Abstract
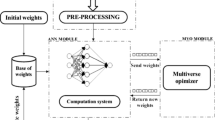
Artificial neural networks based ensembles are used for solving the computer security problems. Ensemble members and the ensembling method are generated automatically with the self-configuring genetic programming algorithm that does not need preliminary adjusting. Performance of the approach is demonstrated with test problems and then applied to two real world problems from the field of computer security – intrusion and spam detection. The proposed approach demonstrates results competitive to known techniques.
Access this chapter
Tax calculation will be finalised at checkout
Purchases are for personal use only
Preview
Unable to display preview. Download preview PDF.
Similar content being viewed by others
References
Maloof, M. (ed.): Machine Learning and Data Mining for Computer Security. Springer (2006)
Victoire, T.A., Sakthivel, M.: A Refined Differential Evolution Algorithm Based Fuzzy Classifier for Intrusion Detection. European Journal of Scientific Research 65(2), 246–259 (2011)
Bloedorn, E.E., Talbot, L.M., DeBarr, D.D.: Data Mining Applied to Intrusion Detection: MITRE Experiences. In: Machine Learning and Data Mining for Computer Security: Methods and Applications. Springer, London (2006)
Julisch, K.: Intrusion Detection Alarm Clustering. In: Machine Learning and Data Mining for Computer Security Methods and Applications. Springer, London (2006)
Patcha, A., Park, J.-M.: An Overview of Anomaly Detection Techniques: Existing Solutions and Latest Technological Trends. Computer Networks (2007)
Özgür, L., Güngör, T., Gürgen, F.: Spam Mail Detection Using Artificial Neural Network and Bayesian Filter. In: Yang, Z.R., Yin, H., Everson, R.M. (eds.) IDEAL 2004. LNCS, vol. 3177, pp. 505–510. Springer, Heidelberg (2004)
Han, C., Li, Y., Yang, D., Hao, Y.: An intrusion detection system based on neural network. In: Proceedings of Mechatronic Science, Electric Engineering and Computer (MEC), pp. 2018–2021 (2011)
Saravanakumar, S., Mohanaprakash, T.A., Dharani, R., Kumar, C.J.: Analysis of ANN-based Echo State Network Intrusion Detection in Computer Networks. International Journal of Computer Science and Telecommunications 3(4), 8–13 (2012)
Panda, M., Abraham, A., Das, S., Patra, M.R.: Network intrusion detection system: A machine learning approach. Intelligent Decision Technologies 5(4), 347–356 (2011)
Pervez, S., Ahmad, I., Akram, A., Swati, S.U.: A Comparative Analysis of Artificial Neural Network Technologies in Intrusion Detection Systems. In: Proceedings of the 6th WSEAS International Conference on Multimedia, Internet & Video Technologies, Lisbon, Portugal, pp. 84–89 (2006)
Dietterich, T.G.: An experimental comparison of three methods for constructing ensembles of decision trees: bagging, boosting, and randomization. Machine Learning 40(2), 139–158 (2000)
Ho, T.K., Hull, J.J., Srihari, S.N.: Decision combination in multiple classifier systems. IEEE Transactions on Pattern Analysis and Machine Intelligence 16(1), 66–75 (1994)
Breiman, L.: Bagging predictors. Machine Learning 24(2), 123–140 (1996)
Friedman, J.H., Hastie, T., Tibshirani, R.: Additive logistic regression: a statistical view of boosting. Annals of Statistics 28(2), 337–374 (2000)
Navone, H.D., Granitto, P.M., Verdes, P.F., Ceccatto, H.A.: A learning algorithm for neural network ensembles. In: Inteligencia Artificial, Revista Iberoamericana de Inteligencia Artificial, vol. 12, pp. 70–74 (2001)
Johansson, U., Lofstrom, T., Konig, R., Niklasson, L.: Building Neural Network Ensembles using Genetic Programming. In: International Joint Conference on Neural Networks (2006)
