Abstract
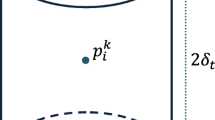
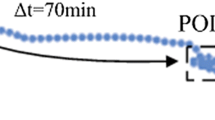
With the growing prevalence of location-aware devices, the amount of trajectories generated by moving objects has been dramatically increased, resulting in various novel data mining applications. Since trajectories may contain sensitive information about their moving objects, so they ought to be anonymized before making them accessible to the public. Many existing approaches for trajectory anonymization consider the same privacy level for all moving objects, whereas different moving objects may have different privacy requirements. In this paper, we propose a novel greedy clustering-based approach for anonymizing trajectory data in which the privacy requirements of moving objects are not necessarily the same. We first assign a privacy level to each trajectory based on the privacy requirement of its moving object. We then partition trajectories into a set of fixed-radius clusters based on the EDR distance. Each cluster is created such that its size is proportional to the maximum privacy level of trajectories within it. We finally anonymize trajectories of each cluster using a novel matching point algorithm. The experimental results show that our approach can achieve a satisfactory trade-off between space distortion and re-identification probability of trajectory data, which is proportional to the privacy requirement of each moving object.
Access this chapter
Tax calculation will be finalised at checkout
Purchases are for personal use only
Preview
Unable to display preview. Download preview PDF.
Similar content being viewed by others
References
Frentzos, E., Gratsias, K., Pelekis, N., Theodoridis, Y.: Nearest Neighbor Search on Moving Object Trajectories. In: Medeiros, C.B., Egenhofer, M., Bertino, E. (eds.) SSTD 2005. LNCS, vol. 3633, pp. 328–345. Springer, Heidelberg (2005)
Lee, J.-G., Han, J., Li, X., Gonzalez, H.: raClass: Trajectory Classification Using Hierarchical Region-based and Trajectory-based Clustering. In: Proc. of the 34th Int. Conf. on Very Large Databases (VLDB 2008), Auckland, New Zealand (2008)
Lee, J.-G., Han, J., Whang, K.-Y.: Trajectory Clustering: a Partition-and-Group Framework. In: Proc. of the ACM SIGMOD Int. Conf. on Management of Data (SIGMOD 2007), Beijing, China, pp. 593–604 (2007)
Li, X., Han, J., Kim, S., Gonzalez, H.: Anomaly Detection in Moving Object. In: Chen, H., Yang, C.C. (eds.) Intelligence and Security Informatics. SCI, vol. 135, pp. 357–381. Springer, Heidelberg (2008)
Pelekis, N., Kopanakis, I., Kotsifakos, E.E., Frentzos, E., Theodoridis, Y.: Clustering Trajectories of Moving Objects in an Uncertain World. In: Proc. of the 9th IEEE Int. Conf. on Data Mining (ICDM 2009), Miami, USA, pp. 417–427 (2009)
Machanavajjhala, A., Kifer, D., Gehrke, J., Venkitasubramaniam, M.: l-diversity: Privacy beyond k-anonymity. ACM Transactions on Knowledge Discovery from Data 1(1) (2007)
Samarati, P.: Protecting Respondents Privacy in Microdata Release. IEEE Transactions on Knowledge and Data Engineering 13(6), 1010–1027 (2001)
Sweeney, L.: k-Anonymity: a Model for Protecting Privacy. International Journal of Uncertainty, Fuzziness Knowledge-Based Systems 10(5), 557–570 (2002)
Chen, L., Özsu, M.T., Oria, V.: Robust and Fast Similarity Search for Moving Object Trajectories. In: Proc. of the 24th ACM SIGMOD Int. Conf. on Management of Data (SIGMOD 2005), Maryland, USA, pp. 491–502 (2005)
Terrovitis, M., Mamoulis, N.: Privacy Preservation in the Publication of Trajectories. In: Proc. of the 9th Int. Conf. on Mobile Data Management (MDM 2008), Beijing, China, pp. 65–72 (2008)
Yarovoy, R., Bonchi, F., Lakshmanan, L.V.S., Wang, W.H.: Anonymizing Moving Objects: How to Hide a MOB in a Crowd? In: Proc. of the 12th Int. Conf. on Extending Database Technology (EDBT 2009), Saint Petersburg, Russia, pp. 72–83 (2009)
Nergiz, E., Atzori, M., Saygin, Y.: Towards Trajectory Anonymization: a Generalization-Based Approach. Transactions on Data Privacy 2(1), 47–75 (2009)
Abul, O., Bonchi, F., Nanni, M.: Anonymization of Moving Objects Databases by Clustering and Perturbation. Information Systems 35(8), 884–910 (2010)
Abul, O., Bonchi, F., Nanni, M.: Never Walk Alone: Uncertainty for Anonymity in Moving Objects Databases. In: Proc. of the 24th IEEE Int. Conf. on Data Engineering (ICDE 2008), Cancun, Mexico, pp. 376–385 (2008)
Monreale, A., Andrienko, G., Andrienko, N., Giannotti, F., Pedreschi, D., Rinzivillo, S., Wrobel, S.: Movement Data Anonymity through Generalization. Transactions on Data Privacy 3(2), 91–121 (2010)
Bonchi, F.: Privacy Preserving Publication of Moving Object Data. In: Bettini, C., Jajodia, S., Samarati, P., Wang, X.S. (eds.) Privacy in Location-Based Applications. LNCS, vol. 5599, pp. 190–215. Springer, Heidelberg (2009)
Brinkhoff, T.: Generating Traffic Data. IEEE Data Engineering Bulletin 26(2), 19–25 (2003)
Author information
Authors and Affiliations
Editor information
Editors and Affiliations
Rights and permissions
Copyright information
© 2012 Springer-Verlag Berlin Heidelberg
About this paper
Cite this paper
Mahdavifar, S., Abadi, M., Kahani, M., Mahdikhani, H. (2012). A Clustering-Based Approach for Personalized Privacy Preserving Publication of Moving Object Trajectory Data. In: Xu, L., Bertino, E., Mu, Y. (eds) Network and System Security. NSS 2012. Lecture Notes in Computer Science, vol 7645. Springer, Berlin, Heidelberg. https://doi.org/10.1007/978-3-642-34601-9_12
Download citation
DOI: https://doi.org/10.1007/978-3-642-34601-9_12
Publisher Name: Springer, Berlin, Heidelberg
Print ISBN: 978-3-642-34600-2
Online ISBN: 978-3-642-34601-9
eBook Packages: Computer ScienceComputer Science (R0)