Abstract
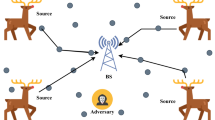
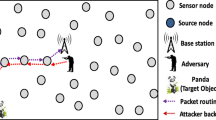
In wireless sensor networks (WSNs), sinks or base stations are the key nodes of the networks which receive and process data from sensor nodes, hence their location should be protected well. However, they can easy fall prey to attacks launched by adversaries. In this paper, we propose a novel countermeasure Maelstrom to protect the location privacy of the key nodes in WSNs from both traffic analysis and packet tracing attacks. The basic idea of Maelstrom is to pre-assign several maelstrom areas in a network, which serve as the destinations of fake packets generated by sensor nodes. We also propose an Approximate Shortest Routing protocol (ASR) for packet delivery. Combining ASR with maelstroms congregated by fake packets, an adversary who launches both traffic analysis and packet tracing attack will be thwarted. The simulation results show that, compared with LPR combined with fake packet injection, under similar energy cost, Maelstrom can remarkably enhance the security of receiver-location in WSNs.
Access this chapter
Tax calculation will be finalised at checkout
Purchases are for personal use only
Preview
Unable to display preview. Download preview PDF.
Similar content being viewed by others
References
Akyildiz, I.F., Su, W., Sankarasubramaniam, Y., Cayirci, E.: Wireless sensor networks: a survey. Computer Networks 38, 393–422 (2002)
Deng, J., Han, R., Mishra, S.: Countermeasures against traffic analysis attacks in wireless sensor networks. In: Proceeding of SecureComm 2005, Athens, Greece (September 2005)
Kamat, P., Zhang, Y., Trappe, W., Ozturk, C.: Enhancing source-location privacy in sensor network routing. In: Proceeding of ICDCS 2005, Columbus, USA (June 2005)
Zhang, L.: A self-adjusting directed random walk approach for enhancing source-location privacy in sensor network routing. In: Proceeding of IWCMC 2006, New York, USA (July 2006)
Jian, Y., Chen, S., Zhang, Z., Zhang, L.: A novel scheme for protecting receiver’s location privacy in wireless sensor networks. IEEE Trans. on Wireless Communications 7(10) (October 2008)
Ouyang, Y., Le, Z., Chen, G., Ford, J., Makedon, F.: Entrapping adversaries for source protection in sensor networks. In: Proceeding of WoWMoM 2006, Niagara, Canada (June 2006)
Mehta, K., Liu, D.: Location privacy in sensor networks against a global eavesdropper. In: Proceeding of ICNP 2007, Beijing, China (October 2007)
Fan, Y., Jiang, Y., Zhu, H., Chen, J., Shen, X.: Network coding based privacy preservation against traffic analysis in multi-hop wireless networks. IEEE Trans. on Wireless Communications 10(3) (December 2010)
Zhu, Y., Bettati, R.: Compromising location privacy in wireless networks using sensors with limited information. In: Proceeding of ICDCS 2007, Toronto, Canada (June 2007)
Xi, Y., Schwiebert, L., Shim, W.: Preserving source location privacy in monitoring-based wireless sensor networks. In: Proceeding of IPDPS 2006, Rhodes Island, Greece (April 2006)
Cheng, R., Yau, D.Y., Fu, J.: Packet cloaking: protecting receiver privacy against traffic analysis. In: Proceeding of NPSec 2007, Beijing, China (October 2007)
Ozturk, C., Zhang, Y., Trappe, W., Ott, M.: Source-location privacy for networks of energy-constrained sensors. In: Proceeding of WSTFEUS 2004, Vienna, Austria (May 2004)
Hoh, B., Gruteser, M.: Protecting location privacy through path confusion. In: Proceeding of SecureComm 2005, Athens, Greece (September 2005)
Ouyang, Y., Le, Z., Ford, J., Makedon, F.: PrivaSense: providing privacy protection for sensor networks. In: Proceeding of SenSys 2007, Sydney, Australia (November 2007)
Li, X., Wang, X., Zheng, N., Wan, Z., Gu, M.: Enhanced location pricacy protection of base station in wireless sensor networks. In: Proceeding of MSN 2009, Wu Yi Mountain, China (December 2009)
Chow, C., Mokbel, M., He, T.: A privacy-preserving location monitoring system for wireless sensor networks. IEEE Trans. on Mobile Computing 10(1) (January 2011)
Yang, Y., Zhu, S., Cao, G., LaPorta, T.: An active global attack model for sensor source Location Privacy: Analysis and Countermeasures. In: Proceeding of SecureComme 2009, Athens, Greece (September 2009)
Shao, M., Hu, W., Zhu, S., Cao, G., Krishnamurthy, S., LaPorta, T.: Cross-layer enhanced source location privacy in sensor networks. In: Proceeding of SECON 2009, Rome, Italy (June 2009)
Author information
Authors and Affiliations
Editor information
Editors and Affiliations
Rights and permissions
Copyright information
© 2011 Springer-Verlag Berlin Heidelberg
About this paper
Cite this paper
Chang, S., Qi, Y., Zhu, H., Dong, M., Ota, K. (2011). Maelstrom: Receiver-Location Preserving in Wireless Sensor Networks. In: Cheng, Y., Eun, D.Y., Qin, Z., Song, M., Xing, K. (eds) Wireless Algorithms, Systems, and Applications. WASA 2011. Lecture Notes in Computer Science, vol 6843. Springer, Berlin, Heidelberg. https://doi.org/10.1007/978-3-642-23490-3_17
Download citation
DOI: https://doi.org/10.1007/978-3-642-23490-3_17
Publisher Name: Springer, Berlin, Heidelberg
Print ISBN: 978-3-642-23489-7
Online ISBN: 978-3-642-23490-3
eBook Packages: Computer ScienceComputer Science (R0)