Abstract
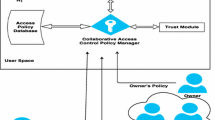
Making friends by sharing personal data has become popular in online social networks (OSNs). Security is a major concern, as an OSN service provider (OSN-SP) is semi-trusted and for-profit, while malicious users might also gather data for improper uses. Encryption of data is a straightforward solution, but interactive sharing of encrypted data becomes a challenging task. In this paper, we propose Masque, a novel access control mechanism employing attribute-based encryption (ABE), as a hierarchical solution for interactive sharing of encrypted data in OSNs. Based on key-policy ABE, it allows the OSN-SP to manage users at a high level but without being able to access their sensitive data. At the same time, based on ciphertext-policy ABE, it enables users to customize their own access policies specifically.
This work was supported by the National Natural Science Foundation of China under Grants 60970138 and 61272479, and also by the Strategic Priority Research Program of Chinese Academy of Sciences under Grant XDA06010702.
Access this chapter
Tax calculation will be finalised at checkout
Purchases are for personal use only
Preview
Unable to display preview. Download preview PDF.
Similar content being viewed by others
References
Boneh, D., Franklin, M.K.: Identity-Based Encryption from the Weil Pairing. In: Kilian, J. (ed.) CRYPTO 2001. LNCS, vol. 2139, pp. 213–229. Springer, Heidelberg (2001)
Boneh, D., Boyen, X.: Efficient Selective-ID Secure Identity-Based Encryption without Random Oracles. In: Cachin, C., Camenisch, J.L. (eds.) EUROCRYPT 2004. LNCS, vol. 3027, pp. 223–238. Springer, Heidelberg (2004)
Sahai, A., Waters, B.: Fuzzy Identity-Based Encryption. In: Cramer, R. (ed.) EUROCRYPT 2005. LNCS, vol. 3494, pp. 457–473. Springer, Heidelberg (2005)
Goyal, V., Pandey, O., Sahai, A., Waters, B.: Attribute-Based Encryption for Fine-Grained Access Control of Encrypted Data. In: 13th ACM Conference on Computer and Communications Security (CCS 2006), pp. 89–98 (October 2006)
Bethencourt, J., Sahai, A., Waters, B.: Ciphertext-Policy Attribute-Based Encryption. In: 28th IEEE Symposium on Security and Privacy (S&P 2007), pp. 321–334 (May 2007)
Pirretti, M., Traynor, P., McDaniel, P., Waters, B.: Secure Attribute-Based Systems. In: 16th ACM Conference on Computer and Communications Security (CCS 2009), pp. 799–873 (November 2009)
Traynor, P., Kevin, B., Enck, W., McDaniel, P.: Realizing Massive-Scale Conditional Access Systems Through Attribute-Based Cryptosystems. In: 13th Network and Distributed System Security Symposium (NDSS 2008), pp. 799–873 (February 2008)
Badenand, R., Benderand, A., Spring, N., Bhattacharjee, B., Starin, D.: Persona: An Online Social Network with User-Defined Privacy. In: ACM Conference on Data Communication (SIGCOMM 2009), pp. 135–146 (August 2009)
Bobba, R., Fatemieh, O., Khan, F., Khanand, A., Gunter, C.A., Khurana, H., Prabhakaran, M.: Attribute-Based Messaging: Access Control and Confidentiality. In: ACM Conference on Data Communication (SIGCOMM 2009), vol. 13 (December 2010)
Yu, S., Wang, C., Ren, K., Lou, W.: Achieving Secure, Scalable, and Fine-Grained Data Access Control in Cloud Computing. In: 29th Conference on Computer Communications (INFOCOM 2010), pp. 14–19 ( March 2010)
Shoup, V.: Lower Bounds for Discrete Logarithms and Related Problems. In: Fumy, W. (ed.) EUROCRYPT 1997. LNCS, vol. 1233, pp. 256–266. Springer, Heidelberg (1997)
Harney, H., Colgrove, A., McDaniel, P.: Principles of Policy in Secure Groups. In: 18th Network and Distributed System Security Symposium (NDSS 2011), pp. 66–74 (August 2011)
Schwartz, J.T.: Fast Probabilistic Algorithms for Verification of Polynomial Identities. Journal of the ACM 27, 701–717 (1980)
Author information
Authors and Affiliations
Editor information
Editors and Affiliations
Rights and permissions
Copyright information
© 2012 Springer-Verlag Berlin Heidelberg
About this paper
Cite this paper
Shuai, H., Zhu, W.T. (2012). Masque: Access Control for Interactive Sharing of Encrypted Data in Social Networks. In: Xu, L., Bertino, E., Mu, Y. (eds) Network and System Security. NSS 2012. Lecture Notes in Computer Science, vol 7645. Springer, Berlin, Heidelberg. https://doi.org/10.1007/978-3-642-34601-9_38
Download citation
DOI: https://doi.org/10.1007/978-3-642-34601-9_38
Publisher Name: Springer, Berlin, Heidelberg
Print ISBN: 978-3-642-34600-2
Online ISBN: 978-3-642-34601-9
eBook Packages: Computer ScienceComputer Science (R0)