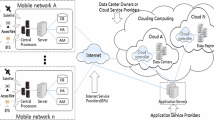
Abstract
Access control is a key issue in the deployment of systems within corporations. To comply with legal and business requirements and to prevent unauthorized access, the identification and authentication of all users is required. This is typically achieved by using an access control system that performs the identification & authentication of each user at the point of entry into the system. However, as the systems evolve and thus become more complex it is difficult to ensure reliable access control, especially if they are accessed via mobile devices. This paper focuses on improving the existing access control approach for service-oriented systems by applying the concept of device comfort to service providers. Similar to the concept of device comfort, service providers are empowered to decide if they feel comfortable with requests sent to them. This paper presents and evaluates the idea of integrating trust evaluations into service-oriented systems by requiring each service provider to evaluate the trustworthiness of requests and to share their evaluations as part of the call-context within the call-stack.
Access this chapter
Tax calculation will be finalised at checkout
Purchases are for personal use only
Preview
Unable to display preview. Download preview PDF.
Similar content being viewed by others
References
Portio Research: “Portio Research Mobile Factbook 2009”, 37 pages (2009)
Yates, S.: Forester: Worldwide PC Adoption Forecast, 2007 To 2015, It’s Time To Focus On Emerging Markets For Future Growth, 21 pages (June 11, 2007)
Milanesi, C., et al.: ”Gartner: Competitive Landscape: Mobile Devices, Worldwide, 2009”, 11 pages (August 11, 2009)
Beccue, M.: ABI-Research Report RR-MCC: “Mobile Cloud Computing”, 64 pages (2009)
Schulte, R., Natis, Y.: Service Oriented Architecture, Gartner (April 12, 1996)
Four Tenets of Service Orientation, http://msdn.microsoft.com/msdnmag/issues/04/01/Indigo/default.aspx
Chatarji, J.: Introduction to Service Oriented Architecture, SOA, 5 pages (2004), http://www.devshed.com/c/a/Web-Services/Introduction-to-Service-Oriented-Architecture-SOA
Marsh, S., Briggs, P.: Defining and investigating Device comfort. In: IFIPTM 2010, pp. 17–24 (2010)
Wang, Y., Vassileva, J.: Toward Trust and Reputation Based Web Service Selection: A Survey. International Transactions on Systems Science and Applications 3(2), 118–132 (2007); (invited paper in the special Issue on New tendencies on Web Services and Multi-agent Systems (WS-MAS))
Maximilien, E., Singh, M.: Toward autonomic web services trust and selection. In: ICSOC 2004, pp. 212–221 (2004)
CAS, http://msdn.microsoft.com/en-us/library/c5tk9z76(v=vs.71).aspx
Fielding, R.: Architectural Styles and the Design of Network-based Software Architectures, Dissertation University of Irvine (2000), http://www.ics.uci.edu/~fielding/pubs/dissertation/top.htm
Author information
Authors and Affiliations
Editor information
Editors and Affiliations
Rights and permissions
Copyright information
© 2012 Springer-Verlag Berlin Heidelberg
About this paper
Cite this paper
Luo, M., Deters, R. (2012). Improving Access Control for Mobile Consumers of Services by Use of Context and Trust within the Call-Stack. In: Ardissono, L., Kuflik, T. (eds) Advances in User Modeling. UMAP 2011. Lecture Notes in Computer Science, vol 7138. Springer, Berlin, Heidelberg. https://doi.org/10.1007/978-3-642-28509-7_24
Download citation
DOI: https://doi.org/10.1007/978-3-642-28509-7_24
Publisher Name: Springer, Berlin, Heidelberg
Print ISBN: 978-3-642-28508-0
Online ISBN: 978-3-642-28509-7
eBook Packages: Computer ScienceComputer Science (R0)