Abstract
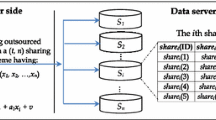
Database as a Service(DaaS) is a paradigm for data management in which the Database Service Provider(DSP), usually a professional third party for data management, can host the database as a service. Many security and query problems are brought about because of the possible untrusted or malicious DSP in this context. Most of the proposed papers are concentrated on using symmetric encryption to guarantee the confidentiality of the delegated data, and using partition based index to help execute the privacy preserving range query. However, encryption and decryption operations on large volume of data are time consuming, and query results always consist of many irrelevant data tuples. Different from encryption based scheme, in this paper, we present a secret share based scheme to guarantee the confidentiality of delegated data. And what is more important, we construct a privacy preserving index to accelerate query and to help return the exactly required data tuples. Finally we analyze the security properties and demonstrate the efficiency and query response time of our approach through empirical data.
Access this chapter
Tax calculation will be finalised at checkout
Purchases are for personal use only
Preview
Unable to display preview. Download preview PDF.
Similar content being viewed by others
References
Shamir, A.: How to share a secret. Communications of the ACM 22(11), 612–613 (1979)
Hacigumus, H., Iyer, B., Mehrotra, S.: Providing database as a service. In: Proc. of the 18th ICDE Conf., pp. 29–38 (2002)
Hacigumus, H., Iyer, B., Mehrotra, S., Li, C.: Executing SQL over encrypted data in the database-service-provider model. In: Proc. of the ACM SIGMOD Conf., pp. 216–227 (2002)
Emekci, F., Agrawal, D., Abbadi, A.E.: Abacus: A distributed middleware for privacy preserving data sharing across private data warehouses. In: Alonso, G. (ed.) Middleware 2005. LNCS, vol. 3790, pp. 21–41. Springer, Heidelberg (2005)
Emekci, F., Agrawal, D., Abbadi, A.E., Gulbeden, A.: Privacy preserving query processing using third parties. In: Proc. of 22th ICDE Conf. (2006)
Agrawal, D., Abbadi, A.E., Emekci, F., Metwally, A.: Datamanagement as a service:challenges and opportunities. Keynotes. In: Proc. of the 25th ICDE Conf. (2009)
Aggarwal, G., Bawa, M., Ganesan, P., Garcia-Molina, H., Kenthapadi, K., Motwani, R., Srivastava, U., Thomas, D., Xu, Y.: Two can keep a secret: A distributed architecture for secure database services. In: Proc. of CIDR Conf., Asilomar, CA, pp. 186–199 (2005)
Agrawal, R., Kiernan, J., Srikant, R., Xu, Y.: Order preserving encryption for numeric data. In: Proc. of the ACM SIGMOD Conf., pp. 563–574 (2004)
Hore, B., Mehrotra, S., Tsudik, G.: A privacy-preserving index for range queries. In: Proc. of the 30th VLDB Conf., Toronto, Canada, pp. 720–731 (2004)
Li, J., Omiecinski, R.: Efficiency, security trade-off in supporting range queries on encrypted databases. In: Jajodia, S., Wijesekera, D. (eds.) Data and Applications Security 2005. LNCS, vol. 3654, pp. 69–83. Springer, Heidelberg (2005)
Shmueli, E., Waisenberg, R., Elovici, Y., Gudes, E.: Designing secure indexes for encrypted databases. In: Proc. of the IFIP Conf. on Database and Application Security (2005)
Anciaux, N., Benzine, M., Bouganim, L., Pucheral, P., Shasha, D.: Ghostdb:querying visible and hidden data without leaks. In: Proc. of the ACM SIGMOD Conf., pp. 677–688 (2007)
Schneier, B.: Applied Cryptography. John Wiley Sons, Chichester (1996)
Mattsson, U.: Database encryption-how to balance security with performance. Protegrity Corp. (2005)
Author information
Authors and Affiliations
Editor information
Editors and Affiliations
Rights and permissions
Copyright information
© 2011 Springer-Verlag Berlin Heidelberg
About this paper
Cite this paper
Tian, X., Sha, C., Wang, X., Zhou, A. (2011). Privacy Preserving Query Processing on Secret Share Based Data Storage. In: Yu, J.X., Kim, M.H., Unland, R. (eds) Database Systems for Advanced Applications. DASFAA 2011. Lecture Notes in Computer Science, vol 6587. Springer, Berlin, Heidelberg. https://doi.org/10.1007/978-3-642-20149-3_10
Download citation
DOI: https://doi.org/10.1007/978-3-642-20149-3_10
Publisher Name: Springer, Berlin, Heidelberg
Print ISBN: 978-3-642-20148-6
Online ISBN: 978-3-642-20149-3
eBook Packages: Computer ScienceComputer Science (R0)