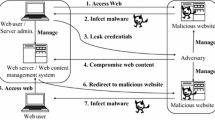
Abstract
High-interaction honeyclients are the tools of choice to detect malicious web pages that launch drive-by-download attacks. Unfortunately, the approach used by these tools, which, in most cases, is to identify the side-effects of a successful attack rather than the attack itself, leaves open the possibility for malicious pages to perform evasion techniques that allow one to execute an attack without detection or to behave in a benign way when being analyzed. In this paper, we examine the security model that high-interaction honeyclients use and evaluate their weaknesses in practice. We introduce and discuss a number of possible attacks, and we test them against several popular, well-known high-interaction honeyclients. Our attacks evade the detection of these tools, while successfully attacking regular visitors of malicious web pages.
The title is a pun that uses the name of a famous LucasArts computer adventure game to describe the purpose of our attacks, which is to evade high-interaction honeyclients such as HoneyMonkey [46].
Access this chapter
Tax calculation will be finalised at checkout
Purchases are for personal use only
Preview
Unable to display preview. Download preview PDF.
Similar content being viewed by others
References
Anubis: Analyzing Unknown Binaries, http://anubis.seclab.tuwien.ac.at
Bayer, U., Kruegel, C., Kirda, E.: TTAnalyze: A Tool for Analyzing Malware. In: Proceedings of the European Institute for Computer Antivirus Research Annual Conference, EICAR (2006)
Boscovich, R. et al.: Microsoft Security Intelligence Report. Technical Report, vol. 7, Microsoft, Inc. (2009)
Broersma, M.: Web attacks slip under the radar (2007), http://news.techworld.com/security/10620/web-attacks-slip-under-the-radar/
Cova, M., Kruegel, C., Vigna, G.: Detection and Analysis of Drive-by-Download Attacks and Malicious JavaScript Code. In: Proceedings of the International World Wide Web Conference, WWW (2010)
CVE. Windows ANI LoadAniIcon() Chunk Size Stack Overflow (HTTP), http://cve.mitre.org/cgi-bin/cvename.cgi?name=2007-0038 .
CWSandbox (2009), http://www.cwsandbox.org/
Dinaburg, A., Royal, P., Sharif, M., Lee, W.: Ether: Malware analysis via hardware virtualization extensions. In: Proceedings of the ACM Conference on Computer and Communications Security, CCS (2008)
Ferrie, P.: Attacks on Virtual Machines. In: Proceedings of the Association of Anti-Virus Asia Researchers Conference (2007)
Fewer, S.: Reflective DLL injection, http://www.harmonysecurity.com/files/HS-P005_ReflectiveDllInjection.pdf
Fogla, P., Lee, W.: Evading Network Anomaly Detection Systems: Formal Reasoning and Practical Techniques. In: Proceedings of the ACM Conference on Computer and Communications Security CCS (2006)
Frei, S., Dübendorfer, T., Ollman, G., May, M.: Understanding the Web browser threat: Examination of vulnerable online Web browser populations and the insecurity iceberg. In: Proceedings of DefCon, vol. 16 (2008)
Garfinkel, T., Adams, K., Warfield, A., Franklin, J.: Compatibility is Not Transparency: VMM Detection Myths and Realities. In: Proceedings of the USENIX Workshop on Hot Topics in Operating Systems (2007)
Google. Safe Browsing API, http://code.google.com/apis/safebrowsing/
Holz, T.: AV Tracker (2009), http://honeyblog.org/archives/37-AV-Tracker.html
Jaeger, T.: Reference Monitor Concept. Encyclopedia of Cryptography and Security (2010)
Jiang, X., Wang, X., Xu, D.: Stealthy Malware Detection and Monitoring through VMM-Based Out-of-the-Box Semantic View Reconstruction. ACM Transactions on Information and System Security (TISSEC) 13(2) (February 2010)
Joebox: A Secure Sandbox Application for Windows (2009), http://www.joebox.org/
Klein, T.: ScoopyNG - The VMware detection tool, http://www.trapkit.de/research/vmm/scoopyng/index.html
Krebs, B.: Former anti-virus researcher turns tables on industry (October 27, 2009), http://voices.washingtonpost.com/securityfix/2009/10/former_anti-virus_researcher_t.html
Liston, T., Skoudis, E.: On the Cutting Edge: Thwarting Virtual Machine Detection (2006), http://handlers.sans.org/tliston/ThwartingVMDetection_Liston_Skoudis.pdf
Martignoni, L., Paleari, R., Roglia, G.F., Bruschi, D.: Testing CPU Emulators. In: Proceedings of the International Symposium on Software Testing and Analysis, ISSTA (2009)
Microsoft. What is SmartScreen Filter?, http://www.microsoft.com/security/filters/smartscreen.aspx
MITRE. HoneyClient, http://www.honeyclient.org/
