Abstract
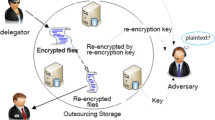
To allow a delegator not only to delegate the keywordcontrolled decryption rights of a broadcast encryption to a set of specified recipients, but also to control when the decryption rights will be delegated, in this paper, for the first time, we introduce a new notion called Timed-Release Conditional Proxy Broadcast Re-Encryption (TRCPBRE). We also propose a concrete construction for TR-CPBRE which can be proven selective identity adaptive CCA secure under the (P,Q, f)- general decisional Diffie-Hellman exponent assumption, and chosen-time period chosen-ciphertext secure under the bilinear Diffie-Hellman assumption. When compared with the existing CPBRE and Timed-Release Proxy Re-Encryption (TR-PRE) schemes, our scheme achieves better efficiency, and enables the delegator to make a fine-grained delegation of decryption rights to multiple delegatees.
Access this chapter
Tax calculation will be finalised at checkout
Purchases are for personal use only
Preview
Unable to display preview. Download preview PDF.
Similar content being viewed by others
References
Ateniese, G., Fu, K., Green, M., Hohenberger, S.: Improved proxy re-encryption schemes with applications to secure distributed storage. ACM Trans. Inf. Syst. Secur. 9(1), 1–30 (2006)
Attrapadung, N., Furukawa, J., Imai, H.: Forward-secure and searchable broadcast encryption with short ciphertexts and private keys. In: Lai, X., Chen, K. (eds.) ASIACRYPT 2006. LNCS, vol. 4284, pp. 161–177. Springer, Heidelberg (2006)
Blaze, M., Bleumer, G., Strauss, M.: Divertible protocols and atomic proxy cryptography. In: Nyberg, K. (ed.) EUROCRYPT 1998. LNCS, vol. 1403, pp. 127–144. Springer, Heidelberg (1998)
Boneh, D., Canetti, R., Halevi, S., Katz, J.: Chosen-ciphertext security from identity-based encryption. SIAM J. Comput. 36(5), 1301–1328 (2007)
Boneh, D., Franklin, M.K.: Identity-based encryption from the weil pairing. SIAM J. Comput. 32(3), 586–615 (2003)
Boneh, D., Gentry, C., Waters, B.: Collusion resistant broadcast encryption with short ciphertexts and private keys. In: Shoup, V. (ed.) CRYPTO 2005. LNCS, vol. 3621, pp. 258–275. Springer, Heidelberg (2005), http://dx.doi.org/10.1007/11535218_16
Boneh, D., Waters, B.: A fully collusion resistant broadcast, trace, and revoke system. In: Proceedings of the 13th ACM Conference on Computer and Communications Security, CCS 2006, pp. 211–220. ACM, New York (2006), http://doi.acm.org/10.1145/1180405.1180432
Canetti, R., Hohenberger, S.: Chosen-ciphertext secure proxy re-encryption. In: Proceedings of the 14th ACM Conference on Computer and Communications Security, CCS 2007, pp. 185–194. ACM, New York (2007), http://doi.acm.org/10.1145/1315245.1315269
Canetti, R., Krawczyk, H., Nielsen, J.B.: Relaxing chosen-ciphertext security. In: Boneh, D. (ed.) CRYPTO 2003. LNCS, vol. 2729, pp. 565–582. Springer, Heidelberg (2003)
Cathalo, J., Libert, B., Quisquater, J.-J.: Efficient and non-interactive timed-release encryption. In: Qing, S., Mao, W., López, J., Wang, G. (eds.) ICICS 2005. LNCS, vol. 3783, pp. 291–303. Springer, Heidelberg (2005), http://dx.doi.org/10.1007/11602897_25
Chalkias, K., Hristu-Varsakelis, D., Stephanides, G.: Improved anonymous timed-release encryption. In: Biskup, J., López, J. (eds.) ESORICS 2007. LNCS, vol. 4734, pp. 311–326. Springer, Heidelberg (2007), http://dx.doi.org/10.1007/978-3-540-74835-9_21
