Abstract
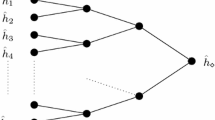
We introduce a statistical experiment setting to carry out a multicollision attack on any iterated hash function. We develop a method for finding multicollisions that gives larger multicollision sets for the same amount of work as Joux’s famous method i.e. with \(2.5\cdot k2^{\frac{n}{2}}\) work one can find greater than 2k-collisions for large k. Furthermore, if the message length is not restricted, we show that we can create arbitrarily large multicollisions by finding two cycles in the iterated hash function. This applies even when an ideal compression function is used.
Access this chapter
Tax calculation will be finalised at checkout
Purchases are for personal use only
Preview
Unable to display preview. Download preview PDF.
Similar content being viewed by others
References
Merkle, R.C.: One way hash functions and DES. In: Brassard, G. (ed.) CRYPTO 1989. LNCS, vol. 435, pp. 428–446. Springer, Heidelberg (1990)
Damgård, I.B.: A design principle for hash functions. In: Brassard, G. (ed.) CRYPTO 1989. LNCS, vol. 435, pp. 416–427. Springer, Heidelberg (1990)
Joux, A.: Multicollisions in iterated hash functions. application to cascaded constructions. In: Franklin, M. (ed.) CRYPTO 2004. LNCS, vol. 3152, pp. 306–316. Springer, Heidelberg (2004)
Suzuki, K., Tonien, D., Kurosawa, K., Toyota, K.: Birthday paradox for multi-collisions. IEICE Transactions 91-A(1), 39–45 (2008)
Kelsey, J., Schneier, B.: Second preimages on n-bit hash functions for much less than 2n work. In: Cramer, R. (ed.) EUROCRYPT 2005. LNCS, vol. 3494, pp. 474–490. Springer, Heidelberg (2005)
Aumasson, J.-P.: Faster multicollisions. In: Chowdhury, D.R., Rijmen, V., Das, A. (eds.) INDOCRYPT 2008. LNCS, vol. 5365, pp. 67–77. Springer, Heidelberg (2008)
Nandi, M., Stinson, D.R.: Multicollision attacks on some generalized sequential hash functions. IEEE Transactions on Information Theory 53(2), 759–767 (2007)
Hoch, J.J., Shamir, A.: Breaking the ICE - finding multicollisions in iterated concatenated and expanded (ICE) hash functions. In: Robshaw, M.J.B. (ed.) FSE 2006. LNCS, vol. 4047, pp. 179–194. Springer, Heidelberg (2006)
Kelsey, J., Kohno, T.: Herding Hash Functions and the Nostradamus Attack. In: Vaudenay, S. (ed.) EUROCRYPT 2006. LNCS, vol. 4004, pp. 183–200. Springer, Heidelberg (2006)
Andreeva, E., Bouillaguet, C., Fouque, P.-A., Hoch, J.J., Kelsey, J., Shamir, A., Zimmer, S.: Second preimage attacks on dithered hash functions. In: Smart, N.P. (ed.) EUROCRYPT 2008. LNCS, vol. 4965, pp. 270–288. Springer, Heidelberg (2008)
Sedgewick, R., Szymanski, T.G., Yao, A.C.: The complexity of finding cycles in periodic functions. SICOMP: SIAM Journal on Computing 11, 376–390 (1982)
Quisquater, J.-J., Delescaille, J.-P.: How easy is collision search. New results and applications to DES. In: Brassard, G. (ed.) CRYPTO 1989. LNCS, vol. 435, pp. 408–413. Springer, Heidelberg (1990)
Menezes, A.J., van Oorschot, P.C., Vanstone, S.A. (eds.): Handbook of Applied Cryptography. CRC Press, Boca Raton (1996)
Author information
Authors and Affiliations
Editor information
Editors and Affiliations
Rights and permissions
Copyright information
© 2011 Springer-Verlag Berlin Heidelberg
About this paper
Cite this paper
Kortelainen, T., Kortelainen, J., Halunen, K. (2011). Variants of Multicollision Attacks on Iterated Hash Functions. In: Lai, X., Yung, M., Lin, D. (eds) Information Security and Cryptology. Inscrypt 2010. Lecture Notes in Computer Science, vol 6584. Springer, Berlin, Heidelberg. https://doi.org/10.1007/978-3-642-21518-6_11
Download citation
DOI: https://doi.org/10.1007/978-3-642-21518-6_11
Publisher Name: Springer, Berlin, Heidelberg
Print ISBN: 978-3-642-21517-9
Online ISBN: 978-3-642-21518-6
eBook Packages: Computer ScienceComputer Science (R0)