Moshchuk, A., Bragin, T., Deville, D., Gribble, S., Levy, H.: SpyProxy: Execution-based Detection of Malicious Web Content. In: Proceedings of the USENIX Security Symposium (2007)
Moshchuk, A., Bragin, T., Gribble, S., Levy, H.: A Crawler-based Study of Spyware in the Web. In: Proceedings of the Symposium on Network and Distributed System Security, NDSS (2006)
Müller, T., Mack, B., Arziman, M.: Web Exploit Finder, http://www.xnos.org/security/web-exploit-finder.html
Nguyen, A., Schear, N., Jung, H., Godiyal, A., King, S., Nguyen, H.: MAVMM: Lightweight and Purpose Built VMM for Malware Analysis. In: Proceedings of the Annual Computer Security Applications Conference, ACSAC (2009)
Norman Sandbox (2009), http://www.norman.com/about_norman/technology/norman_sandbox/
Paleari, R., Martignoni, L., Roglia, G.F., Bruschi, D.: A Fistful of Red-Pills: How to Automatically Generate Procedures to Detect CPU Emulators. In: Proceedings of the USENIX Workshop on Offensive Technologies, WOOT (2009)
Polychronakis, M., Mavrommatis, P., Provos, N.: Ghost Turns Zombie: Exploring the Life Cycle of Web-based Malware. In: Proceedings of the USENIX Workshop on Large-Scale Exploits and Emergent Threats, LEET (2008)
Provos, N., Mavrommatis, P., Rajab, M., Monrose, F.: All Your iFRAMEs Point to Us. In: Proceedings of the USENIX Security Symposium (2008)
Provos, N., McNamee, D., Mavrommatis, P., Wang, K., Modadugu, N.: The Ghost in the Browser: Analysis of Web-based Malware. In: Proceedings of the USENIX Workshop on Hot Topics in Understanding Botnet (2007)
Ptacek, T., Newsham, T.: Insertion, Evasion, and Denial of Service: Eluding Network Intrusion Detection. Technical report, Secure Networks, Inc. (1998)
Quist, D., Smith, V., Computing, O.: Detecting the Presence of Virtual Machines Using the Local Data Table, http://www.offensivecomputing.net/files/active/0/vm.pdf
Raffetseder, T., Kruegel, C., Kirda, E.: Detecting System Emulators. In: Proceedings of the Information Security Conference (2007)
Rocaspana, J.: SHELIA: A Client HoneyPot For Client-Side Attack Detection (2009), http://www.cs.vu.nl/~herbertb/misc/shelia/
Rutkowska, J.: Red Pill. or how to detect VMM using (almost) one CPU instruction (2004), http://www.invisiblethings.org/papers/redpill.html
Sharif, M., Lee, W., Cui, W., Lanzi, A.: Secure In-VM Monitoring Using Hardware Virtualization. In: Proceedings of the ACM Conference on Computer and Communications Security, CCS (2009)
The Honeynet Project. Capture-HPC, https://projects.honeynet.org/capture-hpc
ThreatExpert (2009), http://www.threatexpert.com/
Tsaur, W., Chen, Y., Tsai, B.: A New Windows Driver-Hidden Rootkit Based on Direct Kernel Object Manipulation. In: Proceedings of the Algorithms and Architectures for Parallel Processing Conference (2009)
Van Gundy, M., Chen, H., Su, Z., Vigna, G.: Feature Omission Vulnerabilities: Thwarting Signature Generation for Polymorphic Worms. In: Proceedings of the Annual Computer Security Applications Conference, ACSAC (2007)
Vasudevan, A., Yerraballi, R.: Cobra: Fine-grained Malware Analysis using Stealth Localized Executions. In: Proceedings of the IEEE Symposium on Security and Privacy (2006)
Vigna, G., Robertson, W., Balzarotti, D.: Testing Network-based Intrusion Detection Signatures Using Mutant Exploits. In: Proceedings of the ACM Conference on Computer and Communications Security CCS (2004)
Wang, Y.-M., Beck, D., Jiang, X., Roussev, R., Verbowski, C., Chen, S., King, S.: Automated Web Patrol with Strider HoneyMonkeys: Finding Web Sites That Exploit Browser Vulnerabilities. In: Proceedings of the Symposium on Network and Distributed System Security, NDSS (2006)
Yin, H., Poosankam, P., Hanna, S., Song, D.: HookScout: Proactive Binary-Centric Hook Detection. In: Proceedings of the Conference on Detection of Intrusions and Malware & Vulnerability Assessment, DIMVA (2010)
Author information
Authors and Affiliations
Editor information
Editors and Affiliations
Rights and permissions
Copyright information
© 2011 Springer-Verlag Berlin Heidelberg
About this paper
Cite this paper
Kapravelos, A., Cova, M., Kruegel, C., Vigna, G. (2011). Escape from Monkey Island: Evading High-Interaction Honeyclients. In: Holz, T., Bos, H. (eds) Detection of Intrusions and Malware, and Vulnerability Assessment. DIMVA 2011. Lecture Notes in Computer Science, vol 6739. Springer, Berlin, Heidelberg. https://doi.org/10.1007/978-3-642-22424-9_8
Download citation
DOI: https://doi.org/10.1007/978-3-642-22424-9_8
Publisher Name: Springer, Berlin, Heidelberg
Print ISBN: 978-3-642-22423-2
Online ISBN: 978-3-642-22424-9
eBook Packages: Computer ScienceComputer Science (R0)