Cheon, J.H., Hopper, N., Kim, Y., Osipkov, I.: Provably secure timed-release public key encryption. ACM Trans. Inf. Syst. Secur. 11(2) (2008)
Chow, S.S.M., Yiu, S.M.: Timed-release encryption revisited. In: Baek, J., Bao, F., Chen, K., Lai, X. (eds.) ProvSec 2008. LNCS, vol. 5324, pp. 38–51. Springer, Heidelberg (2008)
Chu, C.-K., Weng, J., Chow, S.S.M., Zhou, J., Deng, R.H.: Conditional proxy broadcast re-encryption. In: Boyd, C., González Nieto, J. (eds.) ACISP 2009. LNCS, vol. 5594, pp. 327–342. Springer, Heidelberg (2009)
Cramer, R., Shoup, V.: Design and analysis of practical public-key encryption schemes secure against adaptive chosen ciphertext attack. IACR Cryptology ePrint Archive 2001, 108 (2001)
Delerablée, C.: Identity-based broadcast encryption with constant size ciphertexts and private keys. In: Kurosawa, K. (ed.) ASIACRYPT 2007. LNCS, vol. 4833, pp. 200–215. Springer, Heidelberg (2007)
Emura, K., Miyaji, A., Omote, K.: A timed-release proxy re-encryption scheme. IEICE Transactions 94-A(8), 1682–1695 (2011)
Fiat, A., Naor, M.: Broadcast encryption. In: Stinson, D.R. (ed.) CRYPTO 1993. LNCS, vol. 773, pp. 480–491. Springer, Heidelberg (1994)
Hanaoka, G., Kawai, Y., Kunihiro, N., Matsuda, T., Weng, J., Zhang, R., Zhao, Y.: Generic construction of chosen ciphertext secure proxy re-encryption. In: Dunkelman, O. (ed.) CT-RSA 2012. LNCS, vol. 7178, pp. 349–364. Springer, Heidelberg (2012)
Kikuchi, R., Fujioka, A., Okamoto, Y., Saito, T.: Strong security notions for timed-release public-key encryption revisited. In: Kim, H. (ed.) ICISC 2011. LNCS, vol. 7259, pp. 88–108. Springer, Heidelberg (2012)
Liang, K., Huang, Q., Schlegel, R., Wong, D.S., Tang, C.: A conditional proxy broadcast re-encryption scheme supporting timed-release (full paper). Cryptology ePrint Archive, http://eprint.iacr.org/
Libert, B., Vergnaud, D.: Unidirectional chosen-ciphertext secure proxy re-encryption. In: Cramer, R. (ed.) PKC 2008. LNCS, vol. 4939, pp. 360–379. Springer, Heidelberg (2008)
Matsuda, T., Nakai, Y., Matsuura, K.: Efficient generic constructions of timed-release encryption with pre-open capability. In: Joye, M., Miyaji, A., Otsuka, A. (eds.) Pairing 2010. LNCS, vol. 6487, pp. 225–245. Springer, Heidelberg (2010)
May, T.: Timed-release cryptography (February 1993), http://www.hks.net.cpunks/cpunks-0/1560.html (unpublished manuscript)
Nakai, Y., Matsuda, T., Kitada, W., Matsuura, K.: A generic construction of timed-release encryption with pre-open capability. In: Takagi, T., Mambo, M. (eds.) IWSEC 2009. LNCS, vol. 5824, pp. 53–70. Springer, Heidelberg (2009), http://dx.doi.org/10.1007/978-3-642-04846-3_5
Rivest, R.L., Shamir, A., Wagner, D.A.: Time-lock puzzles and timed-release crypto. Tech. rep., Cambridge, MA, USA (1996)
Author information
Authors and Affiliations
Editor information
Editors and Affiliations
Rights and permissions
Copyright information
© 2013 Springer-Verlag Berlin Heidelberg
About this paper
Cite this paper
Liang, K., Huang, Q., Schlegel, R., Wong, D.S., Tang, C. (2013). A Conditional Proxy Broadcast Re-Encryption Scheme Supporting Timed-Release. In: Deng, R.H., Feng, T. (eds) Information Security Practice and Experience. ISPEC 2013. Lecture Notes in Computer Science, vol 7863. Springer, Berlin, Heidelberg. https://doi.org/10.1007/978-3-642-38033-4_10
Download citation
DOI: https://doi.org/10.1007/978-3-642-38033-4_10
Publisher Name: Springer, Berlin, Heidelberg
Print ISBN: 978-3-642-38032-7
Online ISBN: 978-3-642-38033-4
eBook Packages: Computer ScienceComputer Science (R0)