Poli, R., Langdon, W.B., McPhee, N.F.: A Field Guide to Genetic Programming (2008), http://lulu.com , http://www.gp-field-guide.org.uk
Bukhtoyarov, V., Semenkina, O.: Comprehensive evolutionary approach for neural network ensemble automatic design. In: Proceedings of the IEEE World Congress on Computational Intelligence, pp. 1640–1645 (2010)
Gomez, J.: Self Adaptation of Operator Rates in Evolutionary Algorithms. In: Deb, K., Tari, Z. (eds.) GECCO 2004. LNCS, vol. 3102, pp. 1162–1173. Springer, Heidelberg (2004)
Meyer-Nieberg, S., Beyer, H.-G.: Self-Adaptation in Evolutionary Algorithms. In: Lobo, F., Lima, C., Michalewicz, Z. (eds.) Parameter Setting in Evolutionary Algorithm, pp. 47–75 (2007)
O’Neill, M., Vanneschi, L., Gustafson, S., Banzhaf, W.: Open issues in genetic programming. In: Genetic Programming and Evolvable Machines, vol. 11, pp. 339–363 (2010)
Finck, S., et al.: Real-parameter black-box optimization benchmarking 2009. Presentation of the noiseless functions. Technical Report Researh Center PPE (2009)
Semenkin, E., Semenkina, M.: Self-configuring genetic programming algorithm with modified uniform crossover. In: IEEE Congress on Evolutionary Computation (CEC 2012), Brisbane, Australia (accepted for publication, 2012)
Semenkin, E., Semenkina, M.: Self-configuring Genetic Algorithm with Modified Uniform Crossover Operator. In: Tan, Y., Shi, Y., Ji, Z. (eds.) ICSI 2012, Part I. LNCS, vol. 7331, pp. 414–421. Springer, Heidelberg (2012)
Frank, A., Asuncion, A.: UCI Machine Learning Repository. School of Information and Computer Science. University of California, Irvine (2010), http://archive.ics.uci.edu/ml
Yu, J.J.Q., Lam, A.Y.S., Li, V.O.K.: Evolutionary Artificial Neural Network Based on Chemical Reaction Optimization. In: IEEE Congress on Evolutionary Computation (CEC 2011), New Orleans, LA (2011)
Bukhtoyarov, V., Semenkin, E., Shabalov, A.: Neural Networks Ensembles Approach for Simulation of Solar Arrays Degradation Process. In: Corchado, E., Snášel, V., Abraham, A., Woźniak, M., Graña, M., Cho, S.-B. (eds.) HAIS 2012, Part III. LNCS, vol. 7208, pp. 186–195. Springer, Heidelberg (2012)
Stolfo, S., Fan, W., Lee, W., Prodromidis, A., Chan, P.: Cost-based Modeling for Fraud and Intrusion Detection: Results from the JAM Project. In: Proceedings of the 2000 DARPA Information Survivability Conference and Exposition, DISCEX 2000 (2000)
Malik, A.J., Shahzad, W., Khan, F.A.: Binary PSO and random forests algorithm for PROBE attacks detection in a network. In: IEEE Congress on Evolutionary Computation, pp. 662–668 (2011)
Dimitrakakis, C., Bengio, S.: Online Policy Adaptation for Ensemble Classifiers. IDIAP Research Report 03-69 (2006)
Author information
Authors and Affiliations
Corresponding author
Editor information
Editors and Affiliations
Rights and permissions
Copyright information
© 2013 Springer-Verlag Berlin Heidelberg
About this paper
Cite this paper
Semenkin, E., Semenkina, M., Panfilov, I. (2013). Neural Network Ensembles Design with Self-Configuring Genetic Programming Algorithm for Solving Computer Security Problems. In: Herrero, Á., et al. International Joint Conference CISIS’12-ICEUTE´12-SOCO´12 Special Sessions. Advances in Intelligent Systems and Computing, vol 189. Springer, Berlin, Heidelberg. https://doi.org/10.1007/978-3-642-33018-6_3
Download citation
DOI: https://doi.org/10.1007/978-3-642-33018-6_3
Publisher Name: Springer, Berlin, Heidelberg
Print ISBN: 978-3-642-33017-9
Online ISBN: 978-3-642-33018-6
eBook Packages: EngineeringEngineering (R0)