be finalised at checkout
Purchases are for personal use only
Preview
Unable to display preview. Download preview PDF.
Similar content being viewed by others
References
Basile, C., Lioy, A., Prez, G.M., Clemente, F.J.G., Skarmeta, A.F.G.: POSITIF: a policy-based security management system. In: 8th IEEE International Workshop on Policies for Distributed Systems and Networks (POLICY 2007), Bologna, Italy, p. 280 (June 2007)
Lapiotis, G., Kim, B., Das, S., Anjum, F.: A Policy-based Approach to Wireless LAN Security Management. In: International Workshop on Security and Privacy for Emerging Areas in Communication Networks, Athens, Greece, pp. 181–189 (September 2005)
Burns, J., Cheng, A., Gurung, P., Rajagopalan, S., Rao, P., Rosenbluth, D., Martin, D.: Automatic Mnagement of Network Security Policy. In: Proceedings of the 2nd DARPA Information Survivability Conference and Exposition (DISCEX II), Anaheim, California, pp. 12–26 (June 2001)
Yavatkar, R., Pendarakis, D., Guerin, R.: RFC 2753: A Framework for Policy-based Admission Control. Internet Society, 1–20 (January 2000)
Westrinen, A., Schnizlein, J., Strassner, J., Scherling, M., Quinn, B., Herzog, S., Carlson, M., Perry, J., Wldbusser, S.: RFC 3198: Terminology for Policy-Based Management. Internet Society, 1–21 (November 2001)
Ferraiolo, D.F., Sandhu, R., Gavrila, S., Kuhn, D.R., Chandramouli, R.: Proposed NIST standard for Role-Based Access Control. ACM Trnsactions on Information and Systems Security 4(3) (August 2001)
Joshi, J.B.D., Bertino, E., Latif, U., Ghafoor, A.: A Generalized Temporal Role-Based Access Control Model. IEEE Transactions on Knowledge and Data Engineering 17(1), 4–23 (2005)
Ray, I., Toahchoodee, M.: A Spatio-Temporal Role-Based Access Control Model. In: Barker, S., Ahn, G.-J. (eds.) Data and Applications Security 2007. LNCS, vol. 4602, pp. 211–226. Springer, Heidelberg (2007)
Tomur, E., Erten, Y.M.: Application of Temporal and Spatial role based access control in 802.11 wireless networks. The Journal of Computers & Security 25(6), 452–458 (2006)
Laborde, R., Nasser, B., Grasset, F., Barrere, F., Benzekri, A.: A Formal Approach for the Evaluation of Network Security Mechanisms Based on RBAC policies. Electronic Notes in Theoritical Computer Science 121, 117–142 (2005)
Hofmeister, T., Schoning, U., Schuler, R., Watanabe, O.: A Probabilistic 3-SAT Algorithm further improved. In: Alt, H., Ferreira, A. (eds.) STACS 2002. LNCS, vol. 2285, pp. 192–202. Springer, Heidelberg (2002)
Mahajan, Y., Fu, Z., Malik, S.: Zchaff 2004: An efficient SAT solver. In: Hoos, H.H., Mitchell, D.G. (eds.) SAT 2004. LNCS, vol. 3542, pp. 360–375. Springer, Heidelberg (2005)
Dubois, O., Andre, P., Boufkhad, Y., Carlier, J.: SAT versus UNSAT, Second DIMACS challenge. In: Johnson, D.S., Trick, M.A. (eds.) (1993)
Bhagyavati, Summers, W.C., Dejoie, A.: Wireless security techniques: an overview. In: Proceedings of 1st International Conference on Information Security Curriculum Development (InfoSecCD 2004), Georgia, pp. 82–87. ACM Press, New York (2004)
Bera, P., Dasgupta, P., Ghosh, S.K.: A Spatio-temporal Role-based Access Control Model for Wireless LAN Security Policy Management. In: Proceedings of 4th ih International Conference on Information Systems, Technology and Management (ICISTM 2010), Thiland, pp. 76–88. Springer, Heidelberg (2010)
Author information
Authors and Affiliations
Editor information
Editors and Affiliations
Rights and permissions
Copyright information
© 2010 Springer-Verlag Berlin Heidelberg
About this paper
Cite this paper
Bera, P., Maity, S., Ghosh, S.K., Dasgupta, P. (2010). A SAT Based Verification Framework for Wireless LAN Security Policy Management Supported by STRBAC Model. In: Meghanathan, N., Boumerdassi, S., Chaki, N., Nagamalai, D. (eds) Recent Trends in Network Security and Applications. CNSA 2010. Communications in Computer and Information Science, vol 89. Springer, Berlin, Heidelberg. https://doi.org/10.1007/978-3-642-14478-3_24
Download citation
DOI: https://doi.org/10.1007/978-3-642-14478-3_24
Publisher Name: Springer, Berlin, Heidelberg
Print ISBN: 978-3-642-14477-6
Online ISBN: 978-3-642-14478-3
eBook Packages: Computer ScienceComputer Science (R0)